KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Chinese-speaking cyberspies have targeted Southeast Asian governmental entities and telecommunication companies for more than a year, backdooring systems running the latest Windows 10 versions with a newly discovered rootkit.
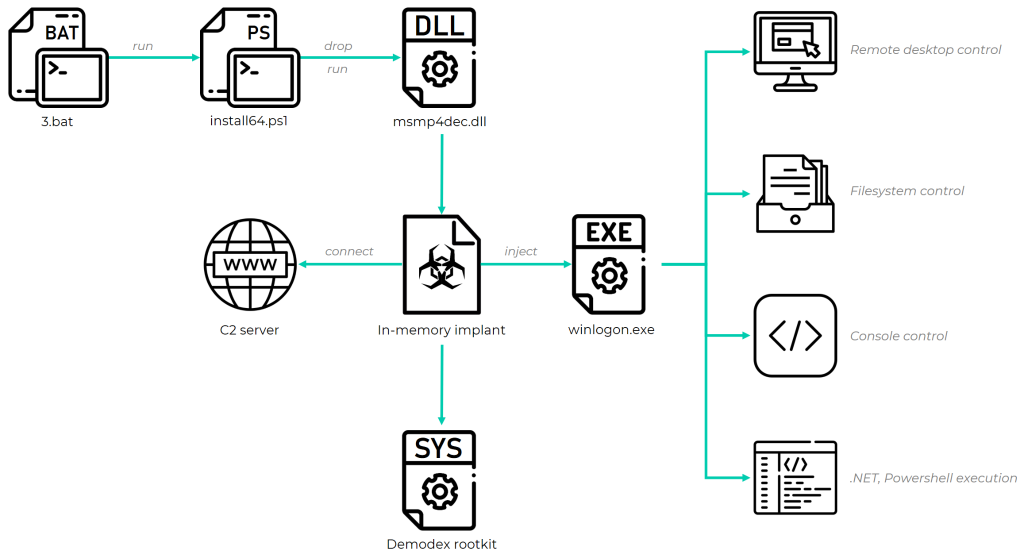
The hacking group, dubbed GhostEmperor by Kaspersky researchers who spotted it, use the Demodex rootkit, which acts as a backdoor to maintain persistence on compromised servers.
This rootkit’s primary goal is to hide malware artifacts (including files, registry keys, and network traffic) to evade detection by both forensic investigators and security products.
“To bypass the Windows Driver Signature Enforcement mechanism, GhostEmperor uses a loading scheme involving a component of an open-source project named ‘Cheat Engine’, “Kaspersky said in July when it released the first details regarding this threat actor.
Also Read: Overview of the Personal Data Protection Act – SG
“This advanced toolset is unique and Kaspersky researchers see no similarity to already known threat actors. Kaspersky experts have surmised that the toolset has been in use since at least July 2020.”
To breach their victims’ servers, the threat actors exploited known vulnerabilities in Internet-facing server software, including Apache, Window IIS, Oracle, and Microsoft Exchange (the latter hit two days after the ProxyLogon bugs were publicly disclosed).
GhostEmperor also uses a “sophisticated multi-stage malware framework” that allows the attackers with remote control capabilities over breached devices to provide remote control over the attacked servers.
GhostEmperor operators showed that they are “accomplished in their craft” and with a significant set of skills highlighted through the use of both sophisticated and uncommon anti-analysis and anti-forensic techniques.
While the vast majority of their attacks were focused on telecom firms and government organizations from South East Asia (e.g., Malaysia, Thailand, Vietnam, Indonesia), the researchers also observed targeting of other geopolitical areas, including countries like Egypt, Ethiopia, and Afghanistan.
Also Read: 5 ways on how to destroy documents securely to prevent data breach
“We observed that the underlying actor managed to remain under the radar for months, all the while demonstrating a finesse when it came to developing the malicious toolkit, a profound understanding of an investigator’s mindset and the ability to counter forensic analysis in various ways,” Kaspersky concluded.
“The attackers conducted the required level of research to make the Demodex rootkit fully functional on Windows 10, allowing it to load through documented features of a third-party signed and benign driver.
“This suggests that rootkits still need to be taken into account as a TTP during investigations and that advanced threat actors, such as the one behind GhostEmperor, are willing to continue making use of them in future campaigns.”
Further technical details regarding GhostEmperor’s tactics and the Demodex rootkit can be found in Kaspersky’s deep dive and report.