KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





More than two dozen SQL databases stolen from online shops in various countries are being offered for sale on a public website. In total, the seller provides over 1.5 million rows of records but the amount of stolen data is much larger.
The attacker is hacking into insecure servers that are reachable over the public web, copies the databases, and leaves a note asking for a ransom in return of the stolen data.
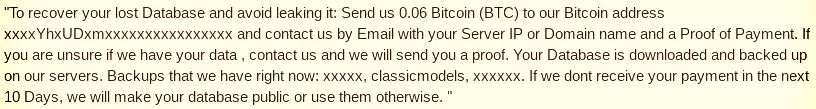
Victims have 10 days to pay BTC 0.06 ($525 at current price) a wallet provided in the ransom note, else the hacker makes the database public or uses it as they please.
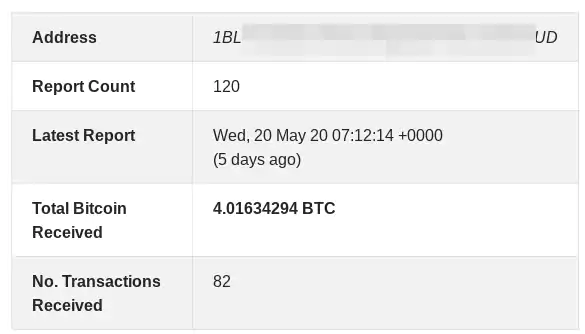
A couple of wallets used by the attacker recorded more than 100 received transactions for a combined total of BTC 5.8 (currently worth a little over $51,000).
The number of abuse reports for these two wallets is over 200, the oldest being from September 20, 2019. The most recent one is from May 20 and this month alone there were nine reports, indicating that the actor is highly active.
It is important to note that the hacker may use more than the wallets found by BleepingComputer. Also, the number of abuse reports for the bitcoin addresses used by hacker are not indicative of the full activity of the operation. Not all victims report the attacker and some decide to pay the ransom.
There are 31 databases listed on the website, although judging from the number of abuse reports, this is clearly just a small portion. The most recent one is from March, and all have a sample attached for the potential buyers to check.
Two more databases are unlisted, one of them advertised in April on a hacker forum, and another stored in the “/samples” directory of the website.
More than half of the listed databases are from online stores in Germany; others are from Brazil, the U.S., Italy, India, Spain, and Belarus. All run e-commerce platforms like Shopware, JTL-Shop, PrestaShop, OpenCart, Magento v1 and v2).
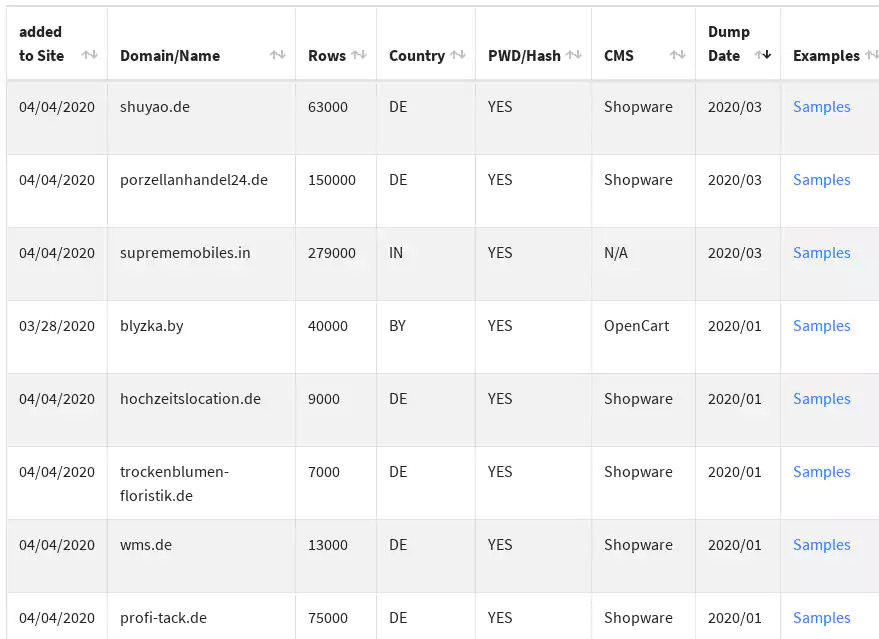
The total number of rows available in these databases is around 1,620,000. Depending on the store, the data contains email addresses, names, hashed passwords (e.g. bcrypt, MD5), postal addresses, gender, dates of birth.
