KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A large scale attack targeted hundreds of thousands of WordPress websites over the course of 24 hours, attempting to harvest database credentials by stealing config files after abusing known XSS vulnerabilities in WordPress plugins and themes.
“Between May 29 and May 31, 2020, the Wordfence Firewall blocked over 130 million attacks intended to harvest database credentials from 1.3 million sites by downloading their configuration files,” Wordfence QA engineer and threat analyst Ram Gall said.
“The peak of this attack campaign occurred on May 30, 2020. At this point, attacks from this campaign accounted for 75% of all attempted exploits of plugin and theme vulnerabilities across the WordPress ecosystem.
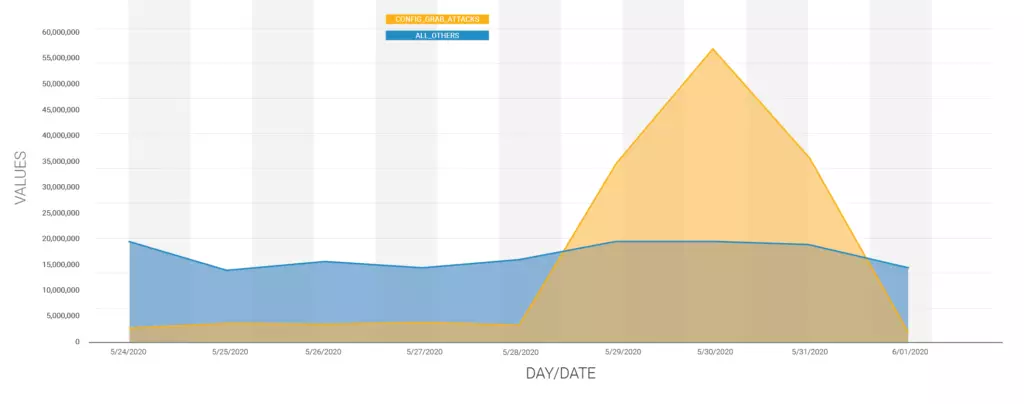
The attackers were trying to download the wp-config.php WordPress configuration file which contains database credentials and connection info, besides authentication unique keys, and salts.
If they successfully exploited any vulnerable plugins used by the targeted sites, the hackers could easily steal credentials from their databases and takeover the websites.
“Attacks by this campaign should be visible in your server logs,” Gall explained. “Look for any log entries containing wp-config.php in the query string that returned a 200 response code.”
Based on the 20,000 different IP addresses used to launch the attacks in this campaign, the WordPress security provider’s researchers were able to link this massive campaign to another large-scale attack that started on April 28 and resurfaced on May 11 to also target hundreds of thousands of vulnerable WordPress sites.
In that campaign, the threat actor—tracked by Wordfence since February—was attempting to plant backdoors or to redirect visitors to malvertising sites by exploiting cross-site scripting (XSS) vulnerabilities in plugins patched months or even years ago and previously targeted in other attacks.
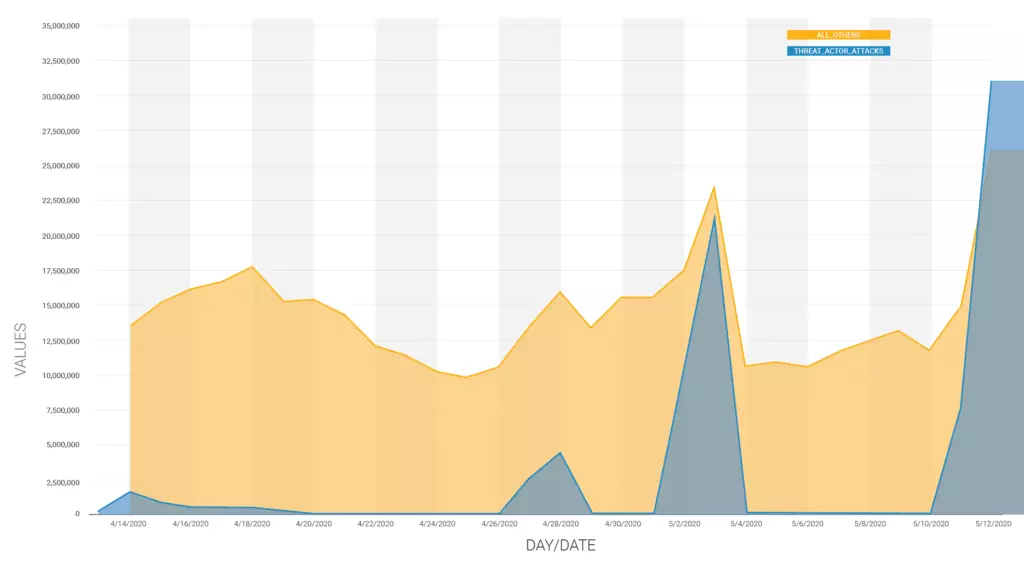
The attackers behind these campaigns were able to launch more than 20 million attacks against over half a million sites on May 3rd alone.
