KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!



IKEA is battling an ongoing cyberattack where threat actors are targeting employees in internal phishing attacks using stolen reply-chain emails.
A reply-chain email attack is when threat actors steal legitimate corporate email and then reply to them with links to malicious documents that install malware on recipients’ devices.
As the reply-chain emails are legitimate emails from a company and are commonly sent from compromised email accounts and internal servers, recipients’ will trust the email and be more likely to open the malicious documents.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
In internal emails seen by BleepingComputer, IKEA is warning employees of an ongoing reply-chain phishing cyber-attack targeting internal mailboxes. These emails are also being sent from other compromised IKEA organizations and business partners.
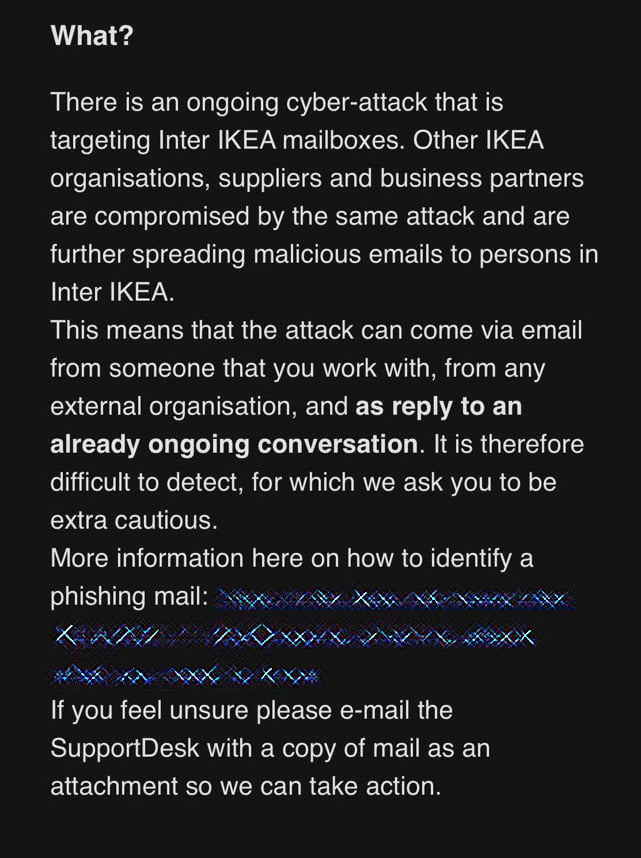
“There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organisations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA,” explained an internal email sent to IKEA employees and seen by BleepingComputer.
“This means that the attack can come via email from someone that you work with, from any external organisation, and as a reply to an already ongoing conversations. It is therefore difficult to detect, for which we ask you to be extra cautious.”
IKEA IT teams warn employees that the reply-chain emails contain links with seven digits at the end and shared an example email, as shown below. In addition, employees are told not to open the emails, regardless of who sent them, and to report them to the IT department immediately.
Recipients are also told to tell the sender of the emails via Microsoft Teams chat to report the emails.
Threat actors have recently begun to compromise internal Microsoft Exchange servers using the ProxyShell and ProxyLogin vulnerabilities to perform phishing attacks.
Once they gain access to a server, they use the internal Microsoft Exchange servers to perform reply-chain attacks against employees using stolen corporate emails.
As the emails are being sent from internal compromised servers and existing email chains, there is a higher level of trust that the emails are not malicious.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
There is also concern that recipients may release the malicious phishing emails from quarantine, thinking they were caught in filters by mistake. Due to this, they are disabling the ability for employees to release emails until the attack is resolved.
“Our email filters can identify some of the malicious emails and quarantine them. Due to that the email could be a reply to an ongoing conversation, it’s easy to think that the email filter made a mistake and release the email from quarantine. We are therefore until further notice disabling the possibility for everyone to release emails from quarantine,” IKEA communicated to employees.
While IKEA has not responded to our emails about the attack and has not disclosed to employees whether internal servers were compromised, it appears that they are suffering from a similar attack.
