KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Intrusion activity related to the Supernova malware planted on compromised SolarWinds Orion installations exposed on the public internet points to an espionage threat actor based in China.
Security researchers named the hacker group Spiral and correlated findings from two intrusions in 2020 on the same victim network to determine activity from the same intruder.
Unlike the malware used in the SolarWinds supply-chain attack [1, 2, 3], which was embedded in the Orion software builds from the developer, the Supernova web shell ended inside the platform after hackers exploited a critical vulnerability in product installations reachable over the public web.
The initial assessment concluded that the malware is from a different threat group than Nobelium, as Microsoft tracks the Russia-linked supply-chain hackers. Others track the actor under different names: UNC2452 (FireEye), StellarParticle (CrowdStrike), SolarStorm (Palo Alto Networks), Dark Halo (Volexity).
Researchers at SecureWorks Counter Threat Unit (CTU) found Supernova dropped on a customer’s network during an incident response job in November 2020.
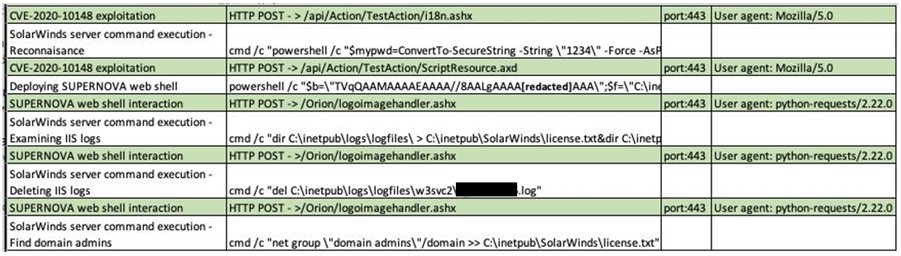
The intrusion vector was a SolarWinds Orion API authentication bypass (CVE-2020-10148) that allowed the attacker to execute a reconnaissance script and commands and drop the Supernova web shell 30 minutes later.
Also Read: 10 Practical Benefits of Managed IT Services
The gap between the last reconnaissance command and dropping the web shell is likely accounted by the intruder running scan-and-exploit activity and find high-value victims on the network.
The attack was targeted because once the web shell was planted, the attacker mapped network shares on only two servers that gave them domain control and access to sensitive business data.
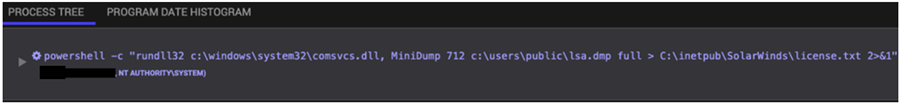
After planting Supernova in SolarWinds Orion by trojanizing a legitimate file the platform used (app_web_logoimagehandler.ashx.b6031896.dll), the attacker used the comsvcs.dll library to dump the content of the LSASS (Local Security Authority Subsystem Service) process.
An earlier intrusion on the same network identified in August was carried out similarly, but the entry point was a vulnerable, public-facing ManageEngine ServiceDesk server.
In this case, SecureWorks CTU found that initial access had occurred in 2018 and the hackers “used the access to periodically harvest and exfiltrate domain credentials.”
At the time, the researchers were unable to attribute the activity to a particular threat group but they noticed that they used the same method and output file path to dump the LSASS process,
The similarities did not stop at this, though, as the actor accessed the same two servers as in the November 2020 incident. Additionally, three of the compromised admin accounts were used on both occasions.
Although the modus operandi (targeting ManageEngine servers, long-term persistence to collect credentials and steal data, theft of intellectual property) is characteristic to Chinese hacking groups, it does not count as strong evidence for more confident attribution.
However, the intrusion in August provided the researchers a more reliable detail to confirm their theory: an IP address in China for a host on the attacker’s infrastructure.
“The naming convention of this host was the same as another host used by the threat actor to connect to the network via a VPN connection” SecureWorks CTU
Based on their analysis, SecureWorks CTU researchers believe that the hackers likely exposed the IP address after they downloaded the endpoint agent installer from the network and installing it on their infrastructure.
“The exposure of the IP address was likely unintentional, so its geolocation supports the hypothesis that the SPIRAL threat group operates out of China,” the researchers say.
The researchers highlight the difficulties of attributing cyberattacks to a particular threat actor but believe that their discoveries point to a China-based hacking crew.
They make available a set of indicators of compromise containing IP addresses for Spiral infrastructure in China and command and control servers, along with hashes for the Supernova web shell delivered after exploiting CVE-2020-10148.
Update [March 8, 19:28 ET]: SolarWinds reached out to BleepingComputer with a statement to clarify that Supernova is malware planted in the Orion software present on the customer network and not part of the supply-chain attack attributed to Russian hackers.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
“This report references an incident where a network was first compromised in a way that was unrelated to SolarWinds. That breach enabled the attackers to add the malicious Supernova code to Orion software on the customer’s network. It is important to note that Supernova is not associated with the broad and sophisticated supply chain attack that targeted multiple software companies as vectors. Supernova was neither signed nor delivered by SolarWinds and the issue was addressed in Orion platform updates that were released in December” – SolarWinds