To defend against this type of attack, WordPress site owners and admins should keep all their plugins and themes up to date to patch the vulnerabilities this threat actor is trying to exploit to compromise their sites,
They should also delete or disable the ones that were removed from WordPress’ repository since they are no longer maintained and they could come with previously undiscovered security vulnerabilities that will never be patched.
Windows 10 includes two disk cleanup features that allow users to free up storage space used by unnecessary system and temporary files. Microsoft is making changes to these features to prevent Windows users from deleting files in the Downloads folder by accident.
With the release of Windows 98, Microsoft has been including a tool called ‘Disk Cleanup’ that frees up space by removing unnecessary system files, past Windows installations, old Windows updates, and temporary files.
When the Windows 10 October 2018 Update was released, Microsoft quietly snuck the Downloads folder as an option that can be selected to clean when running Disk Cleanup.
This addition, though, was a cause of concern for many, as people could mistakenly select it and delete files that they are stored in that folder.
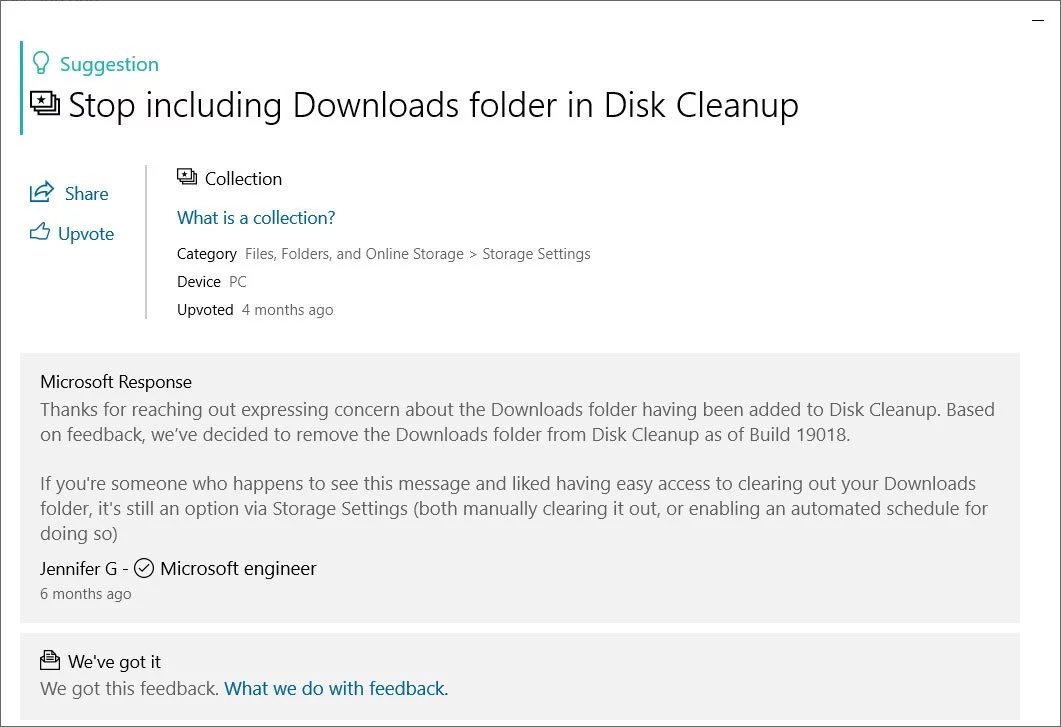
In Windows 10 2004, released last month, Microsoft has once again quietly tweaked the Disk Cleanup utility by removing the Downloads folder as an option.
As can be seen below, Disk Cleanup in Windows 10 1909, shown on the left, contained a Downloads folder option. The image on the right is the Windows 10 2004 Disk Cleanup with the Downloads folder removed.
