KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A threat actor is selling account databases containing an aggregate total of 34 million user records that they claim were stolen from seventeen companies during data breaches.
On October 28th, a data breach broker created a new topic on a hacker forum to sell the stolen user databases for seventeen companies.
In a conversation with BleepingComputer, the seller told us that they were not responsible for hacking into the seventeen companies and is acting as a broker for the databases.
When asked how the hacker gained access to the various sites, the seller stated, “Not sure if he want to disclose.”
Stolen databases are typically sold first in private sales, like those listed above, with previous ranging from $500, as seen in the Zoosk data breach, to $100,000 for the Wattpad database.
After some time, it is common for the stolen databases to be released for free on hacker forums to increase a threat actor’s ‘street cred.’
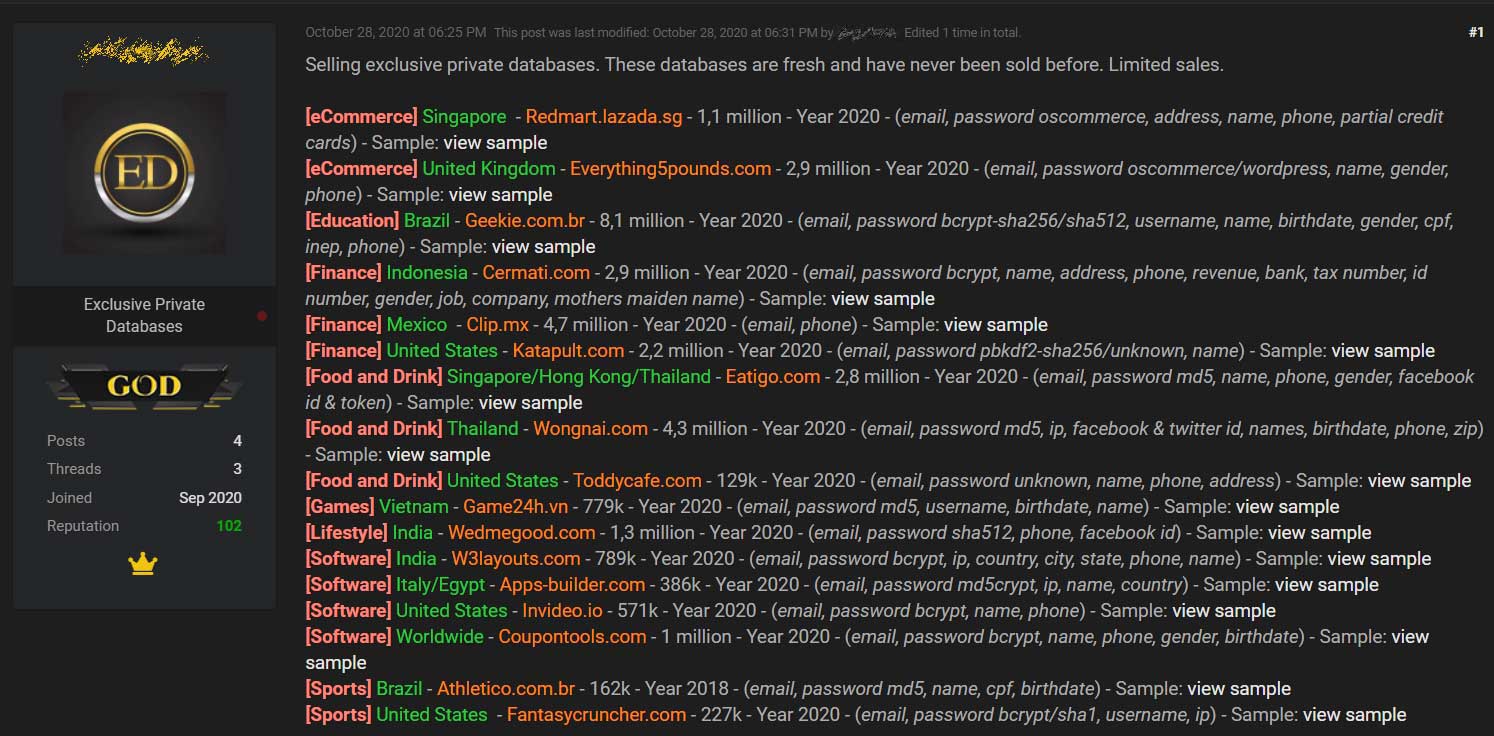
According to the data breach broke, all of the seventeen databases being sold were obtained in 2020, with the largest breach being Geekie.com.br with 8.1 million records. The most well-known affected company is Singapore’s RedMart that exposed 1.1 million rec.
The seller told BleepingComputer that they are selling the RedMart database for $1,500.
None of these companies have previously reported recent data breaches prior to this week.
Also Read: What Is A Governance Framework? The Importance And How It Works
After BleepingComputer contacted all affected companies, only RedMart disclosed a data breach yesterday, and Wongnai.com told BleepingComputer that they are investigating the incident.
