KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Louis Vuitton has quietly patched a security vulnerability on its website that allowed for user account enumeration and even allowed account takeover via password resets.
Founded in 1854, Louis Vuitton is a prominent luxury French fashion brand and merchandise company with over 121,000 employees and a $15 billion annual revenue.
The easily exploitable flaw resided within the MyLV account section of the website.
Creating a MyLV account lets a Louis Vuitton shopper track online orders, access purchase history, obtain e-receipts, manage personal information, and receive company announcements.
Also Read: How To Check Data Breach And How Can We Prevent It
Having discovered the vulnerability, security researcher Sabri Haddouche reached out to Louis Vuitton as a part of the responsible disclosure process.
He then tweeted on September 22nd about his unsuccessful attempts to get through to the correct person when he received a vague response from the company.
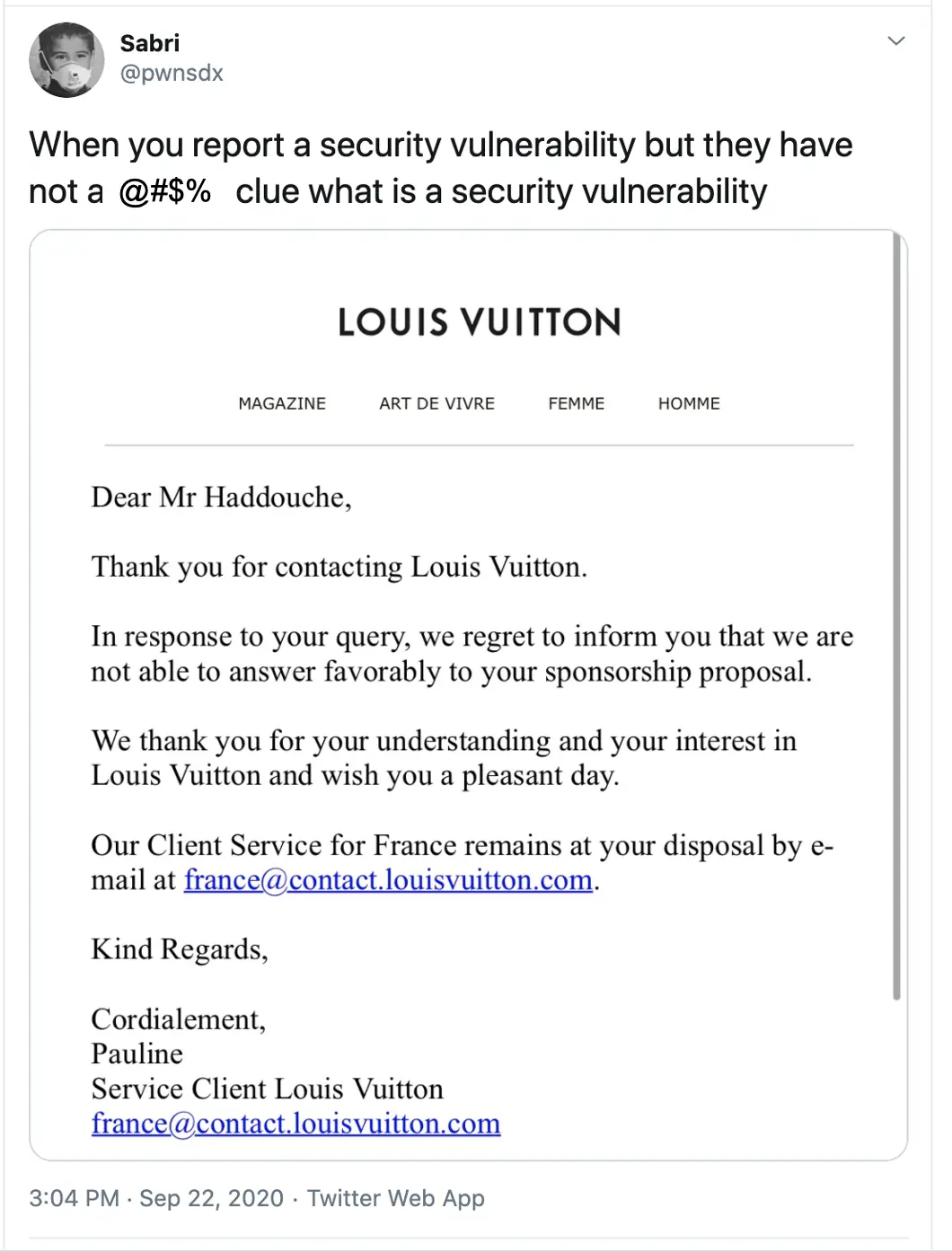
Haddouche continued in the same thread, “Well they said now that they forwarded the report to the related department so I’m going to wait for another week until I try to find a new way to contact them, maybe you can tell them there’s an urgent security issue that needs to be fixed and the support got the report.”
