KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The source code for the ChastityLock ransomware that targeted male users of a specific adult toy is now publicly available for research purposes.
Users of the Bluetooth-controlled Qiui Cellmate chastity device were targets of an attack with this malware last year after security researchers found a vulnerability in the toy that allowed locking it remotely.
Qiui Cellmante is a connected sex toy with a companion app to control its locking/unlocking via Bluetooth that is typically managed by someone else than the person wearing the device.
In October 2020, researchers at Pen Test Partners published details about a serious vulnerability that allowed a remote attacker to take control of any Qiui Cellmate device.
They found that making a request to any API endpoint did not require authentication and that using a six-digit “friend code” would return “a huge amount of information about that user,” such as location, phone number, plain text password.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
“It wouldn’t take an attacker more than a couple of days to exfiltrate the entire user database and use it for blackmail or phishing,” Pen Test Partners wrote in their report.
Following the disclosure, an attacker started targeting Qiui Cellmate mobile app users who controlled the smart toy and locked the chastity device. Victims were asked to pay 0.02 bitcoins, around $270 at the time of the attacks.
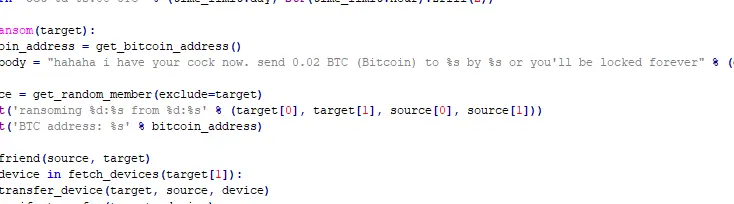
The founder of the VXUnderground research group told BleepingComputer that they published the source code for ChastityLock ransomware after receiving it from someone who got it from the attacker.
The malware includes code that communicates to Qiui’s API endpoints to enumerate user info and send messages to the victim app and add friends, according to analysis from security researcher Ax Sharma.
Soon after the attacks started, a flood of complaints came from victim users reporting that they could no longer control the smart adult toy. Some of them fell victim to the attacker multiple times.
From screenshots seen by BleepingComputer, the attacker engaged victims after locking the chastity devices they controlled. The attacker also mocked victims when they asked what had happened, saying that they used magic to take control of the smart adult toy.
Some users were concerned that the only way to remove the Cellmate device was by cutting it off since there was no manual override for the Bluetooth lock.
However, cutting the hardened steel used for the lock required an angle grinder, and given the sensitive area, this was far from an option for victims.
Luckily, some emergency escape possibilities were available. One of them was to contact remote support and ask them to unlock and reset the Cellmate. Another involved only a screwdriver to unlock the device manually, and Qiui posted a video showing how to do it. The latter came with voiding the warranty of the product.
In a conversation with a party unknown to BleepingComputer, the attacker said that nobody paid the ransom. It is unclear if this was because the victims unlocked the device themselves, through Qiui support, or the attacker did it.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
Qiui addressed the issues causing all the trouble, so the latest version of the app should be safe to use.