KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Threat analysts have observed a new campaign named ‘OiVaVoii’, targeting company executives and general managers with malicious OAuth apps and custom phishing lures sent from hijacked Office 365 accounts.
According to a report from Proofpoint, the campaign is still ongoing, though Microsoft is monitoring the activity and has already blocked most of the apps.
The impact of executive account takeovers ranges from lateral movement on the network and insider phishing to deploying ransomware and business email compromise incidents.
Also Read: Website Ownership Laws: Your Rights And What These Protect
OAuth is a standard for token-based authentication and authorization, removing the need to enter account passwords.
Apps that use OAuth require specific permissions such as file read and write permissions, access to calendar and email, and email send authorization.
The purpose of this system is to offer increased usability and convenience while maintaining a high security level within trustworthy environments by reducing credential exposure.
With OAuth tokens, cloud-based third-party applications can access the data points required to provide businesses with productivity features without getting the users’ passwords.
The actors behind the OiVaVoii campaign used at least five malicious OAuth applications, four of them currently blocked: ‘Upgrade’, ‘Document’, ‘Shared’, and ‘UserInfo’.
.jpg)
Three of these apps were created by verified publishers, which indicates that the threat actors compromised the account of a legitimate Office tenant.
The threat actors then used the apps to send out authorization requests to high-ranking executives in the targeted organizations. In many cases, the recipients accepted the requests, seeing nothing suspicious in them.
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
When victims hit the Accept button, the threat actors use the token to send emails from their accounts to other employees within the same organization.
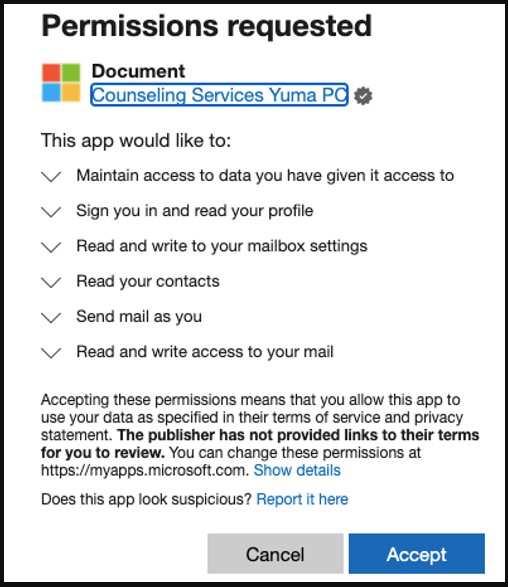
If they click on Cancel, a manipulation in the Reply URL redirects them back to the consent screen, locking them on the same page until they accept the permission request.
Proofpoint also mentions the likelihood of man-in-the-middle proxy attacks that could also compromise the target’s account credentials.
Four of the malicious OAuth apps used by the actors in this campaign have been blocked, but new ones are being created and employed in the same way.
Also, executives who have already been compromised and given access to their accounts remain high-risk points for impacted organizations.
The potentially compromised firms need to revoke the permissions, delete the apps, remove any malicious mailbox rules added by the actors, and scan for any dropped files.
Finally, all employees should be trained to suspect internal communications, especially messages from high-ranking executives that don’t align with their standard business practices.