KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







High-severity and critical vulnerabilities collectively referred to as INFRA:HALT are affecting all versions of NicheStack below 4.3, a proprietary TCP/IP stack used by at least 200 industrial automation vendors, many in the leading segment of the market.
The stack is commonly found on real-time operating systems (RTOS) powering operational technology (OT) and industrial control system (ICS) devices to provide internet and network functionality.
INFRA:HALT is a set of 14 vulnerabilities jointly discovered by Forescout Research Labs and JFrog Security Research. It is part of Forescout’s Project Memoria Research (Amnesia:33, NUMBER:JACK, NAME:WRECK) that focuses on the security of TCP/IP stacks.
The bugs range from remote code execution, denial of service (DoS), and information leak to TCP spoofing and DNS cache poisoning.
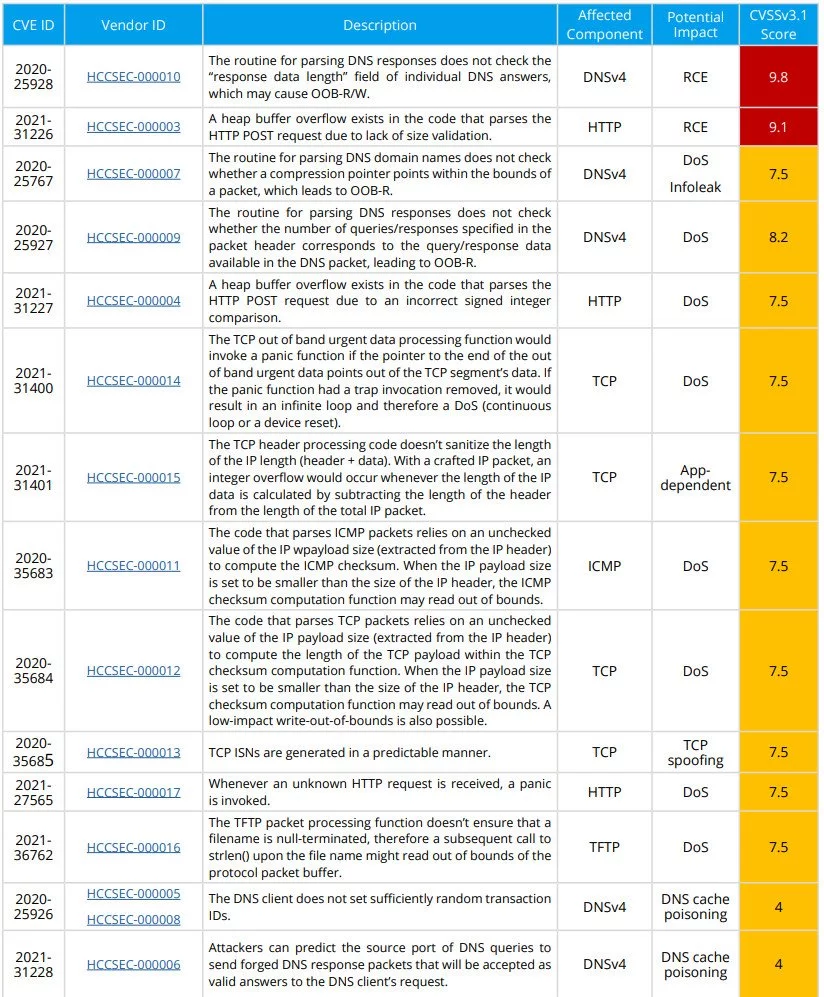
Most are high-severity security issues, but two of them – CVE-2020-25928 and CVE-2020-31226 – are deemed critical. Forescout researchers assessed their severity score at 9.8 and 9.1, respectively.
They impact the DNS client and the HTTP server components of the stack, allowing a remote attacker to execute code on the vulnerable device to take full control over it.
To trigger CVE-2020-25928, an attacker would need to send a crafted DNS packet as a response to a DNS query from the vulnerable device, Forescout and JFrog researchers explain in a joint technical report published earlier today.
