KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Let’s Encrypt will begin revoking certain SSL/TLS certificates issued within the last 90 days due to a bug, starting January 28, 2022. The move could impact millions of active Let’s Encrypt certificates.
As a non-profit certificate authority run by Internet Security Research Group (ISRG), Let’s Encrypt provides X.509 certificates for Transport Layer Security encryption at no cost.
Also Read: CCTV Law Singapore Edition: Know Your Rights and Responsibilities
Yesterday, ISRG was informed by a third party who examined Let’s Encrypt’s Boulder code repo that there were “two irregularities” in the certificate authority’s implementation of “TLS using ALPN” validation method [1, 2].
Consequently, the certificate authority had to make two changes to how its TLS-ALPN-01 challenge validation works.
“All active certificates that were issued and validated with the TLS-ALPN-01 challenge before 00:48 UTC on 26 January 2022 when our fix was deployed are considered mis-issued,” explains Let’s Encrypt Site Reliability Engineer (SRE), Jillian.
To comply with Let’s Encrypt Certificate Policy, which requires the certificate authority to invalidate a Certificate within 5 days under certain conditions, the non-profit will begin revoking certificates at 16:00 UTC on January 28th, 2022.
Note, however, not all certificates are affected by the improper implementation of “TLS using ALPN” validation method. This planned revocation will only apply to certificates issued with the flawed TLS-ALPN-01 validation method.
“We estimate [less than] 1% of active certificates are affected. Subscribers affected by revocations will receive e-mail notifications if their ACME account contains a valid e-mail address. If you are affected by this revocation and need help renewing your certificate please ask questions in this thread,” further explains the engineer.
“We will be providing more details about this incident in the next few days.”
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
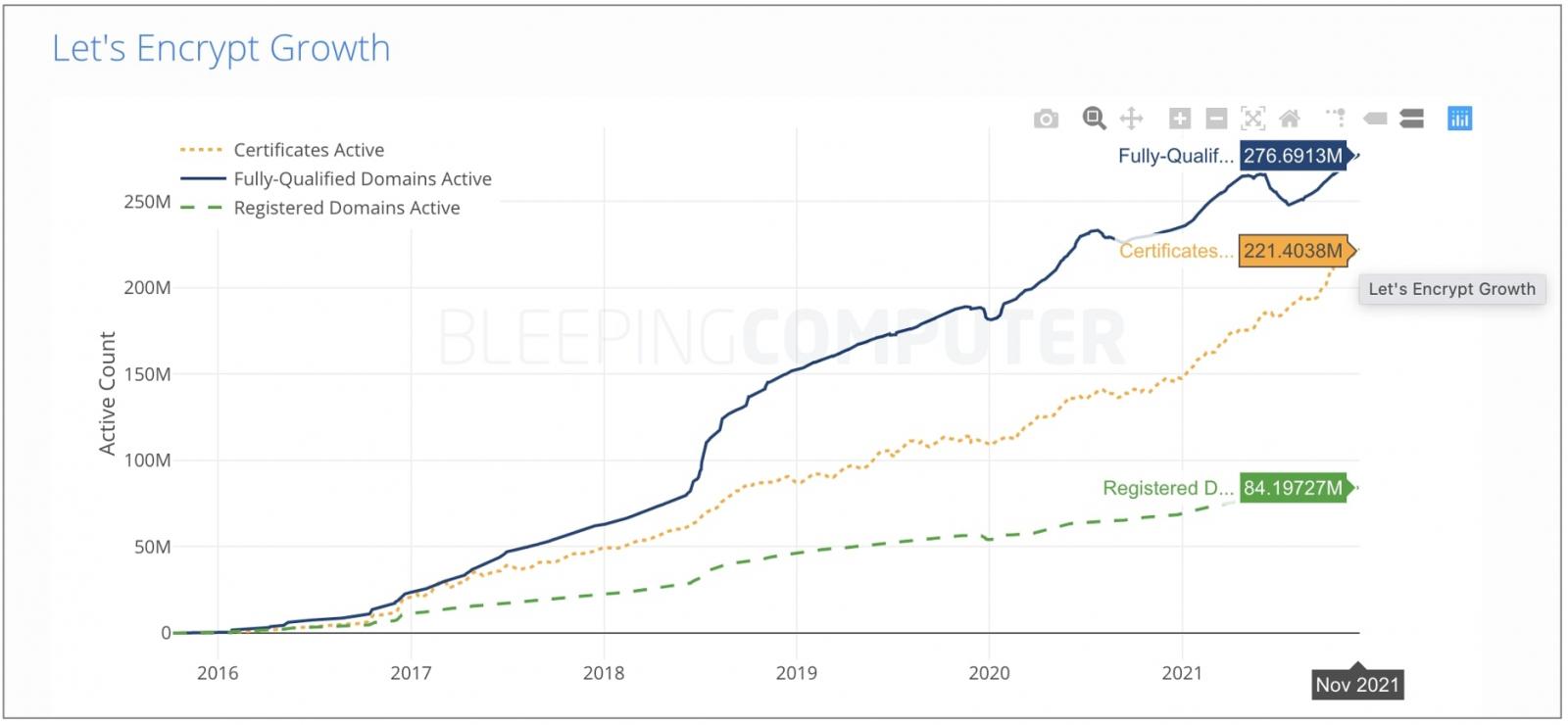
As of November 2021, the number of all active Let’s Encrypt certificates surpassed 221 million, as seen by BleepingComputer.
