KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The authors of the Mac malware known as Shlayer have successfully managed to get their malicious payloads through Apple’s automated notarizing process.
Since February 2020 all Mac software distributed outside of its Mac App Store must be notarized by Apple to be able to run on macOS Catalina and above.
The notarization process requires developers to submit software they built for the macOS platform to be scanned through Apple’s notary service, an automated system designed to scan submitted software for both malicious components and code-signing issues.
If they pass this automated security check, the apps are allowed by the macOS Gatekeeper — a macOS security feature that checks if downloaded apps have been checked for known malicious content — to run on the system.
As Apple describes this process, “[i]f there’s ever a problem with an app, Apple can quickly stop new installations and even block the app from launching again.”
Although the company says that notarizing macOS software is designed to give “users more confidence that the Developer ID-signed software you distribute has been checked by Apple for malicious components,” as discovered by Peter Dantini last week, Apple was tricked into notarizing Shlayer malware samples.
He discovered notarized Shlayer adware installers being distributed through a fake and malicious Homebrew website, installers that could be executed on any Mac running macOS Catalina without being automatically blocked on launch.
This allowed the threat actors behind this adware campaign to deliver their payloads to systems where the installers would have been previously blocked.
Security researcher Patrick Wardle confirmed that these installers were indeed delivering Shlayer adware samples notarized by Apple, which means that they can also infect users running the company’s latest macOS 11.0 Big Sur version.
Even worse, given that the samples had Apple’s seal of approval, users might trust them without thinking twice thus allowing the malware developers to spread their payloads to an even higher number of systems, dropping a persistent Bundlore adware variant on infected Macs.
After Wardle reported the notarized malware samples to Apple, the company reacted immediately and revoked the certificates (which means that they will automatically be prevented by Gatekeeper) the same day, on August 28.
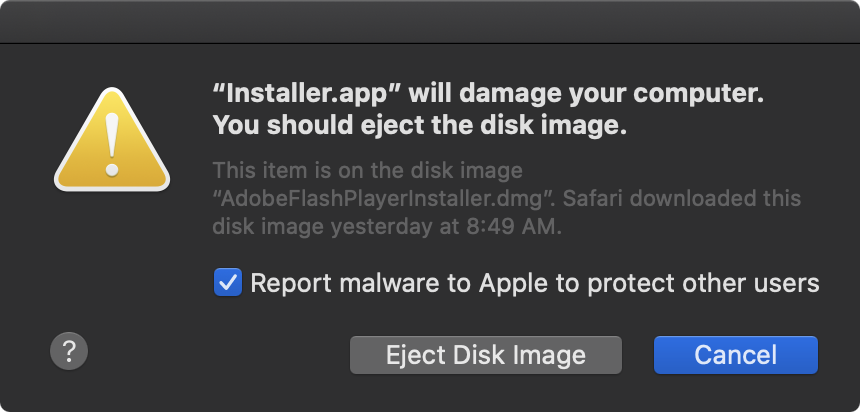
However, over the weekend, the researcher found that the Shlayer campaign was still going strong, serving new payloads notarized the day Apple revoked the initial sample’s certificates.
“Both the old and ‘new’ payload(s) appears to be nearly identical, containing OSX.Shlayer packaged with the Bundlore adware,” Wardle said.
“However the attackers’ ability to agilely continue their attack (with other notarized payloads) is noteworthy.
“Clearly, in the never-ending cat & mouse game between the attackers and Apple, the attackers are currently (still) winning.”
Also read: NDA Data Protection: The Importance, Its Meaning And Laws
Even though some Mac users think that malware only targets Windows and that Macs are virtually safe, Shlayer has been observed attacking over 10% of all Macs according to a Kaspersky report from January 2020.
Last year, a Shlayer variant was observed in the wild by Carbon Black’s Threat Analysis Unit while escalating privileges using a two-year-old technique and disabling Gatekeeper’s protection mechanism altogether to run unsigned second stage payloads.
Shlayer was first spotted by Intego’s research team while being distributed as part of a malware campaign in February 2018, disguised as a fake Adobe Flash Player installer just as many other malware families targeting the macOS platform.
Just as it did in the past, the newer malware versions are distributed as malicious Adobe Flash software update installers but, unlike the original ones which were pushed through torrent sites, Shlayer is now spreading via fake update pop-ups shown to potential victims on hijacked domains or clones of legitimate sites, or as part of far-reaching malvertising campaigns on legitimate websites.
After it infects a Mac, Shlayer will install the mitmdump proxy software and a trusted certificate so it can analyze and modify HTTPS traffic, allowing it to inject ads web pages, monitor the victims’ browser traffic, as well as to inject malicious scripts into visited sites.
To make things worse, this also allows the malware to analyze and alter all traffic, even encrypted traffic such as online banking and secure email.
Besides deploying the traffic monitoring proxy on compromised machines, Shlayer’s authors are currently only deploying adware as a secondary payload but they can switch payloads at any time to drop more dangerous malware strains like ransomware or wipers.
Also read: Intrusion Into Privacy All About Law And Legal Definition