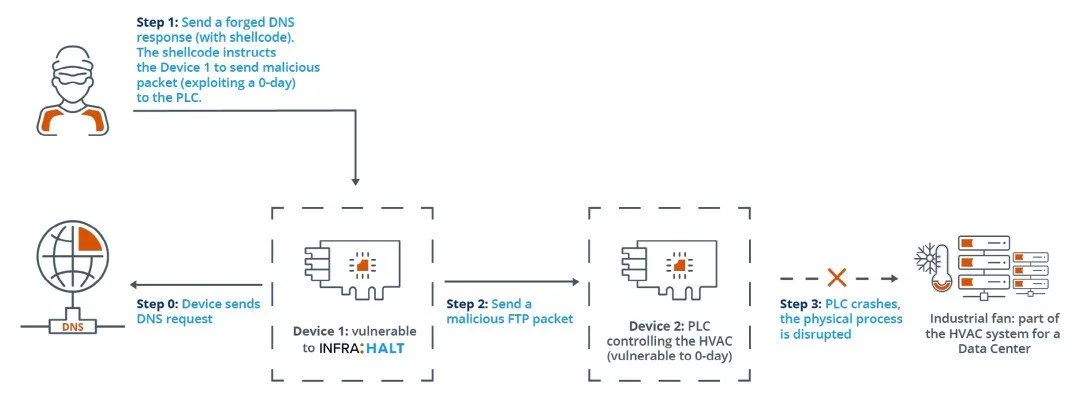
Stanislav Dashevskyi, one of the Forescout researchers that investigated the INFRA:HALT collection of vulnerabilities, demonstrated CVE-2020-25928 in a video by attacking the programmable logical controller (PLC) managing an industrial fan.
Not long after initiating the attack, the PLC could no longer activate the fan and needed a restart to regain control over the fan.
The attack requires only four steps to crash the PLC:
Also Read: 4 Reasons Why You Need an Actively Scanning Antivirus Software
Of the 14 INFRA:HALT vulnerabilities, ten have been rated with a high-severity score, two are low severity and two are critical:
NicheStack, also known as InterNiches, is maintained by HCC Embedded. The library is present in devices from around 200 vendors. An old website version from the company lists big names among its customers: Emerson, Honeywell, Mitsubishi Electric, Rockwell Automation, Schneider Electric, and Siemens.
A search on Shodan on March 8 revealed that more than 6,400 devices running a vulnerable version of the stack. The number is likely lower today.
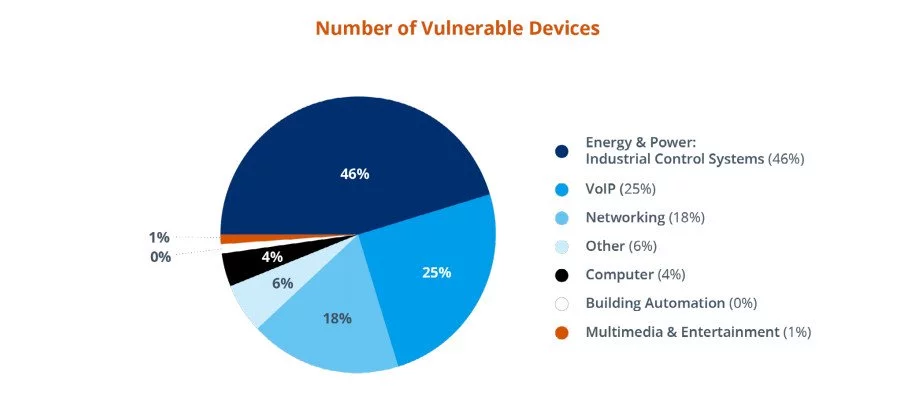
Looking at data collected from its appliances monitoring more than 13 million customer devices, Forescout found 2,500 systems from 21 vendors to be vulnerable to INFRA:HALT.
Almost half (46%) of these devices were deployed in industrial control systems in the Energy and Power sector. A quarter of them were in the VoIP industry and 18% were in the networking sector.
Also Read: 5 Types of Ransomware, Distinguished
HCC Embedded has addressed all INFRA:HALT vulnerabilities with patches that are available on request. Updating to version 4.3 of NicheStack is currently the only solution for complete protection against this set of security issues.
For the many cases where patching is not possible right away, Forescout and JFrog have prepared a script that detects devices running NicheStack and a set of mitigations that could prevent compromise:
CVE-2020-25928, CVE-2020-25767, CVE-2020-25927, CVE-2021-31228, CVE-2020-25926 [DNSv4 client]:
CVE-2021-31226, CVE-2021-31227 [HTTP server]:
CVE-2021-31400, CVE-2021-31401, CVE-2020-35684 [TCP]
CVE-2020-35685 [TCP]
CVE-2020-35683 [ICMPv4]