KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An Iranian-backed hacker group has been observed while seeking to sell access to compromised corporate networks to other threat actors on underground forums and attempting to exploit F5 BIG-IP devices vulnerable to CVE-2020-5902 exploits.
The Iranian hackers have been active since at least 2017 and are being tracked as Pioneer Kitten by cyber-security firm Crowdstrike, as Fox Kitten [1, 2] by threat intelligence firm ClearSky, and as Parisite [1, 2] by ICS security firm Dragos.
“This adversary appears to be primarily focused on gaining and maintaining access to entities possessing sensitive information of likely intelligence interest to the Iranian government,” CrowdStrike says in a report published earlier today.
As detailed by Dragos security researchers, the hacking group is known for exploiting vulnerabilities in Internet-exposed Fortinet (CVE-2018-13379), PulseSecure (CVE 2019-11510, CVE 2019-11539) [1, 2] , Citrix ADC/Gateway (CVE 2019-19781) and Palo Alto Networks VPN (CVE-2019-1579) appliances to gain access to companies’ corporate and industrial networks.
Even more recently, starting with early July when F5 patched a critical remote code execution (RCE) vulnerability in the BIG-IP application delivery controller (ADC), Pioneer Kitten has immediately switched tools to target enterprises that haven’t patched their BIG-IP devices.
Successful exploitation of this flaw allows the hackers to fully compromise vulnerable systems, as well as to intercept controller application traffic and to move laterally other targets on the victims’ internal network.
This activity lines up with an August FBI Private Industry Notification warning of Iranian hackers attempting to compromise vulnerable Big-IP ADC devices since early July 2020.
Also read: The Importance Of DPIA And Its 3 Types Of Processing
Pioneer Kitten was previously observed while providing initial network access to other Iranian-sponsored hacking groups including APT33 (Magnallium, Elfin), APT39 (Chafer, Remix Kitten), and APT34 (Helix Kitten, OilRig).
According to CrowdStrike, a Pioneer Kitten actor has also been spotted during July 2020 while trying to sell to access to the networks of such previously compromised companies to other hackers.
“That activity is suggestive of a potential attempt at revenue stream diversification on the part of PIONEER KITTEN, alongside its targeted intrusions in support of the Iranian government,” CrowdStrike explains.
Pioneer Kitten’s targeting behavior seems to be highly opportunistic according to CrowdStrike’s analysis, with their targets including entities from a long list of countries including the U.S., Israel, Germany, Australia, France, Austria, Finland, Hungary, Italy, Kuwait, Lebanon, Malaysia, Poland, Saudi Arabia, and UAE.
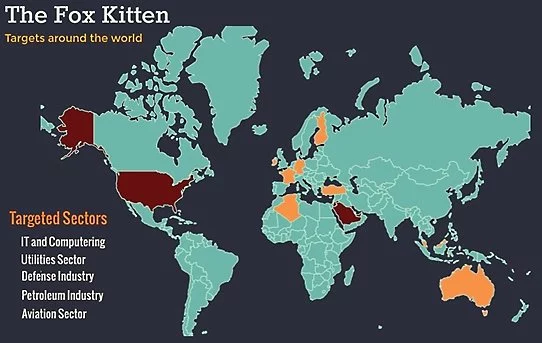
The targeted sectors also cover a wide range of industry verticals including “technology, government, defense, healthcare, aviation, media, academic, engineering, consulting and professional services, chemical, manufacturing, financial services, insurance, and retail.”
However, their attacks are mostly focused on technology, government, defense, and healthcare organizations, and centered on North American and Israeli targets.
Based on behavioral indicators and other characteristics, CrowdStrike says that the group is “a contract element operating in support of the Iranian government” instead of a hacking group directly controlled by the Iranian government.
Also read: 10 Principles On How To Build A Good Governance Model