Some of the databases have a dump date from 2016 but the site seems to have been populated starting March 28, 2020.
This type of attack is reminiscent of the MongoDB ransom attacks that peaked in 2017 and continued through 2019 (1, 2, 3, 4); and here’s an old one targeting MySQL servers.
Guardicore researcher Ophir Harpaz spotted at the beginning of the year a ransomware campaign targeting MySQL servers. The intruders brute-forced they way into the server and encrypted the databases; then they created a ‘Warning’ table to drop their ransom note. About 50 attacks were detected.
Databases are still attractive to cybercriminals. Despite having a low financial value compared to other types of extortion, the crooks can increase their profits by selling the data to multiple parties, including the victim.
h/t Ninja Null

Maze ransomware operators have published credit card data stolen from the Bank of Costa Rica (BCR). They threaten to leak similar files every week.
The hackers are doing this in support of their claim to have breached BCR in the past and the bank’s denial of these intrusions.
In a post on their “leak” site this week, Maze operators shared a 2GB spreadsheet with payment card numbers from customers of Banco de Costa Rica.
The attackers say that they released the data because they are not looking to make any profit off it. Instead, they want to draw attention to the bank’s security lapses when it comes to protecting sensitive information.
Several screenshots from the database accompany the announcement, showing unencrypted credit card numbers. Together, the images contain data for at least 50 cards (some are listed multiple times). Previously, they published over 100 partial numbers (last four digits removed) with expiration date and verification codes.
BleepingComputer checked several numbers with two online validation services and most of them passed the check. Bank identification number (BIN) details showed that they were Visa or MasterCard debit cards issued by BCR.
It should be noted that one of the card validation sites states that the validity of a number does not guarantee that it is also in use. However, the details were confirmed when verified on a second online checker.
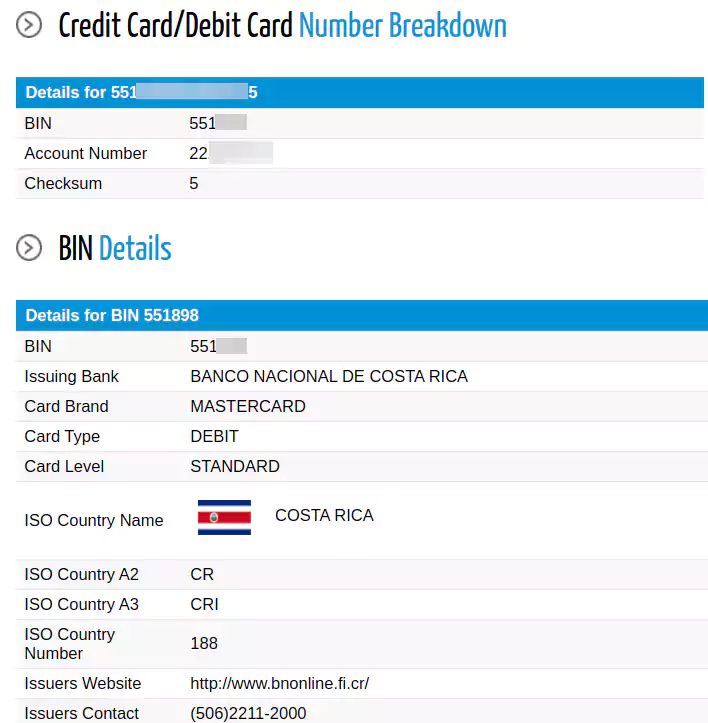
On April 30, Maze ransomware operators claimed to have more than 11 million cards from BCR, with 4 million being unique and 140,000 belonging to “US citizens.”
