KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







One of Iran’s largest privately-owned airlines, Mahan Air, has announced a cybersecurity incident that has resulted in its website going offline and potentially data loss.
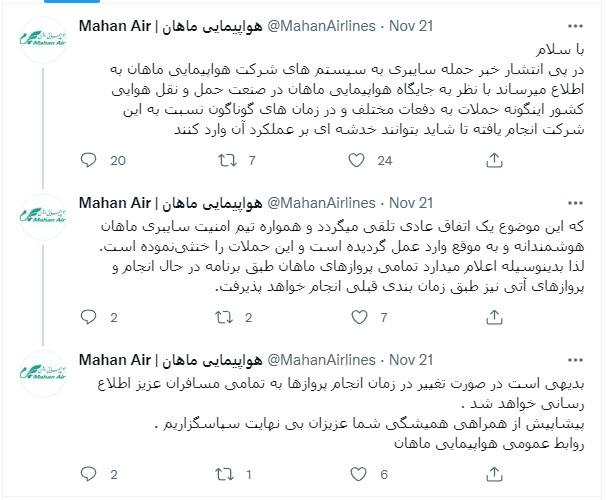
As the firm announced on Twitter, dealing with hacker attacks is nothing out of the ordinary for them, so even though some damage has been done, the flight schedules won’t be affected.
As such, even though people can’t access Mahan’s website, all international and domestic flights are running as usual without changes or delays.
Moreover, the company claims that the attack has been thwarted successfully and in a short time, downplaying its significance and disregarding any real impact.
“Following the news of the cyber attack on the systems of Mahan Airlines, it is reported that due to the position of Mahan Airlines in the country’s aviation industry, such attacks have been carried out against this company many times and at different times, so that they may be damaged,” reads the translated tweet by Mahan airlines.
Also Read: How To Secure Your WiFi Camera: 4 Points To Consider
“This is considered a normal occurrence and Mahan Cyber Security Team has always acted intelligently and in a timely manner and has thwarted these attacks. Therefore, it hereby announces that all Mahan flights will be operated according to the schedule and future flights will be operated according to the previous schedule.”
Mahan Air was added to the US sanctions list in 2011 for supporting members of Iran’s Islamic Revolutionary Guard Corps (IRGC).
In 2019, the US Treasury published a statement on Mahan Air’s operation, detailing the following:
“Mahan Air has transported IRGC-QF operatives, weapons, equipment, and funds abroad in support of the IRGC-QF’s regional operations, and has also moved weapons and personnel for Hizballah.”
“Since the onset of the Syrian civil war, Mahan Air has routinely flown fighters and materiel to Syria to prop up the Assad regime, which has contributed to mass atrocities and displacement of civilians.”
Although Mahan’s operations oppose American strategic interests, which led to actual military action in July 2020, the hackers responsible for the most recent incident don’t seem to be Americans.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
The actor who took responsibility for the cyberattack on Mahan Air is ‘Hooshyarane Vatan,’ who sees IRGC as their enemy and says they fight for the rights of the Ahwaz minority (Iranian Arab minority).
The hackers claim to have stolen confidential documents exposing how Mahair Air has worked with the IRGC and threatened to publish names, numbers, and proof of Mahan’s activities.
“Hacking Mahan Airlines is the first step of a program to stop the looting and encroachments of the corrupt corps on the city and the people of Ahvaz and Khuzestan. With the confidential documents we have obtained from the internal network of Mahan Airlines, we will prove our claim of Mahan complicity in the criminal activities of the IRGC, and we will also show that the Quds force is looting the money and resources of the people and the country of Iran among insurgent groups,” reads a translated text from the alleged hackers.
“And the foreign militia squanders money and at the same time uses the same oppressed people as cover for the air transport of weapons, equipment and ammunition.”
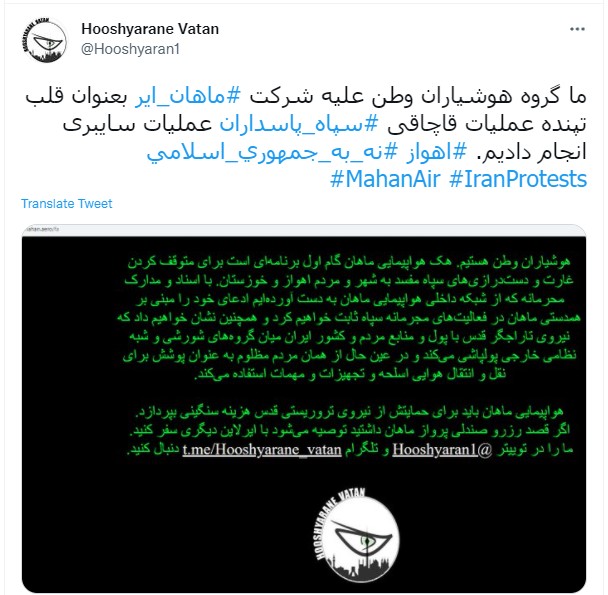
As the actors wrote on their Telegram channel, they have proof of the airline hiding military shipments in civilian flights to secure them from attacks.
Last week, a crescendo of reports about Iranian hackers targeting American, Israeli, and European entities took place. At the same time, Microsoft published a report identifying six distinct Iranian hacking groups that appear to be state-sponsored.
This reporting culminated with the indictment of two Iranian cyber-actors who attempted to influence American voters between September and November 2020, promoting false information under the ‘Proud Boys’ attire.
Both of the identified actors allegedly worked for a cybersecurity company that provided services to the Iranian government.