KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Also Read: Top 3 Common Data Protection Mistakes, Revealed
The saga of what has been dubbed the biggest hack in the world of decentralized finance appears to be over as Poly Network recovered more than $610 million in cryptocurrency assets it lost two weeks ago and the hacker received a $500,000 bounty for returning the money.
Today, the hacker, referred to as Mr. White Hat, gave Poly Network access to the last tranche of stolen digital assets in their wallet, worth about $141 million.
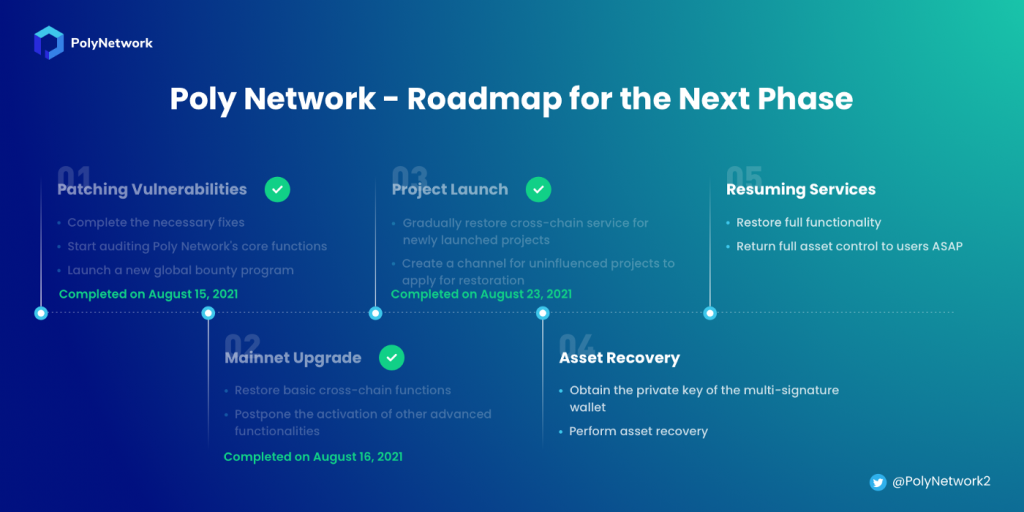
Poly Network has now moved to the “Asset Recovery” operation, the second last stage of bouncing back from the security breach it suffered before resuming all services.
The incident occurred on August 10, when an unknown party transferred into their wallets Binance Chain, Ethereum (ETH), and Polygon assets from the decentralized cross-chain protocol and network Polygon Network:
News quickly spread on the blockchains and the three wallet addresses used by the attacker were marked as PolyNetwork Exploiter to let exchanges know that the assets had been stolen and not to process any transactions.
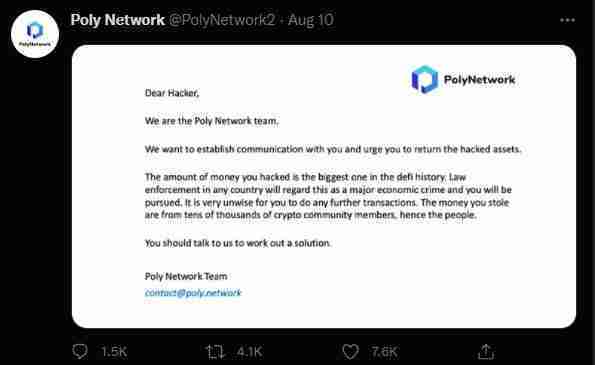
On the same day, Poly Network urged the hacker to return the hacked assets and said they were willing to talk things through to “work out a solution:”
Also Read: The Financial Cost of Ransomware Attack
It is unclear if this message influenced the hacker’s decision or the claims of the blockchain security company SlowMist that it had tracked the attacker’s email and IP addresses, and the device fingerprint, but Mr. White Hat announced the very next day that they would return all the stolen assets.
Mr. White Hat started with about $260 million worth of digital assets and today handed over to Poly Network a private key to the 3/4 multi-signature wallet, releasing the last portion of the loot, 28,953 ETH and 1,032 Wrapped Bitcoin (WBTC), worth about $141 million.
“At this point, all the user assets that were transferred out during the incident have been fully recovered. Thanks to Mr. White Hat’s cooperation, Poly Network has officially entered the fourth phase of our roadmap “Asset Recovery”. We are in the process of returning full asset control to users as swiftly as possible” – Poly Network
Poly Network’s “thank you” came in the form of about $500,000 (160 ETH) and an “invitation” for Mr. White Hat to become its Chief Security Advisor. The company also stated it had no intention to hold the hacker legally accountable.
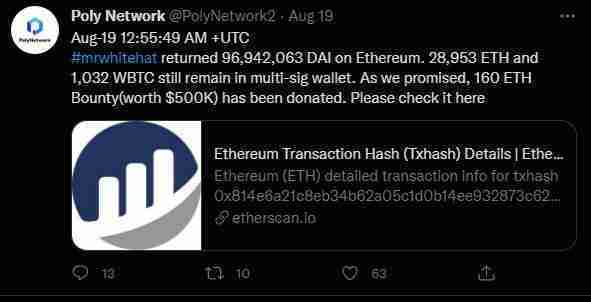
Poly Network kept its word and on August 19 transferred the160 ETH to a wallet address that the hacker had made public.
The response from the hacker about the job offer never came, though. Nor did their reply about the bug bounty.
Starting August 14, Poly Network started to document the progress it made since the attack in a series of updates on the Medium publishing platform [1, 2, 3, 4, 5, 6]. Today, the company announced that it started the full asset restoration process.
Also Read: Vulnerability Management For Cybersecurity Dummies
In about two weeks, Poly Network went from losing more than half a billion U.S. dollars to gaining worldwide notoriety not only for being the victim of the largest cryptocurrency heist by far, but also for recovering all the assets.
Furthermore, the company decided to let bygones be bygones and not follow legal action against the hacker but offer them a top security job and $500,000.
The reward may seem small in contrast with the value of the stolen assets but it is a hefty pile when you think that the hacker might not have been able to spend a dime from the loot.