KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new iPhone bug has come to light that breaks your iPhone’s wireless functionality by merely connecting to a specific WiFi hotspot.
Once triggered, the bug would render your iPhone unable to establish a WiFi connection, even if it is rebooted or the WiFi hotspot is renamed.
A bug like this could be exploited by malicious actors planting rogue WiFi hotspots in popular areas to bork iPhone devices connecting to them.
This week, reverse engineer Carl Schou ran into an issue when connecting to his personal WiFi hotspot named:%p%s%s%s%s%n
On connecting to the hotspot, his iPhone’s WiFi would be disabled, and every time he tried to enable it again, it would quickly turn off, even if he restarted the device or the hotspot name was changed:
“After joining my personal WiFi with the SSID ‘%p%s%s%s%s%n’, my iPhone permanently disabled it’s WiFi functionality. Neither rebooting nor changing SSID fixes it :~),” tweeted Schou.
Schou told BleepingComputer that his experiment worked successfully on an iPhone XS, running iOS version 14.4.2.
Tests conducted by BleepingComputer on an iPhone running iOS 14.6 confirm an iPhone’s wireless functionality would break after connecting to the strangely named wireless network.
Also Read: How to Secure Your WiFi Camera: 4 Points to Consider
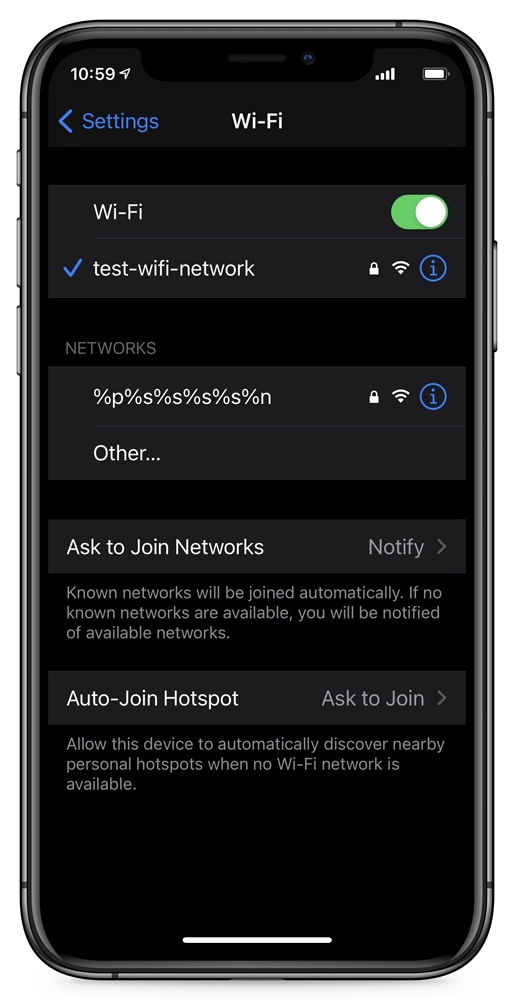
In multiple tests attempting to connect to this strange SSID, our Wi-Fi settings would begin to function erratically, but all led to the same behavior – the breaking of our iPhone’s wireless connectivity.
In some tests, connecting to the SSID would fail, but we could no longer access our regular wireless network.
Other tests led to the behavior described by Schou, where the iPhones Wi-Fi setting would be disabled, and we could no longer enable it again, as shown below.

The only way to fix our iPhone’s broken Wi-Fi feature was to reset the device’s iPhone network settings, which we describe how to do at the end of the article.
A bug like this is serious, considering malicious actors could plant rogue WiFi hotspots (needing no password) in popular areas to bork iPhone devices that connect to them.
According to users, the issue is unique to iPhones and does not appear to be reproducible on Android devices:
Other security researchers who saw Schou’s tweet believe that an input parsing issue likely causes this bug.
When a string with “%” signs exists in WiFi hotspot names, iOS may be mistakenly interpreting the letters following “%” as string-format specifiers when they are not.
In C and C-style languages, string format specifiers have a special meaning and are processed by the language compiler as a variable name or a command rather than just text.
