KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






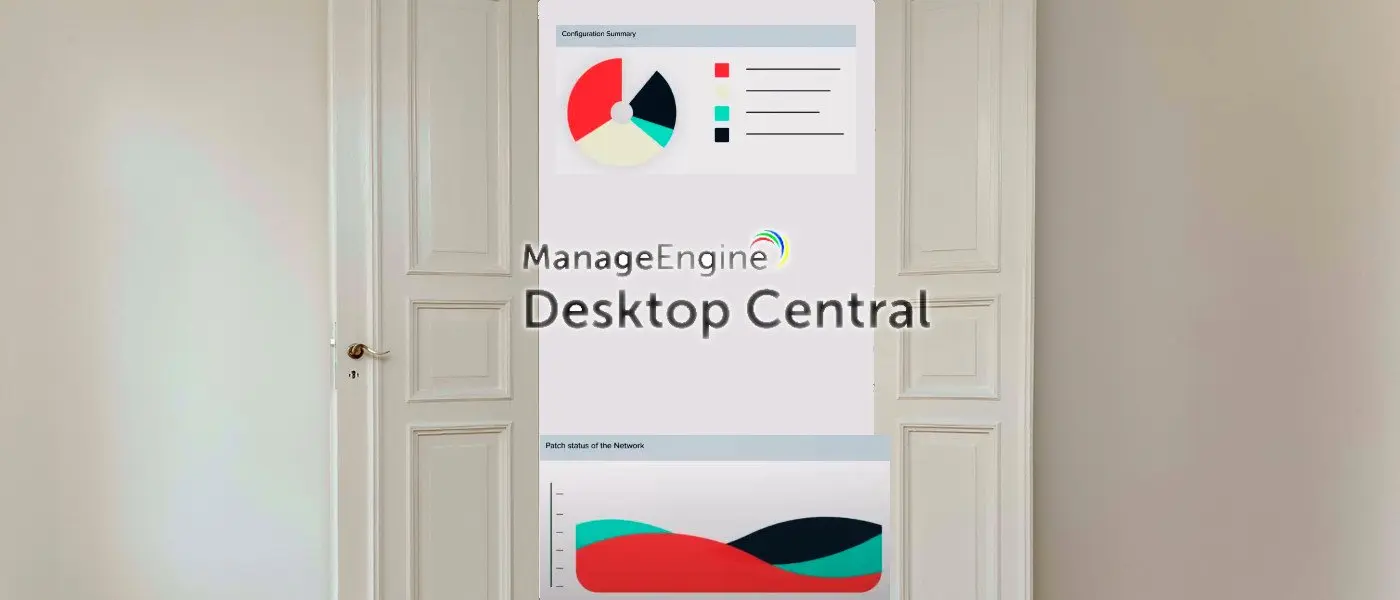
Remote monitoring and management (RMM) software is starting to get attention from hackers as these types of tools provide access to multiple machines across the network.
At least one network access broker has been advertising access to networks of organizations in various regions of the world that use the ManageEngine Desktop Central from Zoho to manage their Windows, Linux, and Mac systems.
Some of the breached companies are attractive targets for ransomware operators, who may already have jumped at the opportunity.
The seller is active on a major Russian-speaking forum where they’ve been announcing network access since at least July 2020. In September, the actor advertised 36 accesses, hoping for a cumulative profit close to $100,000.
In a report shared with BleepingComputer, cyber intelligence company KELA was able to determine that the offer was for Zoho’s ManageEngine Desktop Central, a management platform that lets administrators deploy patches and software automatically on network machines, as well as troubleshoot them through remote desktop sharing.
KELA told BleepingComputer that the actor is not selling RMM access exclusively. In an early post on the forum, they offered domain access. More recently, they offered credentials to 1,000 remote desktop (RDP) servers in China.
Also Read: Does Personal Data Market About To Become The Next Big Thing
Apart from these, though, almost all posts from the access broker’s sales thread are for RMM access. According to KELA, there are at least 53 accesses advertised individually with a cumulative value of over $150,000.