Haddouche has now shared with BleepingComputer more details about this urgent security issue that needed to be patched.
The researcher stated, “The vulnerability is surprisingly easy to exploit and I had found it by accident when clicking in one of the links in Louis Vuitton’s e-mail. Here is how it works:”
The e-mail Haddouche is referring to was an email notification about his repair from Louis Vuitton, which prompted him to login to an account.
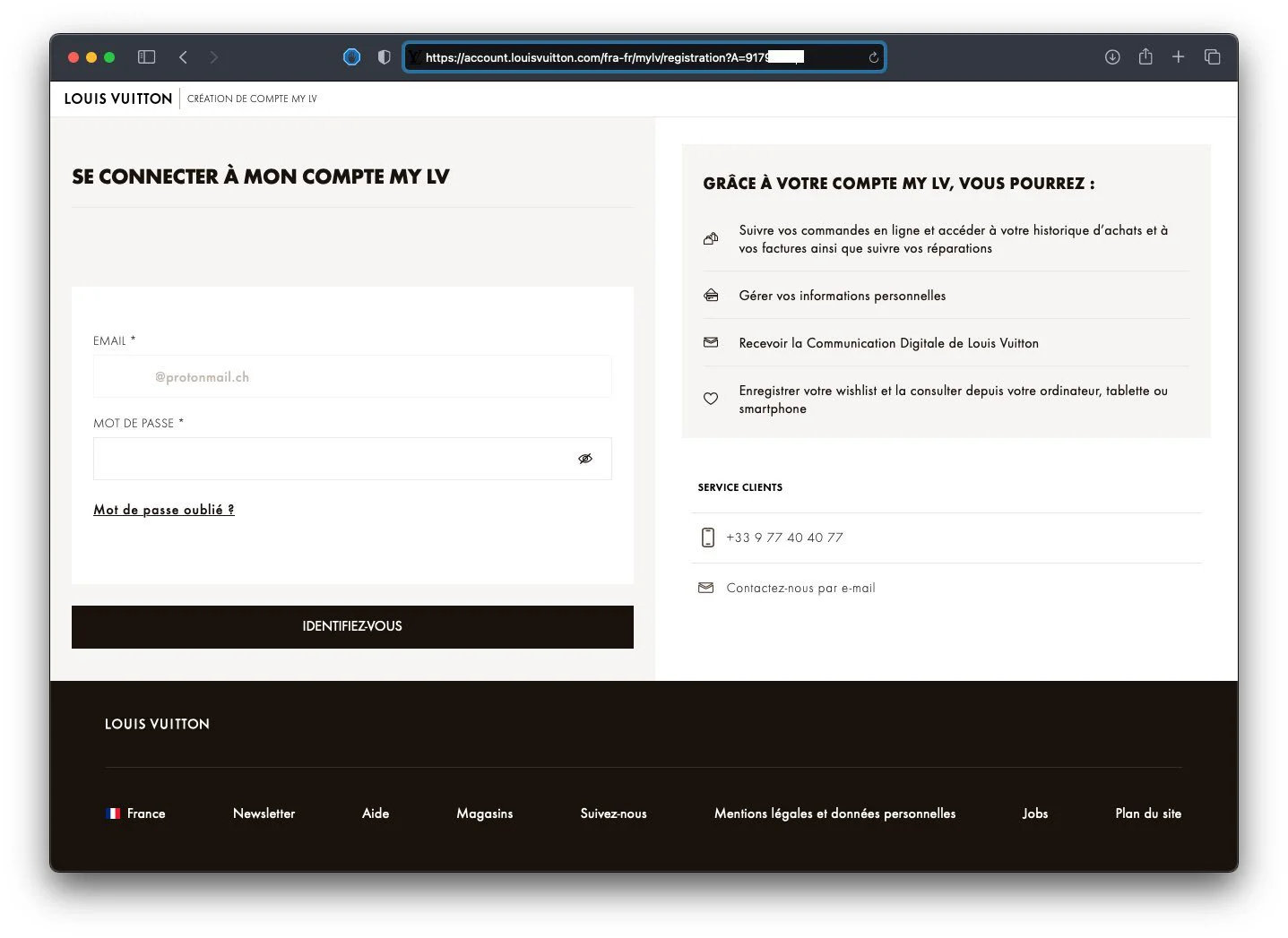
The “Consulter mon compte” (View my account) button leads to the MyLV link with Haddouche’s account ID, as shown in the steps above.