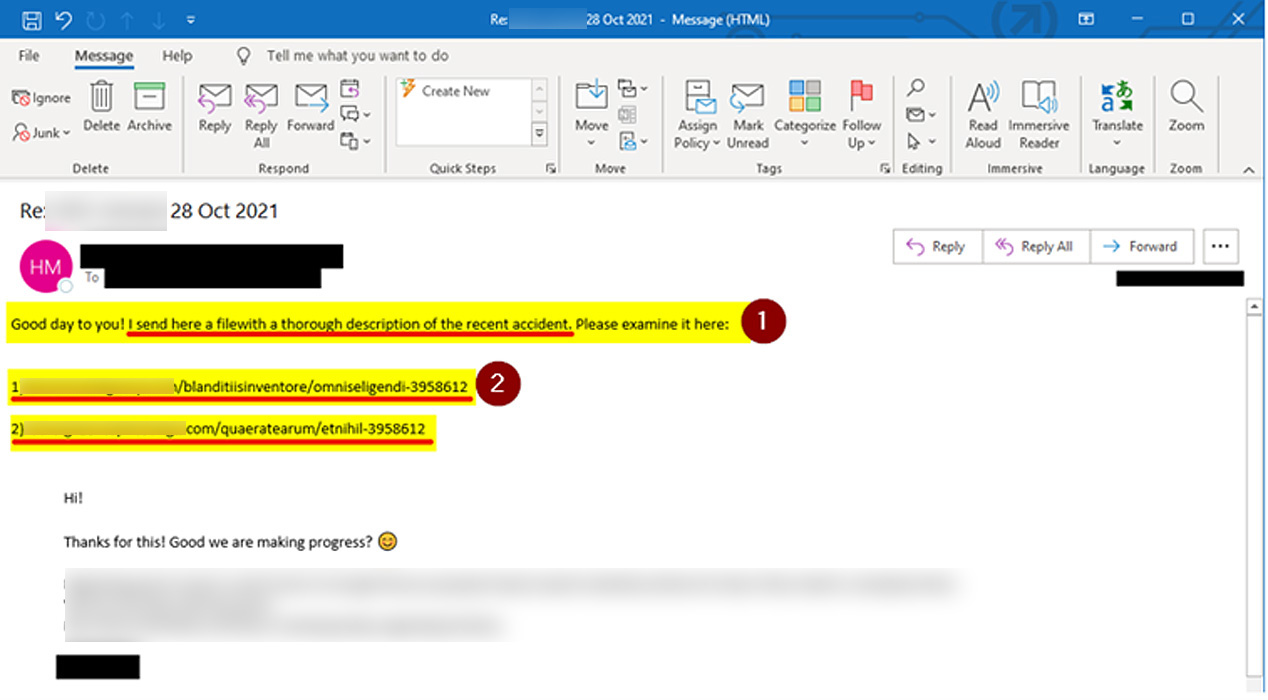
From the URLs shared in the redacted phishing email above, BleepingComputer has been able to identify the attack targeting IKEA.
When visiting these URLs, a browser will be redirected to a download called ‘charts.zip’ that contains a malicious Excel document. This attachment tells recipients to click the ‘Enable Content’ or ‘Enable Editing’ buttons to properly view it, as shown below.