It is difficult to determine the seller’s profit from these transactions because some offers did not disclose a price and they asked potential buyers to make an offer.
There is confirmation that the threat actor sold access to ten networks, though, which earned them around $33,800. The number is likely higher since some deals may have completed in private
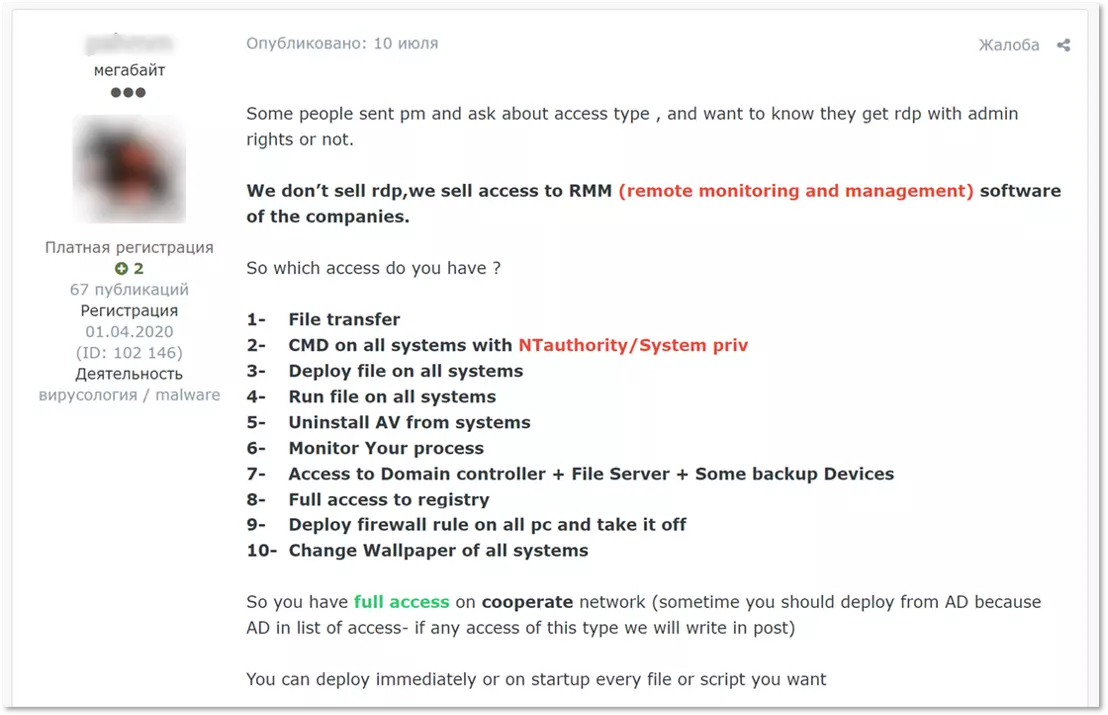
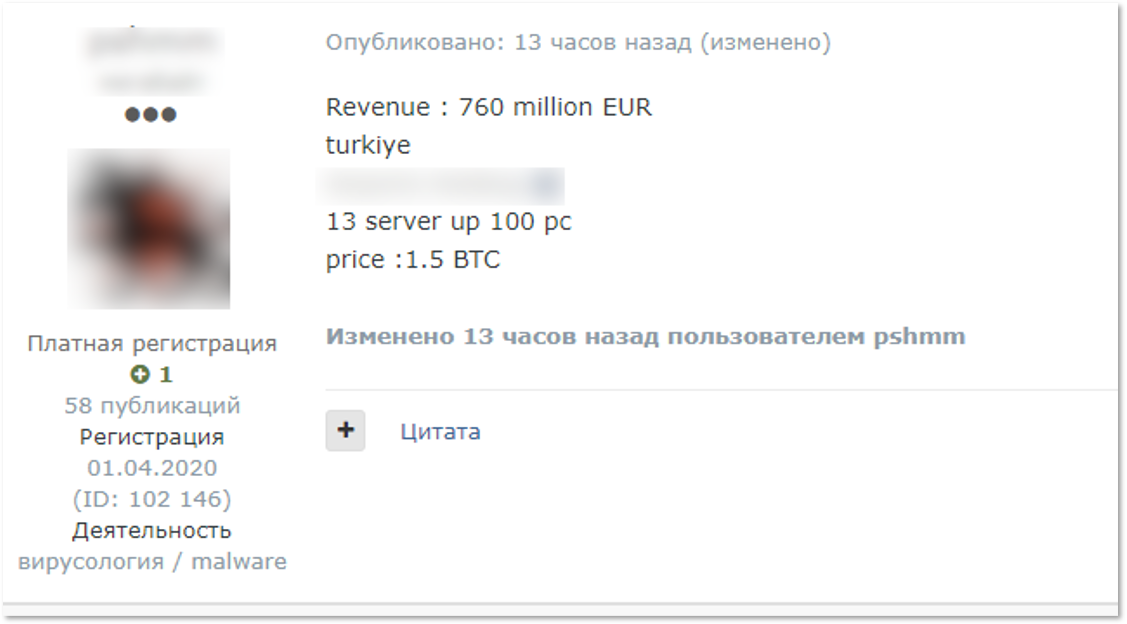
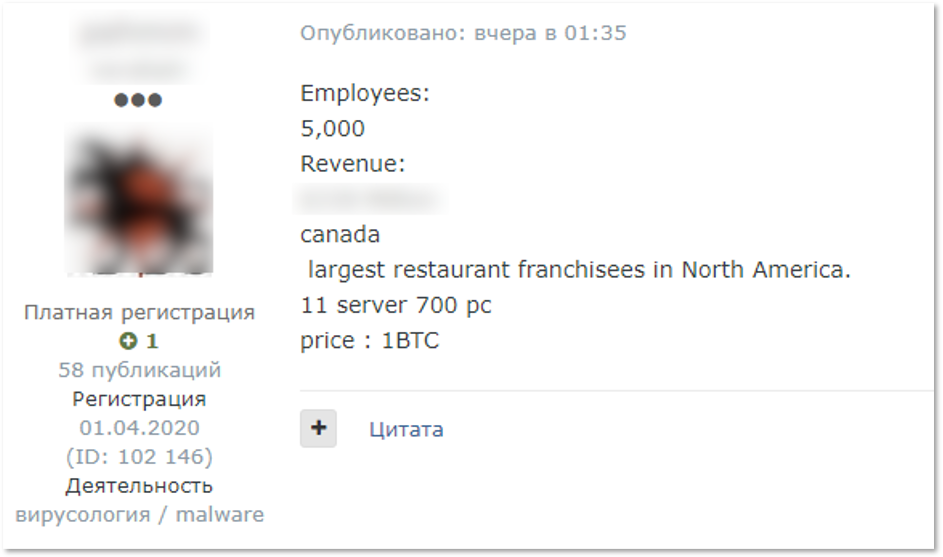
KELA was able to identify multiple victims, but for two of them the network access was the most expensive in the seller’s offer: one company in Turkey and one in Canada. The prices asked for these two were 1.5BTC and 1BTC.
Brief profiles for the two companies published by the broker show revenues of hundreds of millions of US dollars and hundreds of computers on their network, details that caused the sale to complete in a few hours.
 |
 |
However, based on the actor’s statements, they have network access to companies all over the world, most of them in the U.S., including the U.K., Spain, Brazil, and Portugal.
As for the activity sector of the victims, this also varies (IT, education, construction, manufacturing, law, healthcare, government) suggesting that the compromises are opportunistic rather than targeted attacks.
Although there isn’t a strong indication, the buyers are likely connected with ransomware operators.
“We haven’t seen any direct communications between the actor and known ransomware affiliates, for example. However, based on the broker’s wording in posts it’s pretty evident the actor is aiming towards ransomware use cases” – Raveed Laeb, KELA Product Manager
Furthermore, the seller appears hints that the network access they’re selling is suitable for ransomware attacks. Laeb told us that the actor wrote in one of their posts:
“From there [the RMM platform] you can deploy your payloads (cobalt or any other) and take over network. Also if you want you can deploy your file stealer on File server and transfer to your own FTP server.”