Haddouche noticed replacing his account ID number in the “A” parameter with a consecutive number now showed another user’s email address in the email field.
Also Read: 10 Government Data Leaks In Singapore: Prevent Cybersecurity
An attacker can potentially obtain email addresses of multiple Louis Vuitton’s members without their knowledge or consent by simply enumerating their account ID in the URL.
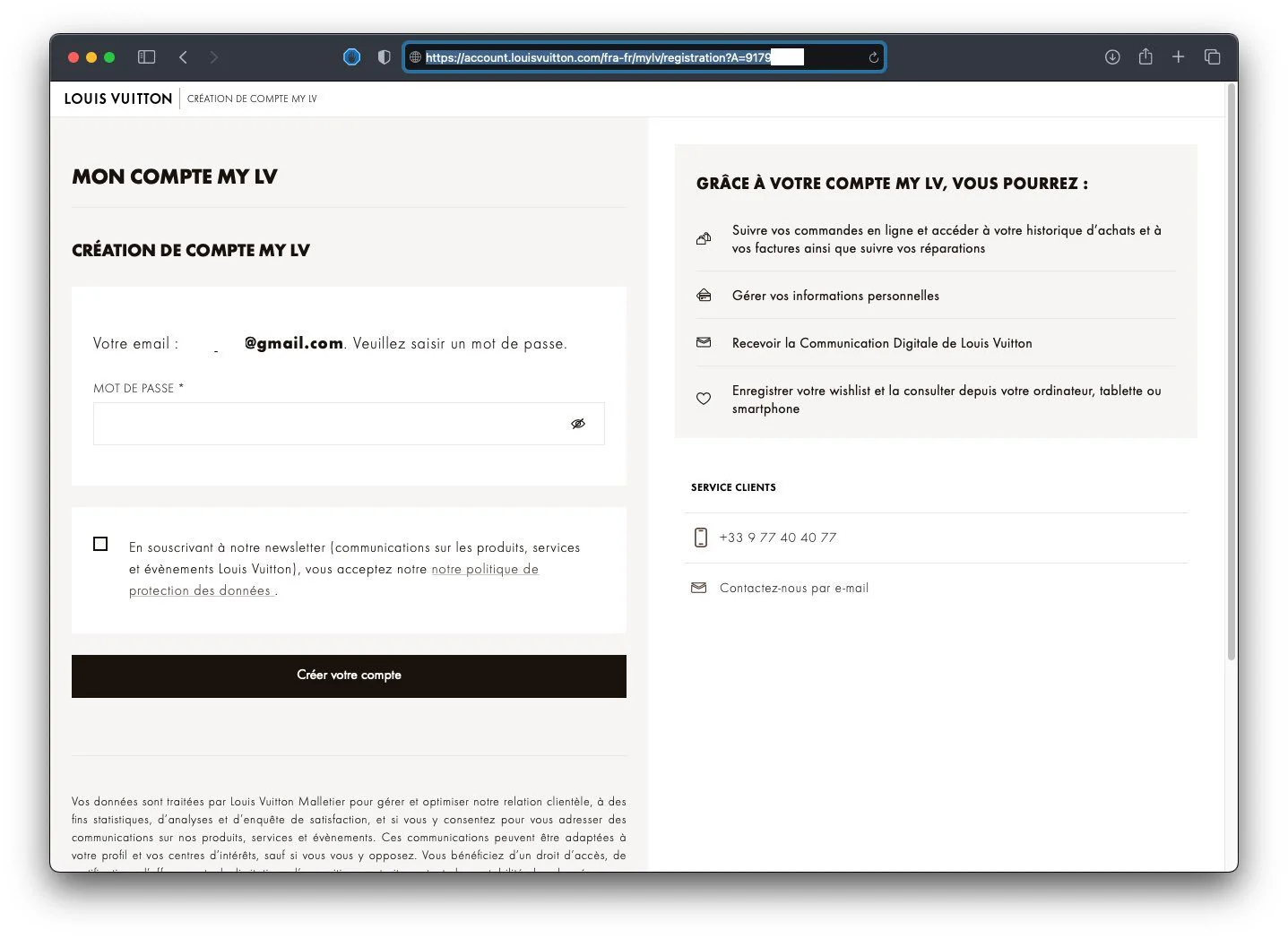
Another worrisome aspect of My LV account website is how it enabled anyone to takeover a Louis Vuitton member’s account.
Consider that a user had previously shopped on the website using their email address, but hadn’t signed up for an account.