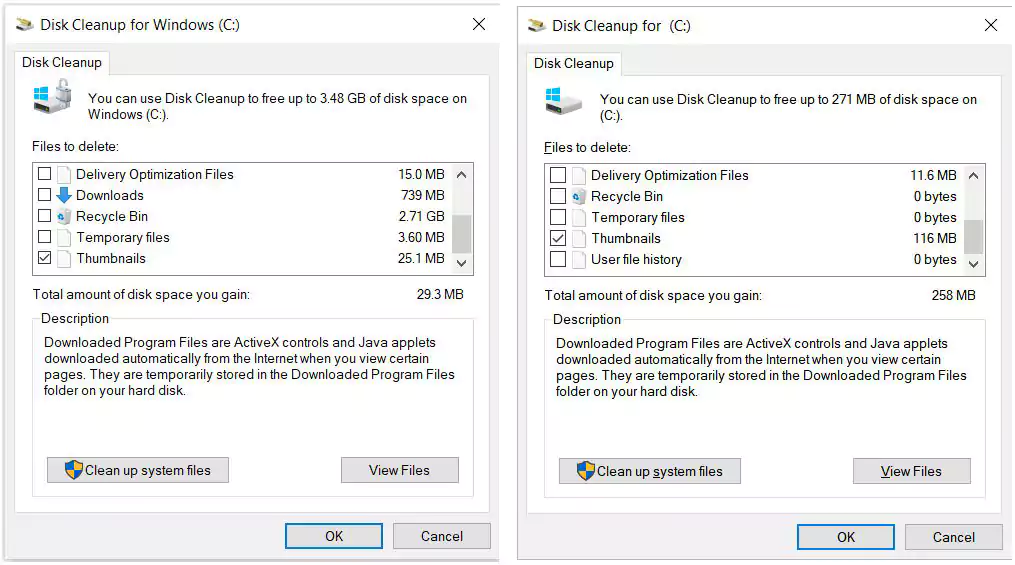
Overall, making this change was a smart decision as the risk was not worth the reward.
Starting with the Windows 10 October 2018 Update, Microsoft has also been steadily improving a modern version of the Disk Cleanup tool as a new integrated feature called Storage Sense.
Unlike Disk Cleanup, which requires manual operation, Storage Sense will automatically monitor the free space on the system drive and cleans up temporary files if space gets too low.
It is possible to configure Storage Sense to treat the files in the Downloads folder as temporary files and delete them if they have been unused for a specified number of days.
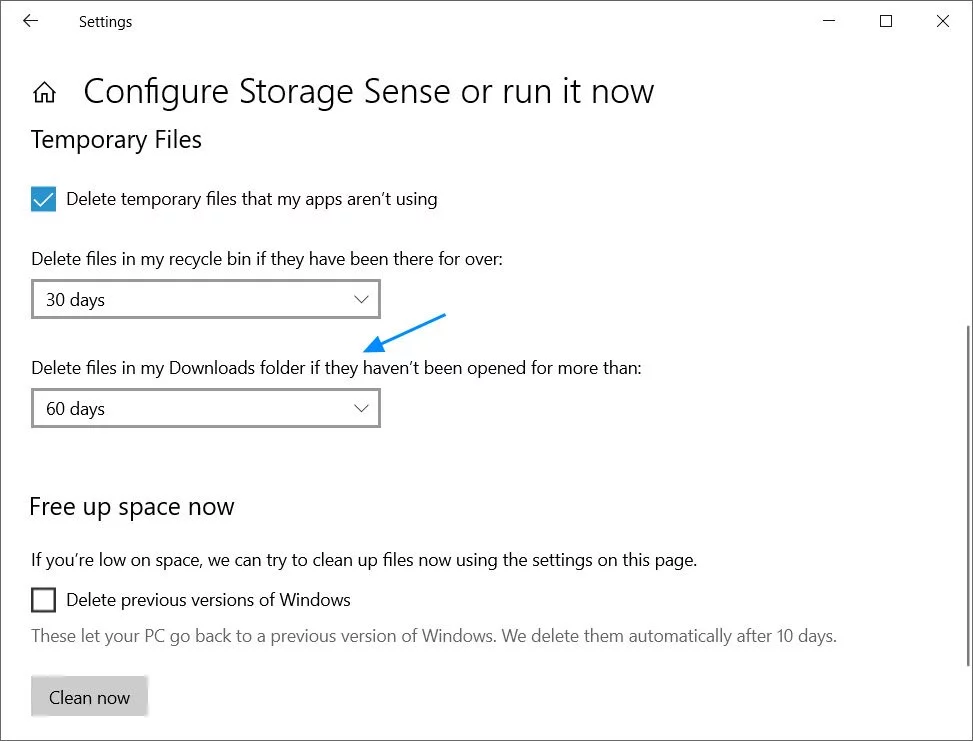
In today’s release of the Windows 10 Insider build 19640, Microsoft is changing this functionality by not clearing unused Downloads if the folder is synced to a cloud provider.