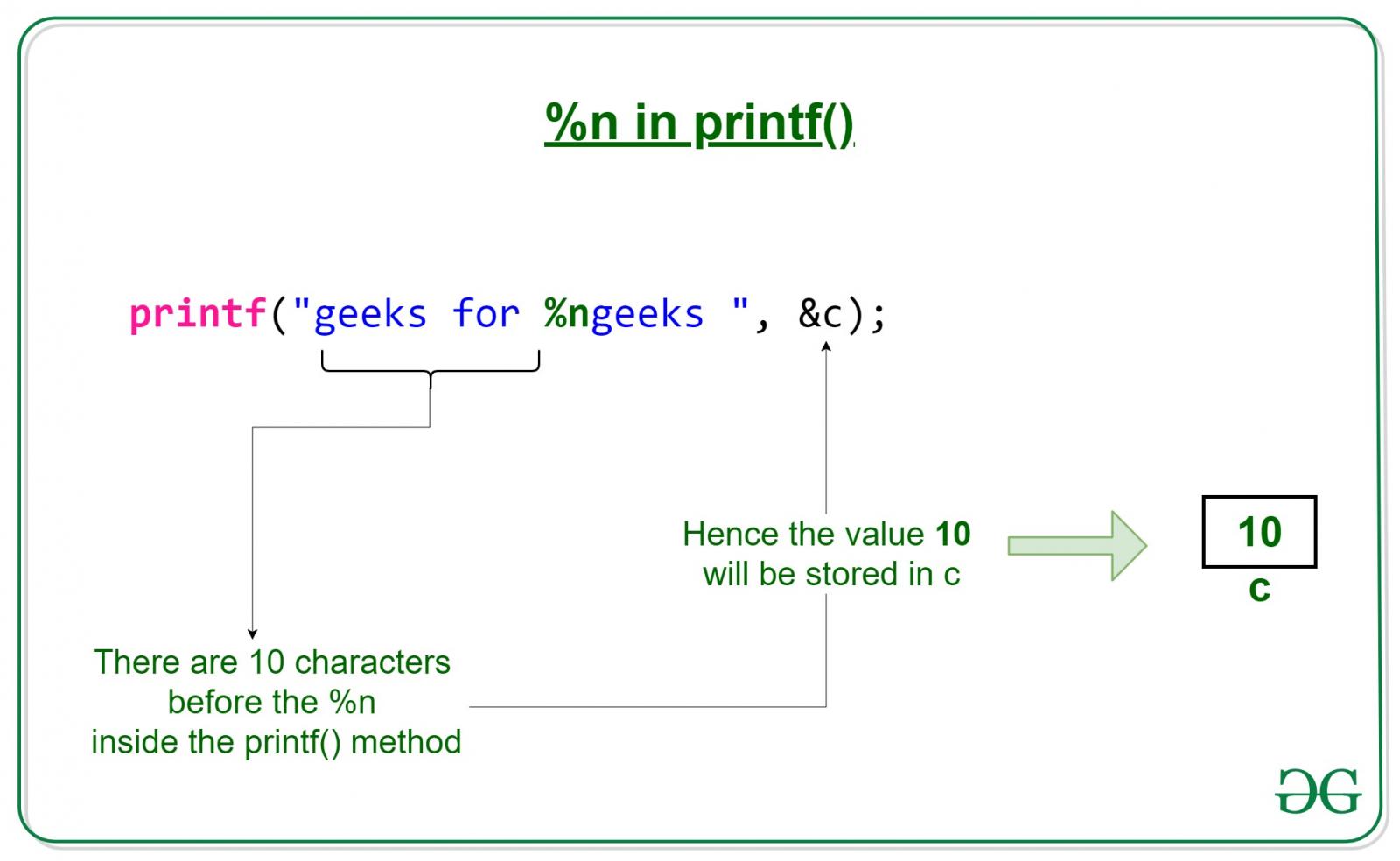
For example, the following printf command does not actually print the “%n” character but stores the number of characters (10) preceding %n into the variable “c.”
The “%n” is merely a format specifier and not an actual text string. As such, the output of the following line will simply be “geeks for geeks,” with no mention of “%n.”printf(“geeks for %ngeeks “, &c);
Some users have claimed previously inserting the relatively innocuous “%x” format specifiers in their WiFi SSID to avoid causing major issues for unsuspecting WiFi users.
When asked what was his motivation to name his WiFi hotspot with the funky string specifiers, the reverse engineer said:
“All my devices are named after format strings to f*** with poorly developed devices,” Schou told BleepingComputer.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
Although restarting your iPhone won’t fix the issue, this bug is not permanent and can be fixed without resetting your entire device.
Instead, you can follow these simple steps to reset your iOS network settings to resolve the issue:
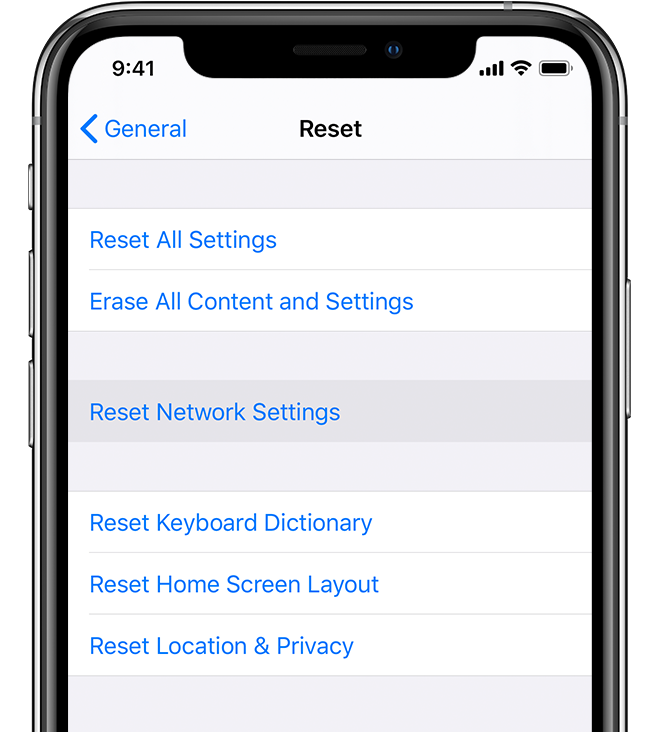 Resetting network settings on an iPhone (Apple)
Resetting network settings on an iPhone (Apple)BleepingComputer has reached out to Apple for comment before publishing, and we are awaiting their response.