Building on the above workflow, had a hacker come across such an email address in their course of guessing account IDs one by one, the website would not only expose the account’s email address but ask the hacker to set a password.
This could enable the attacker to create an account on behalf of the rightful user and set a password.
Recall, that a MyLV account grants access to personal information, online orders, access purchase history, e-receipts, and other sensitive bits.
Therefore, an account takeover via this flaw could’ve potentially exposed a user’s shopping history and data that should remain confidential.
Also Read: Basic Info On How Long To Keep Accounting Records In Singapore?
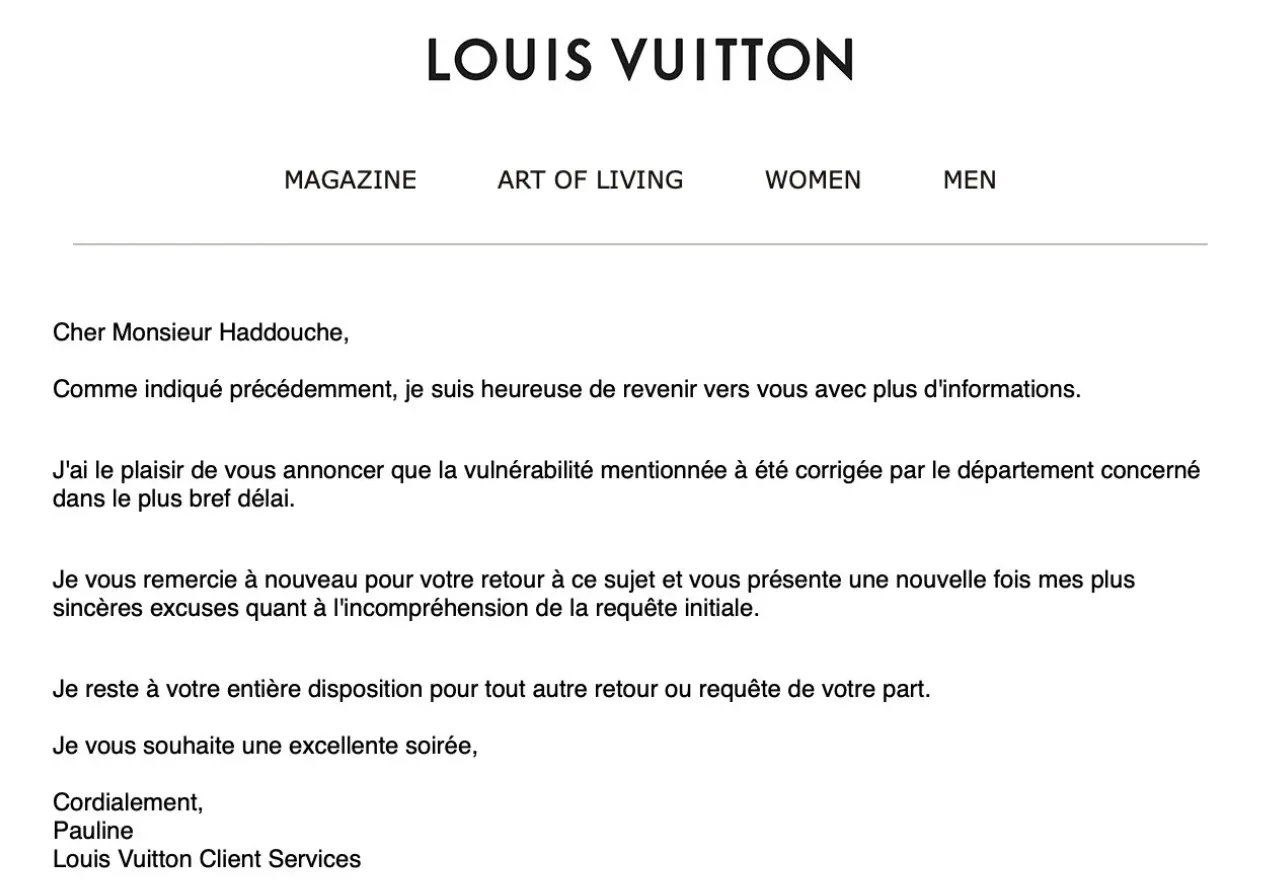
Today, Louis Vuitton has patched the flaw and as observed by BleepingComputer, the website no longer leaks arbitrary email addresses or allows account takeovers when navigating to the account creation URL in question.
