KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The numerous law enforcement operations leading to the arrests and takedown of ransomware operations in 2021 have forced threat actors to narrow their targeting scope and maximize the efficiency of their operations.
Most of the notorious Ransomware-as-a-Service (RaaS) gangs continue their operations even after the law enforcement authorities have arrested key members but have refined their tactics for maximum impact.
According to an analysis published by Coveware, which looks at ransom negotiation data from Q4 2021, ransomware groups now demand higher ransom payments instead of increasing the volume of their attacks.
In numbers, the average ransom payment in Q4 2021 reached $322,168, which is 130% higher compared to the previous quarter. The median ransom payment amount was $117,116, up 63% compared to Q3.
Also Read: Domain spoofing: What is it and how to protect your business from it
.png)
Because disrupting the operation of large firms provokes investigations and creates political tensions on the international level, crooks are now striving for a delicate balance.
They target large enough firms to receive hefty ransom payment demands but not that big or critical that will cause them more geopolitical troubles than gains.
When looking at the company size in terms of employee count, entities with over 50,000 employees experienced fewer incidents as threat actors chose to focus more on mid-sized organizations.
.png)
“Although medium and large organizations continue to be impacted, ransomware remains a small business problem with 82% of attacks impacting organizations with less than one thousand employees,” explains Coveware
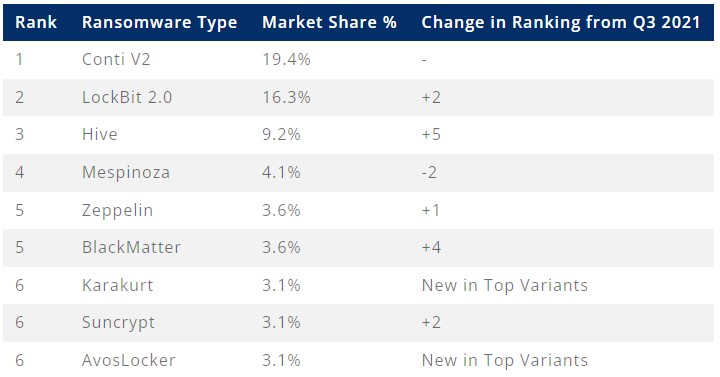
In Q4 2021, the most frequently encountered variant was Conti, accounting for 19.4% of all detections, LockBit 2.0 came second with 16.3%, and Hive third with 9.2%.
Also Read: How ransomware infects a system and ways to prepare against it
Considering that the top three ransomware operations engage in double-extortion tactics, it is no surprise that 84% of all attacks in Q4 2021 involved stolen data too.
This percentage would be even higher if it relied only upon the actors’ intentions, as in some cases, the attacks are detected and stopped by defense systems prematurely.
In terms of the techniques and procedures (TTPs), Coveware reports the following:
Another notable change in the tactics concerns the initial compromise vector. RDP access which used to be a widely-bartered item on dark web markets, is steadily dropping as ransomware actors turn to exploiting vulnerabilities.
.png)
The most exploited flaws for network entry in Q4 2021 were CVE-2021-34473, CVE-2021-26855, and CVE-2018-13379, on Microsoft Exchange and Fortinet firewall appliances.