Looking for ManageEngine Desktop Central instances exposed on the internet, KELA found close to 900 servers open on various ports.
Also Read: PDPA For Companies: Compliance Guide For Singapore Business
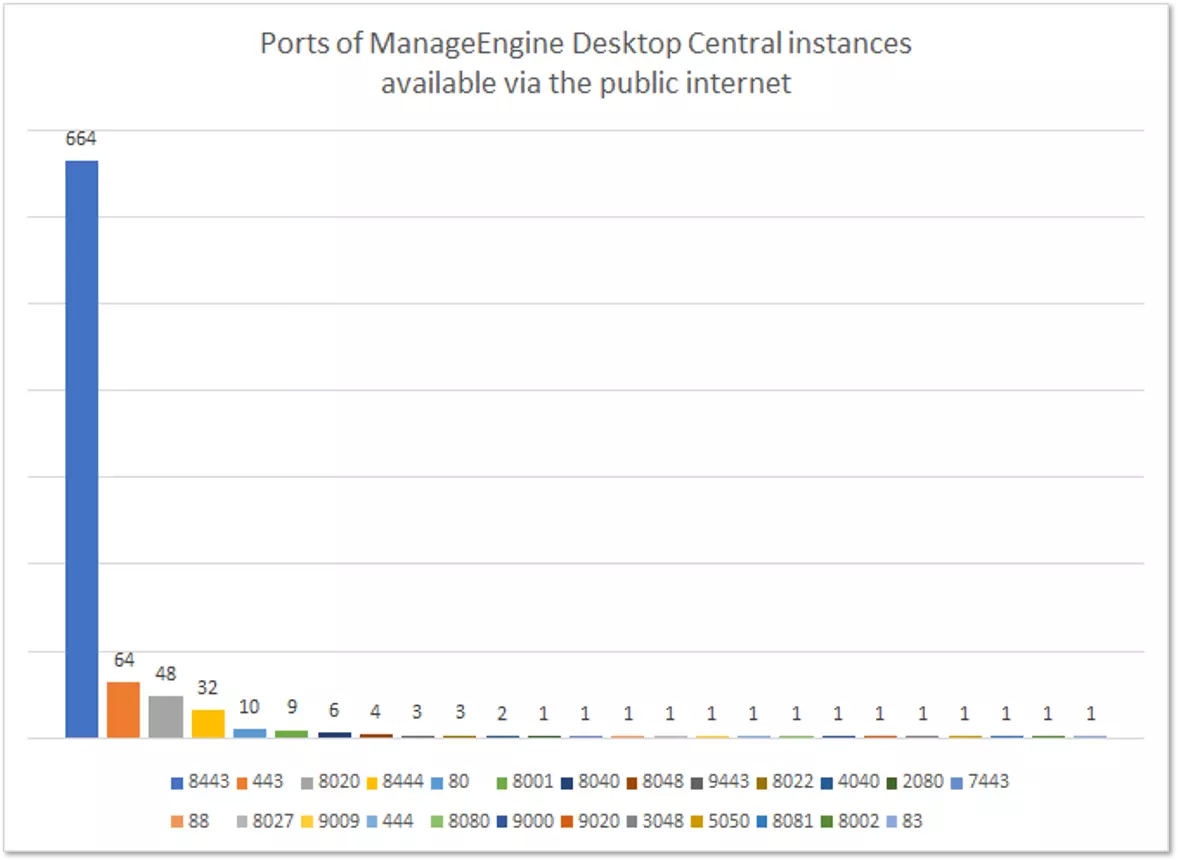
As for the hacking method, this remains unknown at the moment; but it could be anything from attacking a managed services provider, direct brute-force attacks, or exploiting the remote code execution vulnerability CVE-2020-10189 disclosed in March.
Laeb told us that the actor leveraging this flaw is also unlikely because the actor is selling login credentials to the management platform, and exploiting the vulnerability is typically for backdooring the server and dropping malware. However, this is just an assumption since there isn’t a clear and complete profile of the seller’s activity and abilities.