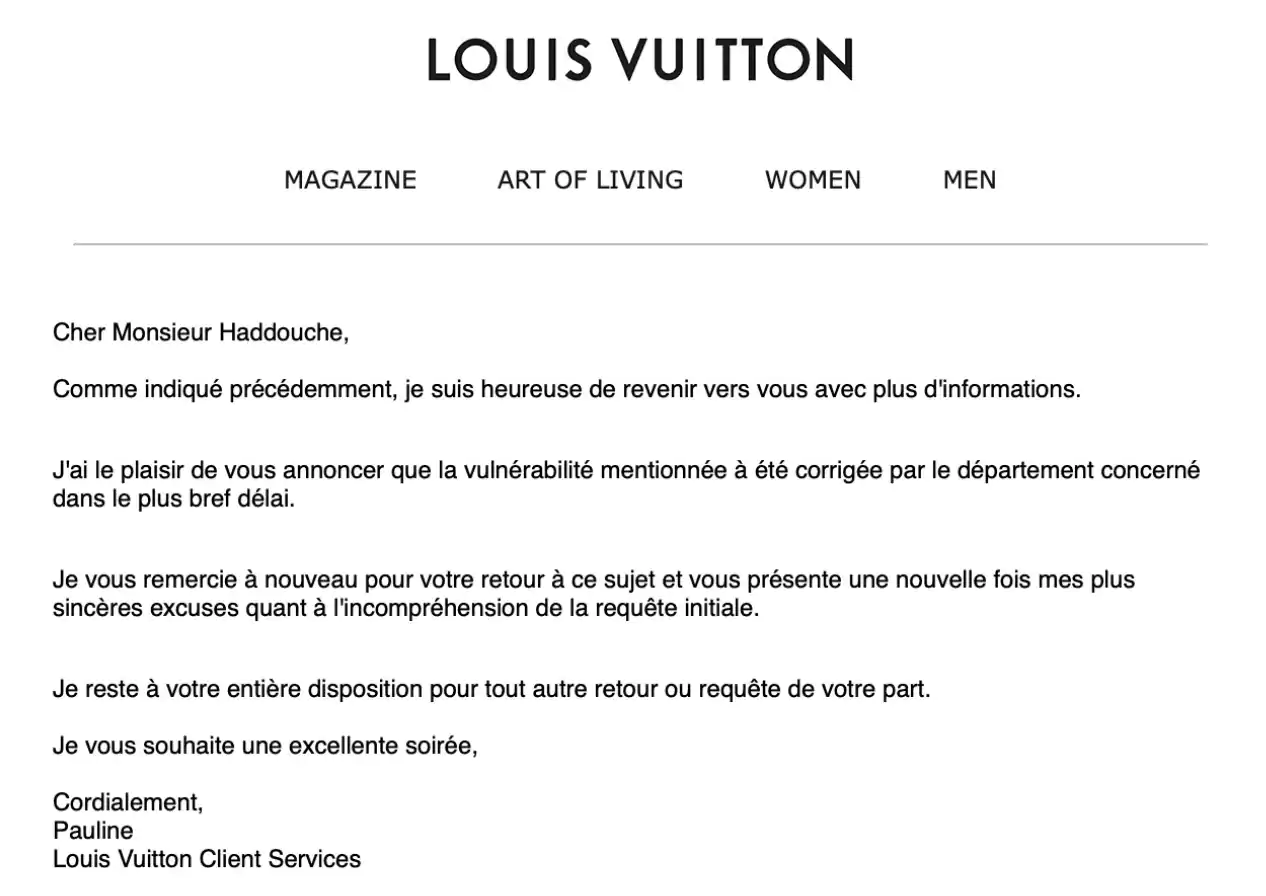
The company thanked the researcher for reporting the flaw in an email. A rough translation of the email shown below would be:
Dear Mr. Haddouche,
As mentioned before, I am happy to come back to you with more information.
I am pleased to announce that the mentioned vulnerability has been immediately fixed by the concerned department.
I thank you again for your feedback on this matter and once again offer my sincerest apologies for the misunderstanding of the initial request.
I remain at your disposal for any other return or request on your part.
I wish you an excellent evening,
Yours sincerely,
Pauline
Although Louis Vuitton does have a HackerOne bug bounty page, it does not seem to be actively used.
When asked, how could companies make it easier for researchers to report vulnerabilities, Haddouche told BleepingComputer:
“I would say that always have a dedicated email with PGP keys or a similar secure way for reporting security-related issues (YesWeHack bug bounty platform has PGP encryption in the background for each report) or like a dedicated Wire or Signal account for reporting security vulnerabilities, and publish them on your website or in a security.txt file because we basically lost 2 weeks and the vulnerability was already disclosed in my Twitter DMs and then in clear text per email during that time.”
“Anyone who has access to their mailbox, Twitter or my account would have been able to see the details of the vulnerability and make use of it,” he concluded.