“Based on feedback, if your Downloads folder is synced to a cloud provider, we are disabling the option to have Storage Sense automatically clear out your Downloads folder on a cycle”
This change is most likely being to prevent the synchronized cloud servers from deleting the files if Storage Sense deletes them.

An increasing number of offers for stolen YouTube credentials has been noted recently on hacker and cybercrime forums, where access to accounts is sold in bulk.
Sellers advertise large lists of credentials that are verified for the availability of a YouTube channel and subscriber count.
Cybercriminals have found value in YouTube channels a long time ago, providing them a new audience to expose to fraudulent activities ranging from scams to advertising.
Others simply hijack the channels and ask the legitimate owner to pay a ransom to get it back. YouTube community support is filled with complaints from users that lost access to their channel and were demanded a ransom.
The data comes mostly from infected computers, phishing campaigns, or logs of credentials. It is combed for logins to specific services and then auctioned on forums.
Researchers at IntSights external threat intelligence company found that there’s an increased demand in YouTube credentials on underground markets, which also fuels data verification side businesses.
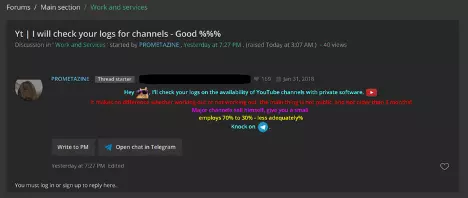
The value of the lists offered is proportional to the subscriber count. For instance, the bidding for a channel with 200,000 subscribers starts at $1,000 with a step of $200.
One post advertised an auction a log for 990,000 YouTube active channels that started at $1,500; anyone paying $2,500 got it without contest. The seller was looking to cash in fast, like other actors, for fear of victims reporting the mischief and reclaiming access to their accounts.
A set of 687 YouTube accounts, broken down by subscriber count, was available for a starting price of $400 and a $100 step. Anyone willing to pay $5,000 would get it on the spot.
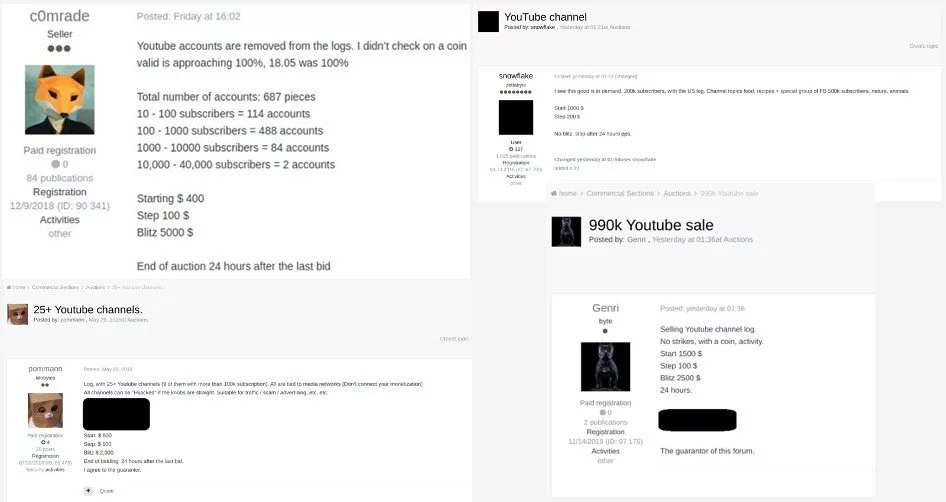
Another actor was looking to sell credentials for more than 25 YouTube channels, some with over 100,000 subscribers for a starting price of $600 and a step of $100. They also offered to sell it immediately to whoever paid $2,000.
Etay Maor, IntSights’ Chief Security Officer, says that the surge of YouTube logs likely originates from databases with Google credentials and infected computers.
