KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







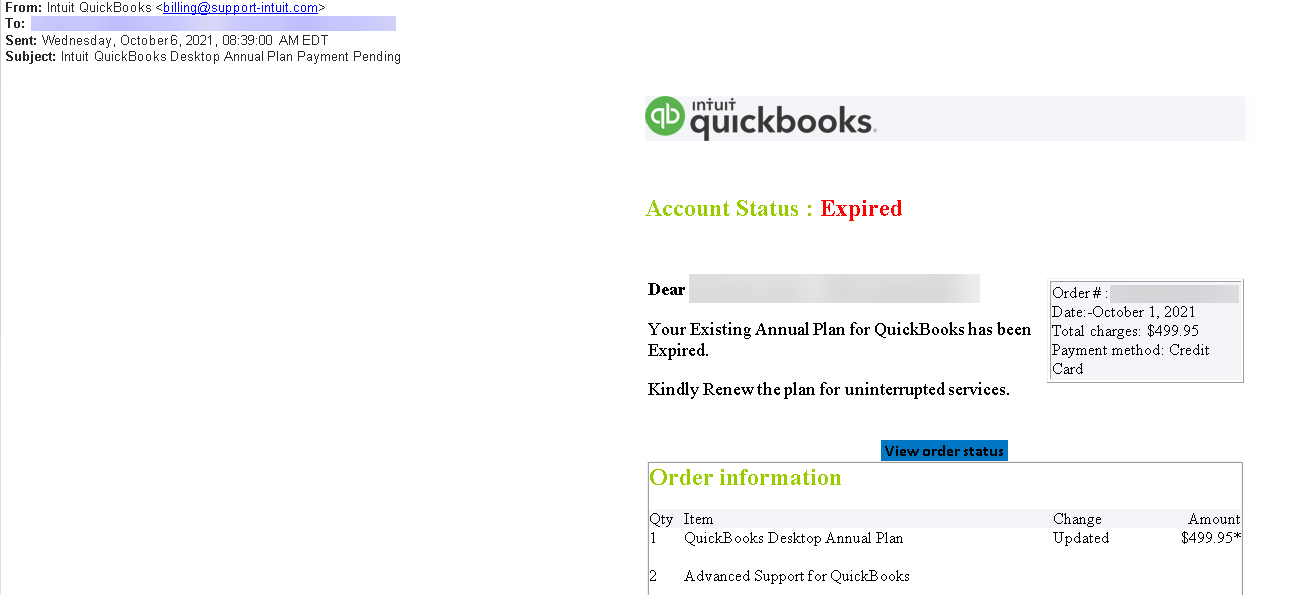
Intuit has warned QuickBooks customers that they are targeted by an ongoing phishing campaign impersonating the company and trying to lure potential victims with fake renewal charges.
The company said it received reports from customers that they were emailed and told that their QuickBooks plans had expired.
“This email did not come from Intuit. The sender is not associated with Intuit, is not an authorized agent of Intuit, nor is their use of Intuit’s brands authorized by Intuit,” Intuit explained.
The financial software firm advises all customers who received one of these phishing messages not to click any links embedded in the emails or open attachments.
Also Read: Buying a Paper Shredder Singapore: 5 Important Factors to Consider
The recommended way to deal with them is to delete them to avoid being infected with malware or redirected to a phishing landing page designed to harvest credentials.
Customers who have already opened attachments or clicked links in the phishing emails should:
Intuit also provides information on how customers can protect themselves from phishing attempts on its support website.