Therefore, the number of affected active certificates (1% or less) could possibly touch millions—if these were issued with the flawed TLS-ALPN-01 challenge validation.
Site owners with the affected Let’s Encrypt certificates are reporting receiving email notifications, instructing them to renew their certificates as the revocation is about to kick in.
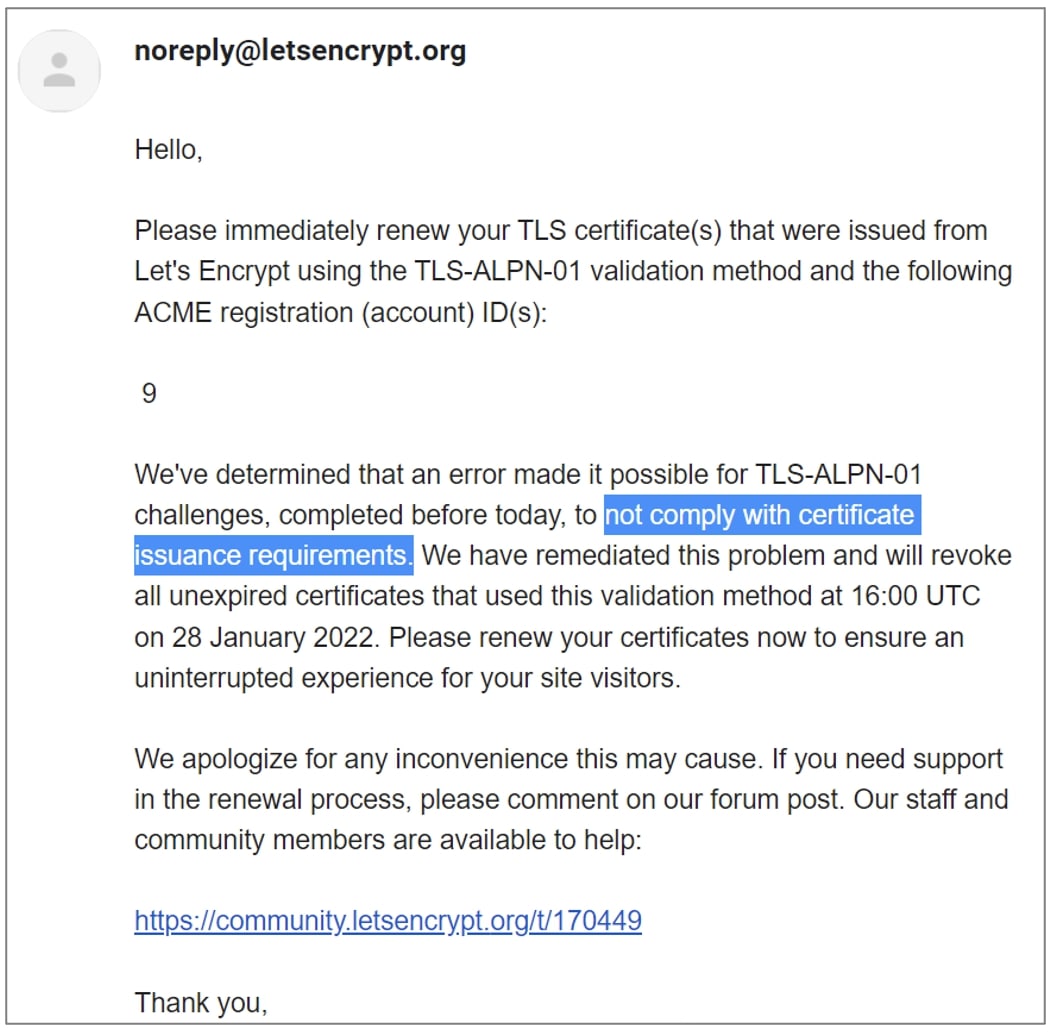
“If you received the e-mail, then your account has successfully obtained at least one certificate in the last 90 days that was validated using the TLS-ALPN-01 challenge,” explains Let’s Encrypt in the aforementioned thread.
“All certificates issued in the last 90 days and validated with TLS-ALPN-01 challenge are affected. You need to (force) renew the certificate according to your ACME client’s directions. If your client requires you to make a configuration change, please remember to revert after your certificate is renewed!”
In 2020, Let’s Encrypt had revoked millions of certificates after learning of another validation bug.
Given the short notice, not all users may be pleased with Let’s Encrypt’s sudden but necessary move.
On the bright side, though, those using automated certificate management solutions like Caddy Web Server can rest easy.
“Sites using Caddy v2.4.2 or newer should not have to take any action when automated certificates are revoked. Enjoy your sleep,” touts the team behind Caddy Web Server.
“Caddy automatically staples OCSP for all relevant certificates. It will refresh the staple about halfway through its validity period. If the next status is Revoked, Caddy will replace the certificate right away.”
Update, 1:54 PM ET: Added reference to another bug that had also led to the revocation of millions of Let’s Encrypt certificates in 2020.