Users reporting account hijacking to YouTube often complain that they were tricked into downloading malicious software on their computers.
“They pretended to be sponsors for youtube, once I tried to visit their website, a keylogger/spyware software was downloaded to my browser. They changed my password, removed my known devices, removed my recovery phone number and e-mail within about 2 mins tops. They then tried to extort me to send them btc or they would sell my channel” – extorted YouTube channel owner
Another victim reported a similar story, with fraudsters pretending to look for collaborators.
Maor says that attackers in the past relied on sophisticated phishing campaigns and reverse-proxy toolkits that defeated Google’s two-factor authentication (2FA).
No mention of 2FA from the sellers could mean that the stolen credentials are for accounts where this security option was inactive.

The San Francisco Employees’ Retirement System (SFERS) has suffered a data breach after an unauthorized person gained access to a database hosted in a test environment.
SFERS manages the benefits program for active and retired employees of San Francisco, California.
In a data breach notification filed today, SFERS stated that one of their vendors had set up a test environment that included a database containing the information for approximately 74,000 SFERS members.
On March 21, 2020, the vendor learned that the server had been accessed by an unauthorized third-party on February 24, 2020. They subsequently told SFERS on March 26, when an investigation was started.
“On March 21, 2020, 10up Inc. learned that this server had been accessed by an outside party on February 24, 2020. The vendor promptly shut down the server and began an investigation. The vendor found no evidence that the information of SFERS members was removed from its server, but at this time, it cannot confirm that the information was not viewed or copied by an unauthorized party. On March 26, 2020, the vendor notified SFERS of the server breach and both SFERS and the vendor continue to investigate the potential exposure of data,” the data breach notification states.
While SFERS states that no Social Security Numbers or bank account information was contained in the breach, there was enough personal information exposed that could be used by threat actors in attacks.
According to the notification, the types of information that was exposed is different depending on whether a member is retired or if they had registered on the web site.
The leaked information for all members includes a member’s name, address, date of birth, and beneficiary information.
Retired members also had IRS Form 1099R information (excluding SSN) and the direct deposit bank account routing numbers exposed.
Finally, if a member had registered at the site, the leaked information would have included their login name and security questions and answers.
As the test environment used an old database, the data exposed is from no later than August 29th, 2018.
SFERS is offering all exposed members a complimentary one-year membership of Experian’s IdentityWorks monitoring service.