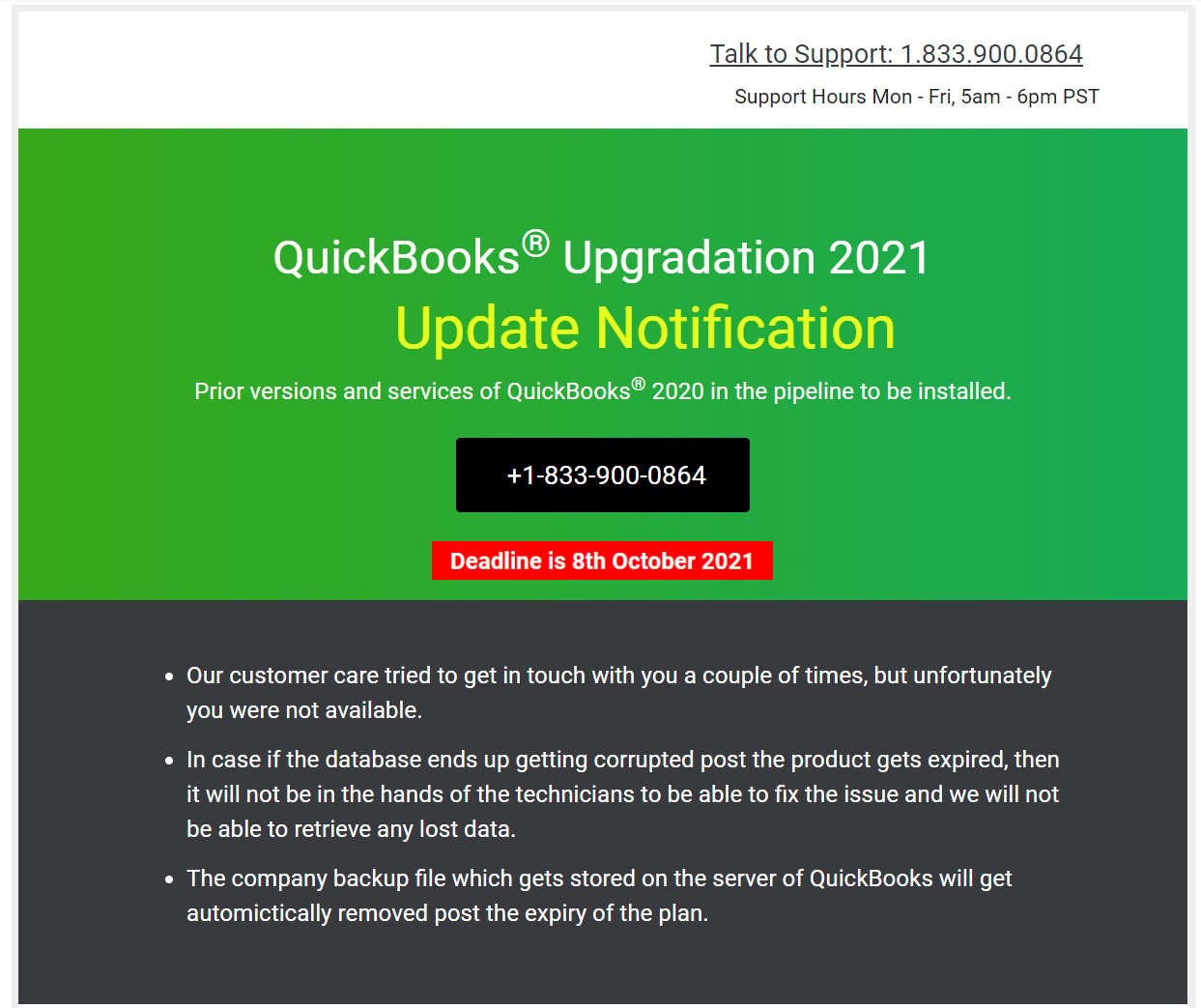
In July, Intuit also alerted its customers of phishing emails, asking them to call a phone number to upgrade to QuickBooks 2021 until the end of the month to avoid having their databases corrupted or company backup files removed automatically.
BleepingComputer found similar emails sent to Intuit customers this month, using a very similar template with the upgrade deadline changed to the end of October.
While Intuit didn’t explain how the upgrade scheme worked, from BleepingComputer’s previous encounters with similar scam attempts, the scammers will attempt to take over the callers’ QuickBooks accounts.
To do that, they ask the victims to install remote access software like TeamViewer or AnyDesk while posing as QuickBooks support staff.
Also Read: Letter of Consent MOM: Getting the Details Right
Next, they connect and ask the victims to provide the information needed to reset their QuickBooks password and take over their accounts to siphon their money by making payments in their names.
If the victims also have two-factor authentication enabled, the scammers will ask for the one-time authorization code they need to go ahead with the upgrade.
Besides these two active campaigns, Intuit is also being impersonated by other threat actors in a fake copyright phishing scam, as SlickRockWeb CEO Eric Ellason said today.
Recipients targeted by these emails risk infecting themselves with the Hancitor (aka Chanitor) malware downloader or have Cobalt Strike beacons deployed on their systems.
The embedded links send the potential victims through advanced redirection chains using various security evasion tactics and victim fingerprinting malspam.
In June, Intuit also notified TurboTax customers that some of their personal and financial info was accessed by attackers following a series of account takeover attacks. The company also said that that was not a “systemic data breach of Intuit.”
The company’s investigation revealed that the attackers used credentials obtained from “a non-Intuit source” to access the customers’ accounts and their name, Social Security number, address(es), date of birth, driver’s license number, financial information, and more.
TurboTax customers were targeted in at least three other account takeover attack campaigns in 2014/2015 and 2019.