KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A high-severity remote code execution flaw tracked as CVE-2021-45388 has been discovered in the KCodes NetUSB kernel module, used by millions of router devices from various vendors.
Successfully exploiting this flaw would allow a remote threat actor to execute code in the kernel, and although some restrictions apply, the impact is broad and could be severe.
The vulnerability discovery comes from researchers at SentinelLabs who shared their technical report with Bleeping Computer before publication.
Also Read: 5 Simple Instructions on How to Access Request Form PDF
Some router manufacturers include USB ports on devices, allowing users to share printers and USB drives on the network.
NetUSB is a kernel module connectivity solution developed by KCodes, allowing remote devices in a network to interact with the USB devices directly plugged into a router.
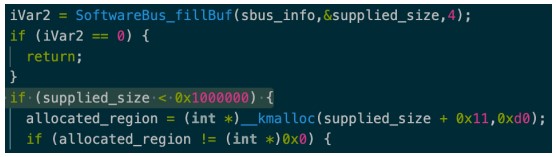
SentinelOne discovered a vulnerable code segment in the kernel module that doesn’t validate the size value of a kernel memory allocation call, resulting in an integer overflow.
The ‘SoftwareBus_fillBuf’ function may then use this new region for a malicious out-of-bounds write with data from a network socket under the attacker’s control.
Some limitations may make it difficult to exploit the vulnerability, as described below.
However, the vulnerable NetUSB module has a sixteen-second timeout to receive a request, allowing more flexibility when exploiting a device.
Also Read: Unsolicited Electronic Messages Act Means for Businesses
“While these restrictions make it difficult to write an exploit for this vulnerability, we believe that it isn’t impossible and so those with Wi-Fi routers may need to look for firmware updates for their router,” SentinelOne warned in their report.
The router vendors that use vulnerable NetUSB modules are Netgear, TP-Link, Tenda, EDiMAX, Dlink, and Western Digital.
It is unclear which models are affected by CVE-2021-45388, but it’s generally advisable to use actively supported products that receive regular security firmware updates.
Because the vulnerability affects so many vendors, Sentinel One alerted KCodes first, on September 9, 2021, and provided a PoC (proof of concept) script on October 4, 2021, to verify the patch released that day.
Vendors were contacted in November, and a firmware update was scheduled for December 20, 2021.
Netgear released a security update to patch CVE-2021-45388 on affected and supported products on December 14, 2021.
According to the security advisory published on December 20, 2021, the affected Netgear products are the following:
The solution implemented by Netgear was to add a new size check to the ‘supplied size’ function, preventing the out-of-bounds write.
Bleeping Computer has contacted all affected vendors to request a comment on the timeline of releasing a firmware update, but we haven’t received a response yet.