All members should immediately take advantage of this subscription to monitor their credit history and other information that may be exposed on the dark web.
As the exposed information can be used in phishing attacks, especially the security questions and answers, all affected members should be on the lookout for unusual emails.
If you receive an email claiming to be from SFERS and prompting you to enter your credentials or other sensitive information, it is advised that you contact SFERS directly to confirm the legitimacy of the email.
.
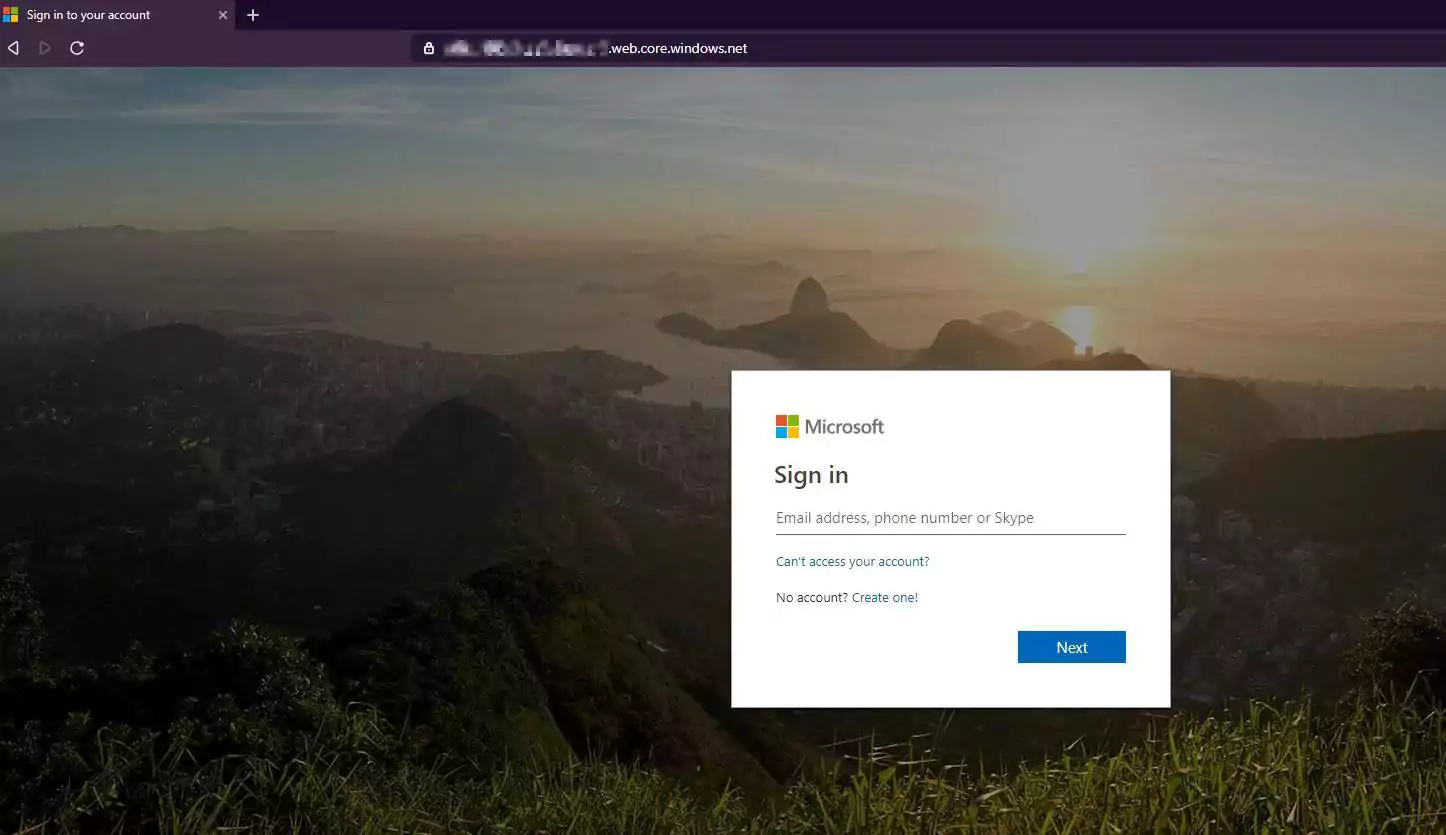
Microsoft Office 365 customers are targeted by a phishing campaign using bait messages camouflaged as notifications sent by their organization to update the VPN configuration they use to access company assets while working from home.
The phishing emails impersonating VPN configuration update requests sent by their company’s IT support department have so far landed in the inboxes of up to 15,000 targets according to stats from researchers at email security company Abnormal Security.
These phishing messages are a lot more dangerous because of the huge influx of employees working remotely and using VPNs to connect to company resources from home for sharing documents with their colleagues and accessing their orgs’ servers.
The attackers are spoofing the sender email address in the phishing emails to match the domains of their targets’ organizations and embed hyperlinks that instead of directing the recipients to new VPN configs send them to phishing landing sites designed to steal their Office 365 credentials.
“Numerous versions of this attack have been seen across different clients, from different sender emails and originating from different IP addresses,” Abnormal Security explains.
“However, the same payload link was employed by all of these attacks, implying that these were sent by a single attacker that controls the phishing website.”
.png)
These attacks could have a high rate of success in tricking potential victims since many recipients might click through and log into their Office 365 accounts to avoid losing remote access to company servers and resources.
The landing page is a cloned Office 365 login page hosted on the Microsoft-owned web.core.windows.net domain by abusing the Azure Blob Storage and it comes with a valid Microsoft certificate, making it a lot harder to detect the phishing attempt.
Abusing the Azure Blob Storage platform to target Office 365 users is the perfect ruse seeing that the landing pages will automatically get their own secure page padlock because of the *.web.core.windows.net wildcard SSL certificate.
This way even the most suspicious targets could get tricked after clicking on the certificate and seeing that it is issued by a Microsoft CA to *.web.core.windows.net, automatically validating the phishing page as official Microsoft login forms in the eyes of potential victims.
“However, the URL of this site should not be trusted, and instead, users should only login from their main company affiliated webpage,” Abnormal Security advises.