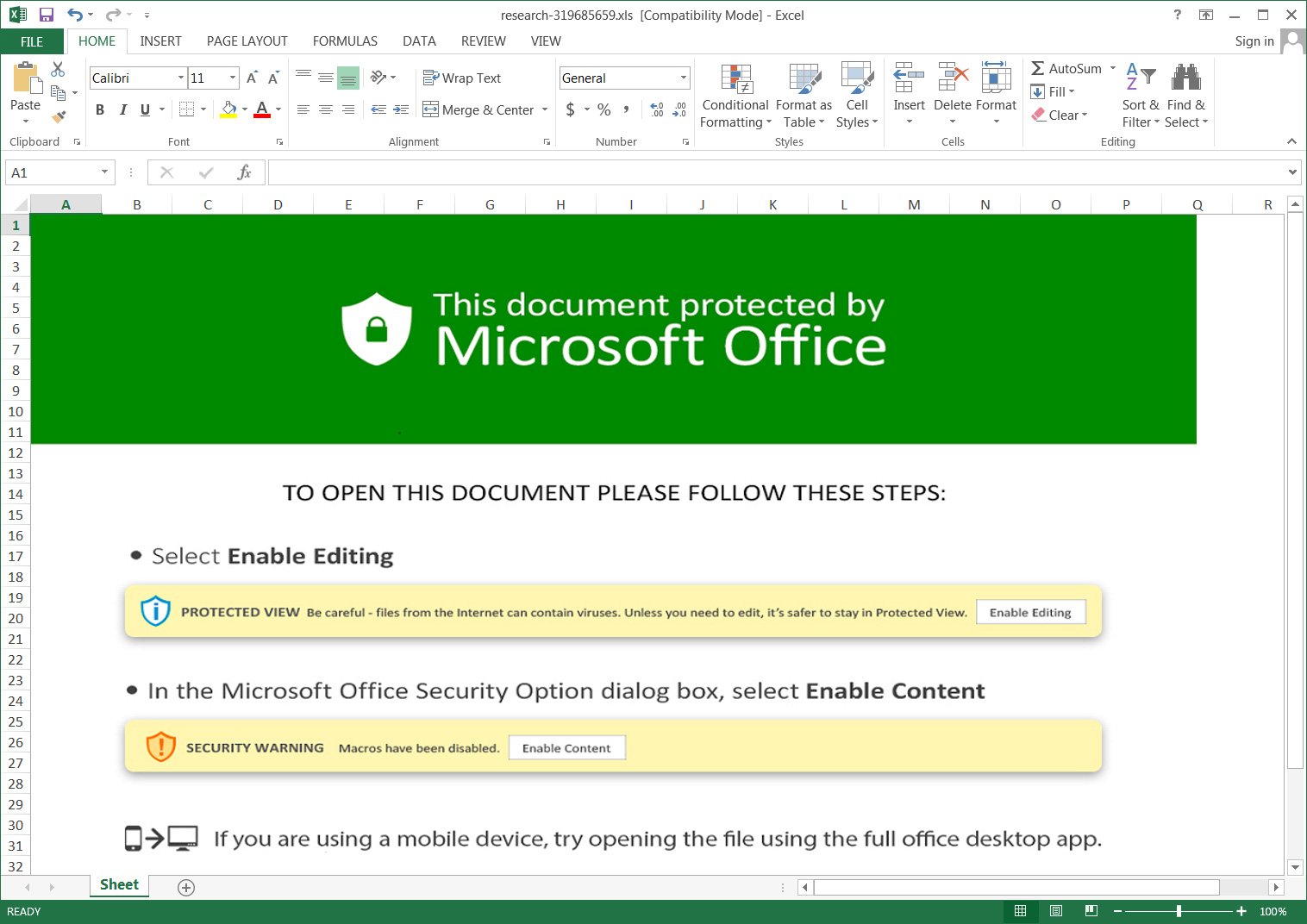
Once those buttons are clicked, malicious macros will be executed that download files named ‘besta.ocx,’ ‘bestb.ocx,’ and ‘bestc.ocx’ from a remote site and save them to the C:\Datop folder.
These OCX files are renamed DLLs and are executed using the regsvr32.exe command to install the malware payload.
Campaigns using this method have been seen installing the Qbot trojan (aka QakBot and Quakbot) and possibly Emotet based on a VirusTotal submission found by BleepingComputer.
The Qbot and Emotet trojans both lead to further network compromise and ultimately the deployment of ransomware on a breached network.
Due to the severity of these infections and the likely compromise of their Microsoft Exchange servers, IKEA is treating this security incident as a significant cyberattack that could potentially lead to a far more disruptive attack.