KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Technical details about a high-severity vulnerability in Facebook’s Instagram app for Android and iOS show how an attacker could exploit it to deny user access to the app, take full control of their account, or use their mobile device to spy on them.
To trigger the bug, an attacker had only to send the target a specially crafted image via a common messaging platform or over email.
The issue was in the way Instagram parsed images, so as long as the app could access it to show it as options for a post, the vulnerability would set off allowing dangerous actions.
Also Read: The Importance of DPIA And Its 3 Types Of Processing
Technically, the vulnerability is a heap buffer overflow (CVE-2020-1895) occurring when Instagram tried to upload a larger image believing it to be smaller.
Facebook fixed the problem in spring, following responsible disclosure from cybersecurity company Check Point, and issued a vague security advisory for it.
In a detailed technical report today, Gal Elbaz from Check Point highlights how custom implementation of third-party code in Instagram could have led to serious, remote code execution risks.
The weak point, in this case, was a hardcoded constant value that Instagram developers added when integrating Mozjpeg, an open-source JPEG encoder that Mozilla forked from libjpeg-turbo better compression of JPEG images.
Check Point started checking Mozjpeg for potential flaws that could be exploited in a meaningful way. The purpose was to learn if Instagram could be impacted through the library so the researchers focused on the app integrated Mozjpeg.
They found that the function handling image sizes when parsing JPEG images had an error that caused memory allocation problems (integer overflow) during the decompression process.
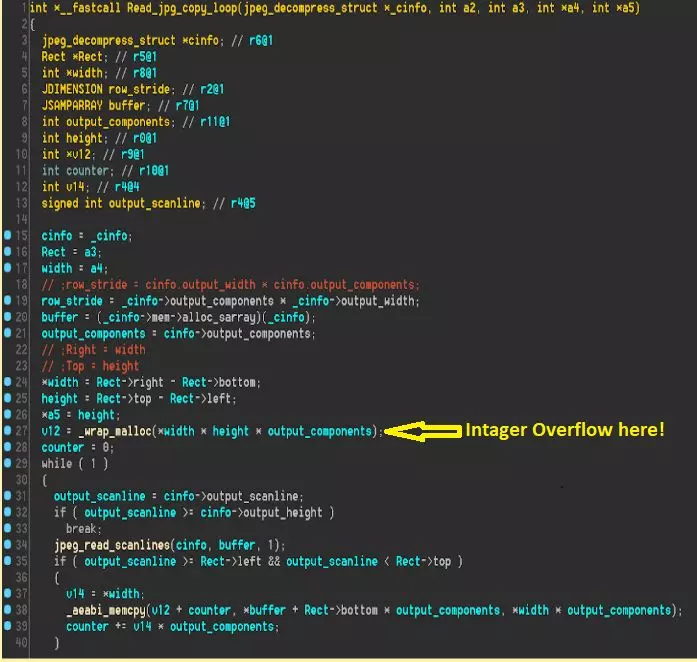
This could be used to to corrupt memory, which may come with dangerous implications. At best, this type of bug could crash Instagram but, if exploitable, it may lead to critical risks.
As Elbaz explains, triggering the vulnerability requires specifying a size larger than 2^32 bytes. In simpler terms, Check Point told BleepingComputer:
“Technically speaking, the issue itself was a buffer overflow and it is caused by sending a picture with a large size, while fooling the application into believing it’s much smaller. This causes an overwrite and let us do our magic” – Check Point
With an image crafted this way, an attacker may have been able to “steal” Instagram’s execution flow and make it run code within its context and permissions.
As Check Point told us, Instagram has extensive permissions on the device, which include access to contacts, storage, device location, camera, and microphone.
Apart from controlling the device owner’s Instagram profile, an attacker could also use the device as an effective spying tool without raising any suspicion.
Also Read: Data Storage Security Standards: What Storage Professionals Need To Know
A possible scenario from an attacker with skills to exploit the glitch could be as follows:
While this chain of events is possible, Check Point never got to discover all the possibilities stemming from exploiting this vulnerability, although they had more avenues to explore. Facebook patching the bug put an end to these efforts.
When informing Check Point about fixing the issue, a Facebook representative said that they did not see “any evidence of abuse.”