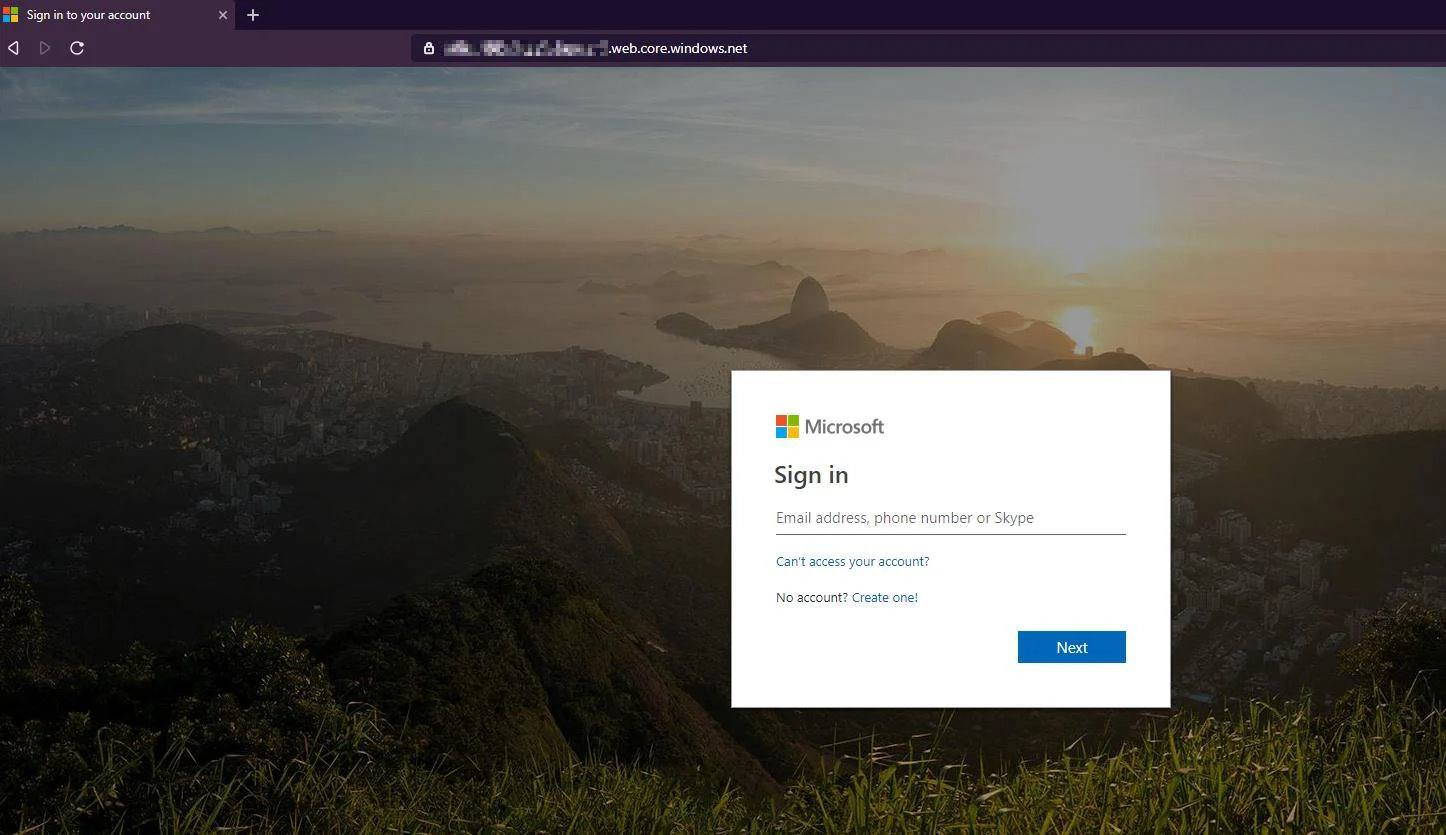
Azure Blob Storage subdomains being used to phishing pages is a known and highly effective tactic BleepingComputer reported about in the past [1, 2, 3].
These phishing attacks can easily be tackled if you set up custom Office 365 block rules to take advantage of the Office 365 ATP Safe Links feature to automatically block them.
If you don’t configure block rules, the only way to be sure that attackers aren’t trying to steal your credentials while entering them in an Office 365 login form is to remember that official login pages are hosted by Microsoft on the microsoft.com, live.com, or outlook.com domains.
Last month, Abnormal Security researchers discovered another highly convincing Office 365 phishing campaign that used cloned imagery from automated Microsoft Teams notifications attempting to steal credentials from almost 50,000 users.