Maze said that they first gained access to the bank’s network in August 2019 and again in February 2020, to check if security had improved.
They chose to exit without encrypting the systems the second time because it “was at least incorrect during the world pandemic” and “the possible damage was too high.” But they did not leave empty-handed.
BleepingComputer contacted BCR on May 1 to confirm either of the two incidents but received no reply. However, the bank issued a public statement that day saying that following an “exhaustive verification” they can “firmly confirm that the institution’s systems have not been violated.”AD
In response, Maze released four days later a spreadsheet with details about systems they claim to be from BCR’s network. On May 21 they dumped the payment card data.
The bank issued another statement on May 22 reiterating that multiple analyses from internal and external specialists confirmed that the systems were not accessed without authorization and that clients’ transactions were not impacted.
At the beginning of the month, Maze told BleepingComputer that they reached out to the bank multiple times with a ransom demand and that they may sell the card data on the dark web.
Even if they spared BCR’s systems from encryption, the ransom was for showing the institution the vulnerable spots on its network.

Online education site EduCBA has started notifying customers that they are resetting their passwords after suffering a data breach.
EduCBA is an online education site based out of India that offers over 2,500 online courses and job oriented learning programs focus on finance, technology, and business to their 500,000 learners.
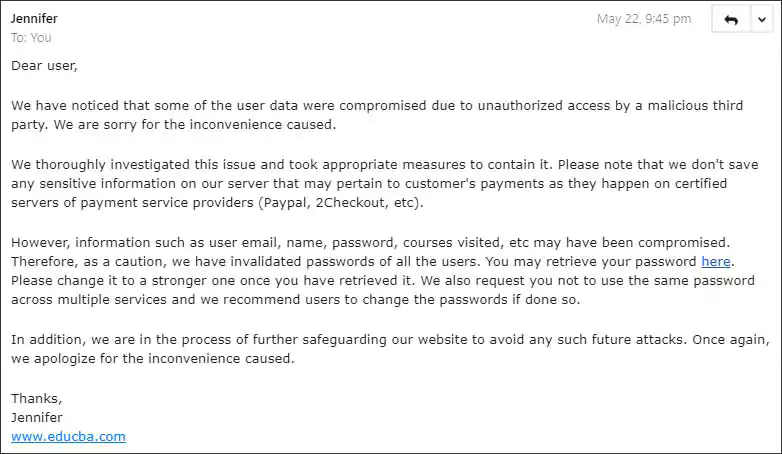
Yesterday, EduCBA began emailing data breach notifications to customers stating that their systems were hacked and user data was exposed.
The notification is a bit strange as it does not go into great detail about what information was stolen and simply states, “email, name, password, courses visited, etc may have been compromised.”
BleepingComputer has emailed EduCBA to clarify what other information is referenced by ‘etc’ but has not heard back as of yet.
They have stated that no financial information was accessed as they use third-party processors such as PayPal and 2Checkout to process payments.
As a precaution, EduCBA states that they have reset all user’s passwords.
“Therefore, as a caution, we have invalidated passwords of all the users. You may retrieve your password here,” the data breach notification reads.
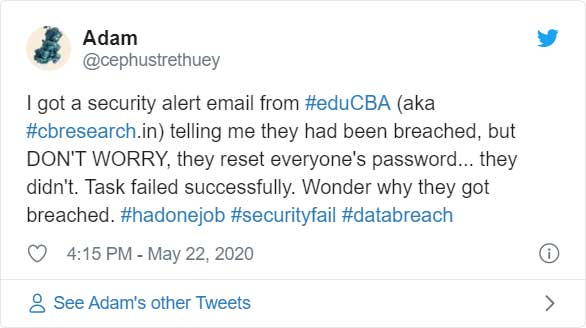
A comment on twitter, though, states that the password for their account was not reset.
If you have an account at EduCBA, you should immediately change your password to a unique one only used at that site.AD
If your EduCBA password was used at other sites, it is strongly advised that you change the passwords at these sites to a strong and unique one as well.