KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Bad guys find unprotected Elasticsearch servers exposed on the web faster than search engines can index them. A study found that threat actors are mainly going for cryptocurrency mining and credential theft.
For the duration of the experiment, a honeypot with a fake database recorded more than 150 unauthorized requests, the first one occurring less than 12 hours since being exposed.
Comparitech’s research team, led by Bob Diachenko, left the Elasticsearch server exposed on the internet from May 11 until May 22. In this period, the machine an average of 18 attacks every day.
Search engines like Shodan and BinaryEdge indexed the system on May 16 and May 21, respectively. Attackers, however, were quicker and started probing it eight hours and 30 minutes after it was deployed.
Before getting indexed by the search engines, the server was hit more than three dozen times, indicating that at least some threat actors don’t wait for the machines to appear in public resources and actively scan the internet to discover them.
Once indexed, though, it took a minute for two attacks to target the honeypot. The highest number of requests in a day counted 22.
Comparitech admits that some of the requests may have been from security researchers looking for new open servers. However, distinguishing between them and the bad guys is not something easily done.
According to the study, most of the attacks originated from the U.S. (89), Romania (38), and China (15). This information is unreliable, though, because attackers can hide their true IP address by using a proxy service.
“Attackers weren’t just interested in stealing data. Some wanted to hijack servers to mine cryptocurrency, steal passwords, and destroy data” – Comparitech
Also read: 7 Key Principles of Privacy by Design that Businesses should adopt
From the attacks observed, many actors were looking to mine for cryptocurrency by exploiting an old vulnerability (CVE-2015-1427) to install a miner. Multiple IP addresses were used for these attacks but all had in common the download source for the mining script.
Stealing passwords for the server was also a common occurrence via the same vulnerability as the one used for cryptojacking along with another old bug affecting Elasticsearch (CVE-2015-5531 – directory traversal) to get to the server’s /etc/passwd file.
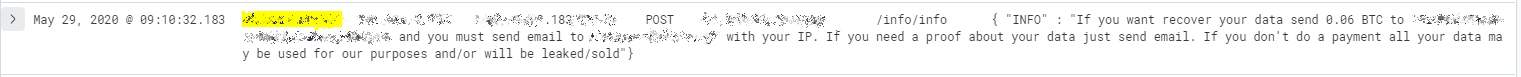
More exotic attacks include changing the server configuration to delete the contents inside and asking for a ransom after destroying the data.
The latter occurred outside the experiment’s period and the attackers asked for 0.06BTC, currently about $550. This is a common extortion practice, with some actors turning a nice profit.
Most of the requests observed during the experiment probed the database, trying to establish its status and settings, Comparitech says.
Unprotected Elasticsearch servers have caused data leaks with billions of records for millions of users.
Information gleaned this way can serve a myriad of nefarious purposes ranging from phishing and account hijacking to identity theft.
To prevent unauthorized access to an Elasticsearch server, administrators should make sure that authentication is enabled and strong credentials are used. Also, TLS should be enabled to ensure that data is encrypted when transiting the network.
Also read: Free 8 Steps Checklist for Companies to Prevent Data Breach