“Thanks for your inquiry, we were aware of this incident last night (Bangkok time) and our tech team have been investigating this matter,” Wongnai emailed BleepingComputer.com.
The seventeen databases being sold are shown below:
| Company | User Records | Disclosed? |
| Geekie.com.br | 8.1 million | No |
| Clip.mx | 4.7 million | No |
| Wongnai.com | 4.3 million | Yes via email |
| Cermati.com | 2.9 million | No |
| Everything5pounds.com | 2.9 million | No |
| Eatigo.com | 2.8 million | No |
| Katapult.com | 2.2 million | No |
| Wedmegood.com | 1.3 million | No |
| RedMart | 1.1 million | Yes |
| Coupontools.com | 1 million | No |
| W3layouts.com | 789 thousand | No |
| Game24h.vn | 779 thousand | No |
| Invideo.io | 571 thousand | No |
| Apps-builder.com | 386 thousand | No |
| Fantasycruncher.com | 227 thousand | No |
| Athletico.com.br | 162 thousand | No |
| Toddycafe.com | 129 thousand | No |
According to the seller, the following information is exposed per breach:
From the samples of each database seen by BleepingComputer, we have confirmed that exposed email addresses correspond to accounts for thirteen of the allegedly seventeen breached services. We could not verify accounts for Clip.mx, Katapult, CouponTools, or Aps-builder.com.
Also Read: Data Centre Regulations Singapore: Does It Help To Progress?
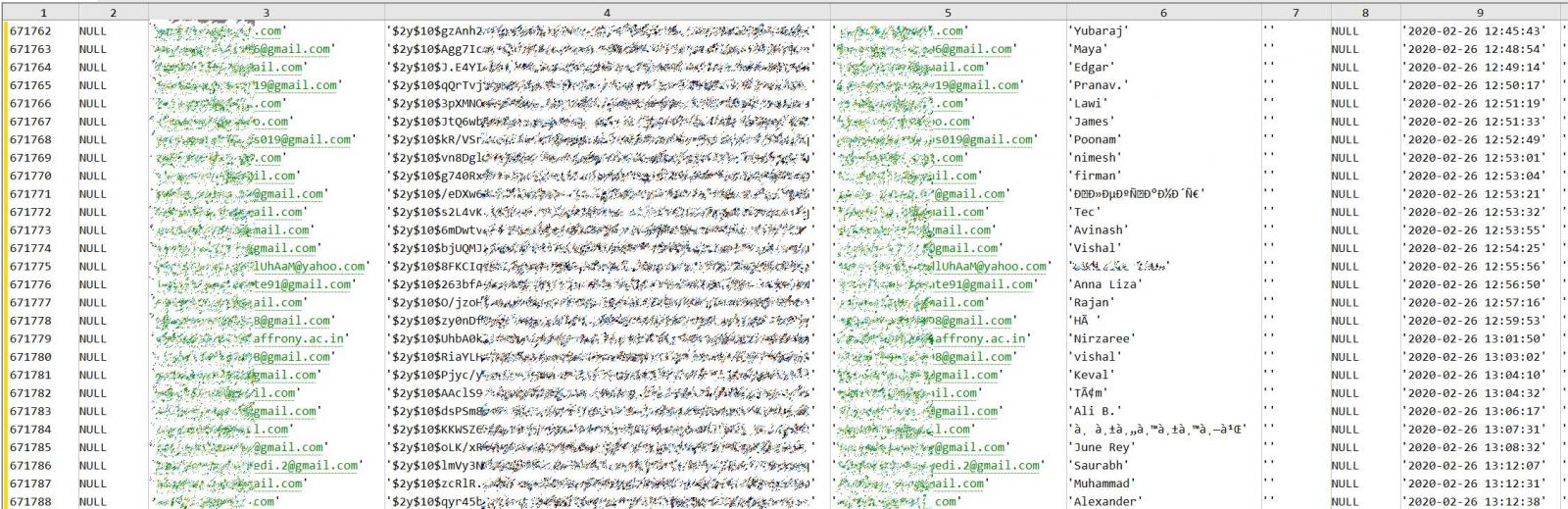
The combined databases expose over 34 million user records. While a password is not included in every record, for example, Clip.mx, there is still useful information disclosed in each database that threat actors can use.
BleepingComputer has contacted each of the companies being sold online and has only heard from Wongnai at this time.
Unfortunately, this lack of response is common when reporting data breaches, and a few weeks later, if not months later, the companies will eventually disclose the breach.
To be safe, if you are a user of one of these sites, you should assume that they have been breached and immediately change your password.
If you use the same password at other sites, you should also change the password at those sites to a unique and strong one that you only use for that site.
Using unique passwords at every site you have an account prevents a data breach at one site from affecting you at other websites you use.
It is suggested that you use a password manager to help you keep track of unique and robust passwords at every site.