KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Several Tibetan organizations were targeted in a cyber-espionage campaign by a state-backed hacking group using a malicious Firefox extension designed to hijack Gmail accounts and infect victims with malware.
The attacks coordinated by the TA413 Chinese-linked APT group started in January and continued throughout February, according to a Proofpoint report published on Thursday.
The Chinese state hackers also infected victims with the Scanbox malware reconnaissance framework, which allowed them to harvest their targets’ data and log their keystrokes.
“Scanbox has been used in numerous campaigns since 2014 to target the Tibetan Diaspora along with other ethnic minorities often targeted by groups aligned with the Chinese state interests,” Proofpoint said.
Also Read: The Importance Of DPIA And Its 3 Types Of Processing
“The tool is capable of tracking visitors to specific websites, performing keylogging, and collecting user data that can be leveraged in future intrusion attempts.”
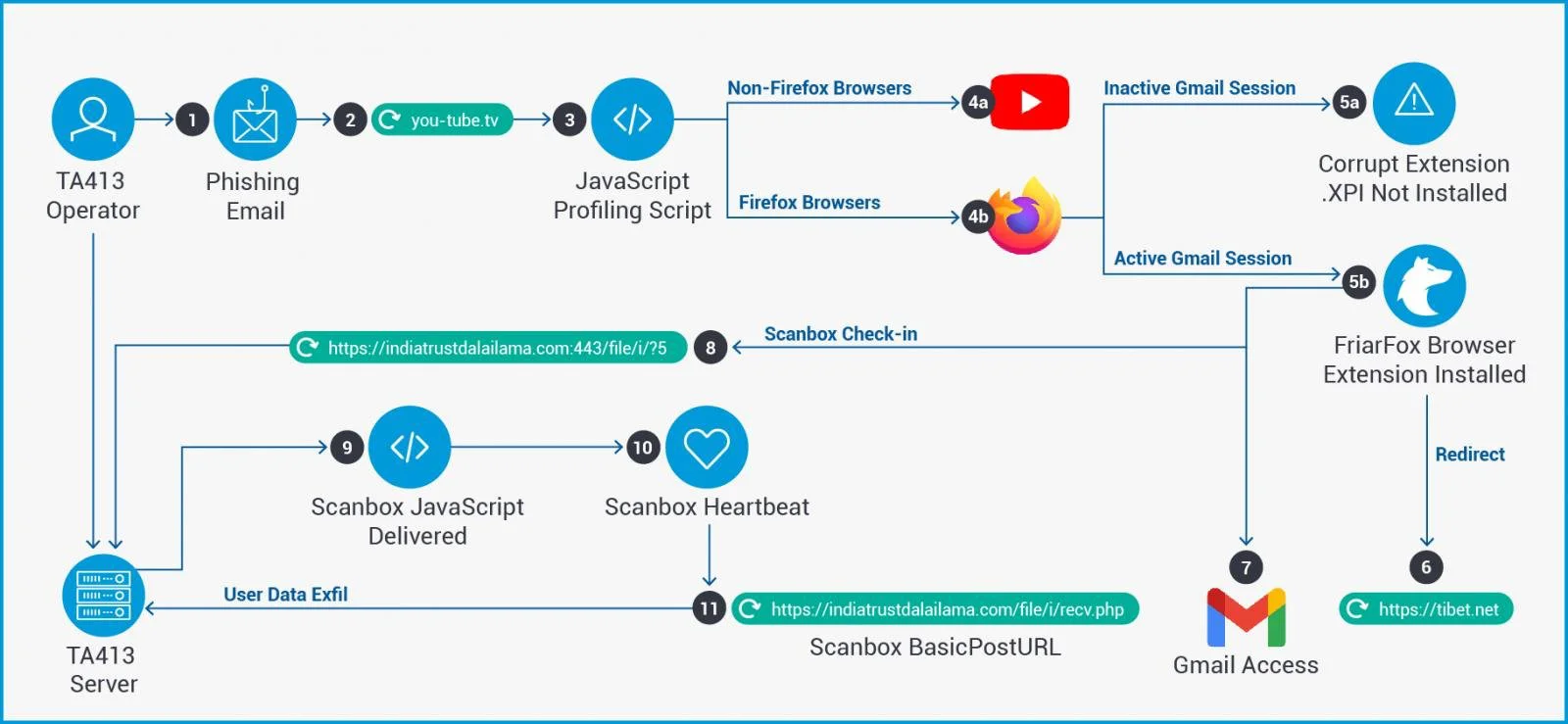
Phishing emails delivered by the TA413 attackers to their targets’ mailboxes redirected them to the attacker-controlled you-tube[.]tv domain that displays a fake Adobe Flash Player Update landing page.
JavaScript profiling scripts executed from this domain would automatically prompt the targets to install a malicious add-on named FriarFox if they were using the Firefox web browser and logged into their Gmail account.
If the potential victim used any other web browser, they would get redirected to the legitimate YouTube login page. If they were using Firefox but weren’t logged into a Gmail account, they’d be asked to add a corrupt FriarFox add-on to the browser, which would fail to install.
The FriarFox malicious extension is based on the open-source Gmail Notifier (restartless) Firefox add-on by changing its icon and metadata description to mimic a Flash update process.
They also added malicious JavaScripts designed to hijack the victims’ Gmail accounts and infect their systems with the Scanbox malware.
Once the victims get tricked into installing the FriarFox extension, TA413 operators take over the users’ Gmail account and Firefox browser to perform the following malicious actions:
Hijacked Gmail account:
Firefox (based on browser permissions):
“The use of browser extensions to target the private Gmail accounts of users combined with the delivery of Scanbox malware demonstrates the malleability of TA413 when targeting dissident communities,” Proofpoint concluded.
“These communities have a traditionally low barrier for compromise by threat actor groups and TA413 appears to be modulating their tools and techniques while continuing to rely on proven social engineering techniques.”
Also Read: Data Storage Security Standards: What Storage Professionals Need To Know
Further technical details and indicators of compromise (IOCs), including infrastructure and malware sample hashes used in this campaign, are available at the end of Proofpoint’s report.