KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Two widely used walk-through metal detectors made by Garrett are vulnerable to many remotely exploitable flaws that could severely impair their functionality, thus rendering security checkpoints deficient.
Garrett is a well-known US-based manufacturer of hand-held and walk-through metal detectors commonly deployed in security-critical environments such as sports venues, airports, banks, museums, ministries, and courthouses.
Security researchers at Cisco Talos have discovered numerous vulnerabilities that could allow attackers to execute commands or read/modify information on the Garret iC Module version 5.0, which is the component that provides network connectivity to Garrett PD 6500i and Garrett MZ 6100.
Also Read: Ways to protect HR data and avoid penalties for data breaches
The nine vulnerabilities disclosed in detail by Cisco Talos are:
In CVE-2021-21901 and CVE-2021-21903, the iC Module exposes a discovery service on UDP port 6977. This opens up an exploitation path by broadcasting a specially-formatted UDP packet, forcing a reply with sensitive information.
Using this info, an attacker could craft a UDP packet with a sufficiently long CRC field leading to a buffer overflow, allowing remote code execution before any authentication.
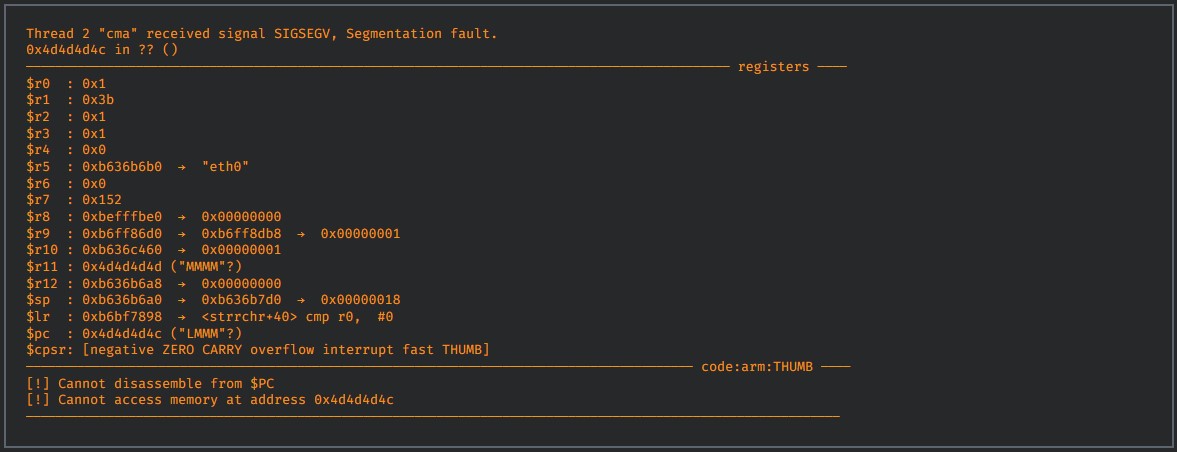
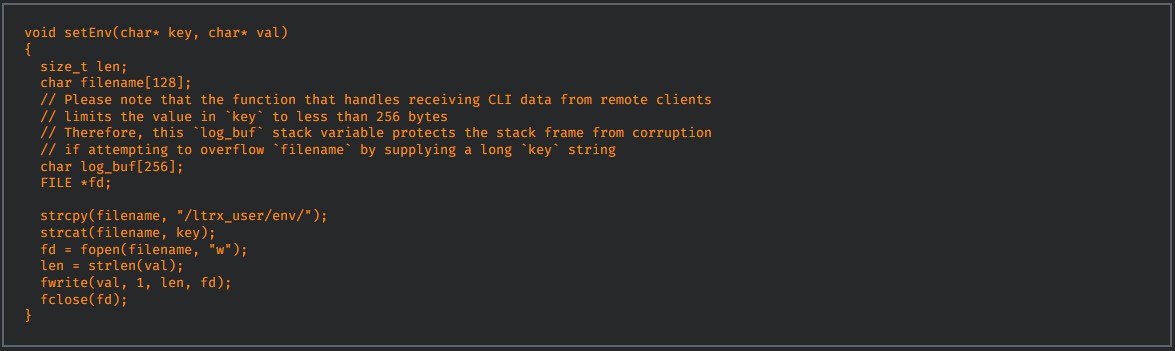
In CVE-2021-21904, the iC Module exposes an authenticated CLI over TCP port 6877. After a client authenticates, they are allowed to send plain-text commands to the device, and one of the potential commands is the creation of new “environment variables.”
Also Read: Data Protection Act of Singapore: Validity in the Post-pandemic World
These variables are underpinned by a key parameter, which is not sanitized or validated. As such, it can lead to unauthenticated arbitrary file creation and code execution as the root user.
Cisco Talos disclosed the above flaws to Garrett on August 17, 2021, and the vendor fixed the identified issues on December 13, 2021.
Admins of walk-through Garrett Metal detectors are urged to upgrade their iC Module CMA software to the latest available version to resolve these vulnerabilities.
If you are unsure how to do that, contact your Garrett sales representative and ask for guidance.
As these vulnerabilities require access to the network used by the metal detector, they will not likely be targeted in mass by threat actors. However, insider threats continue to be a problem and are usually not detected until after the damage is done.
The US government recently warned about insider threats and released a self-assessment tool to help organizations determine their risk posture to insider attacks.
BleepingComputer has reached out to Garrett to learn more about the impact of these vulnerabilities but has not heard back.