





The Fonix Ransomware operators have shut down their operation and released the master decryption allowing victims to recover their files for free.
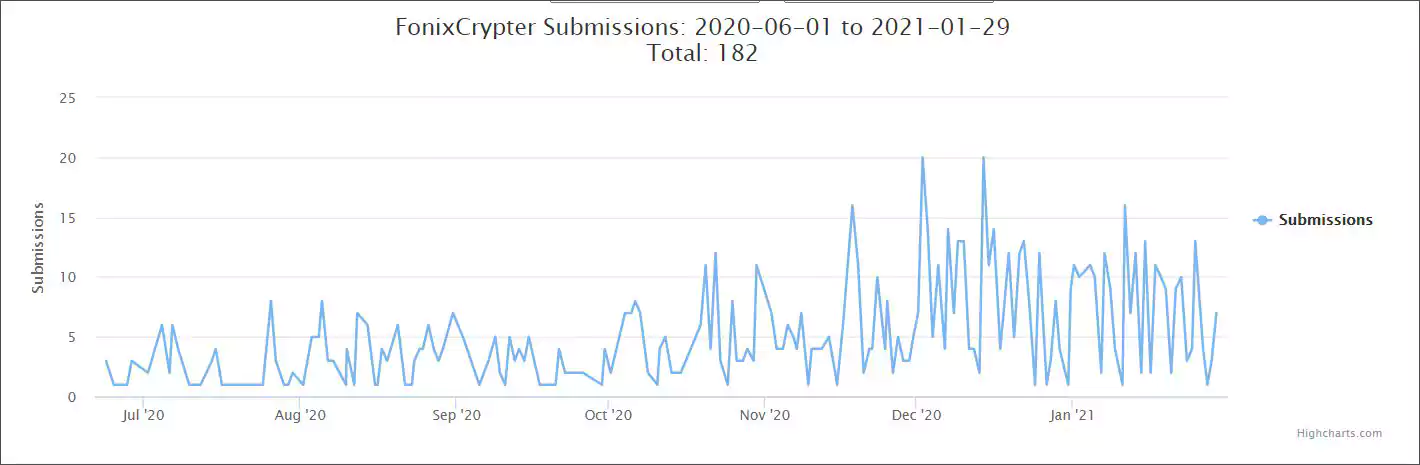
Fonix Ransomware, also known as Xinof and FonixCrypter, began operating in June 2020 and has been steadily encrypting victims since. The ransomware operation was not as widely active as others, such as REvil, Netwalker, or STOP, but starting in November 2020, it picked up a bit, as shown by the ID Ransomware submissions below.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
This afternoon, a Twitter user claiming to be a Fonix ransomware admin announced that the ransomware had shut down.
The message shared in the image reads:
I’m one fonix team admins.
you know about fonix team but we have come to the conclusion.
we should use our abilities in positive ways and help others.
Also rans0mware source is completely deleted, but some of team members are disagree with closure of the project, like telegram channel admin who trying to scam people in telegram channel by selling fake source and data.
Anyway now main admin has decided to put all previous work aside and decrypt all infected systems at no cost.
And the decryption key will be available to the public.
The final statement of the team will be announced soon.Regards-FonixTeam
According to the message, some of the ‘members’ of the ransomware operation were not happy that it was shutting down.
This shutdown could cause members to join other ransomware affiliate programs or splinter off and create a new operation.
In a different tweet, the Fonix admin shared a link to a RAR archive named ‘Fonix_decrypter.rar’ containing both a decryptor and the master private decryption key.
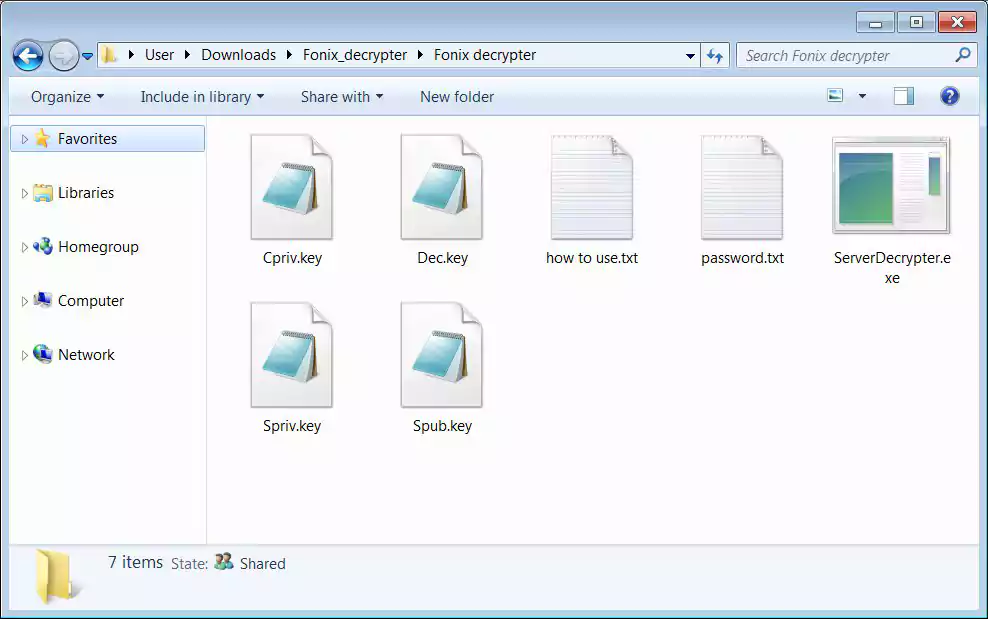
This decryption tool is not a decryptor that can be used by a victim to decrypt their files easily but is instead an admin tool used internally by the ransomware gang.
Most ransomware operations allow victims to send a few encrypted files that they will decrypt for free to prove that they can do so.
The decryptor released tonight is the Fonix Ransomware operators’ tool when performing these free test decryption and does not allow a victim to decrypt an entire computer.
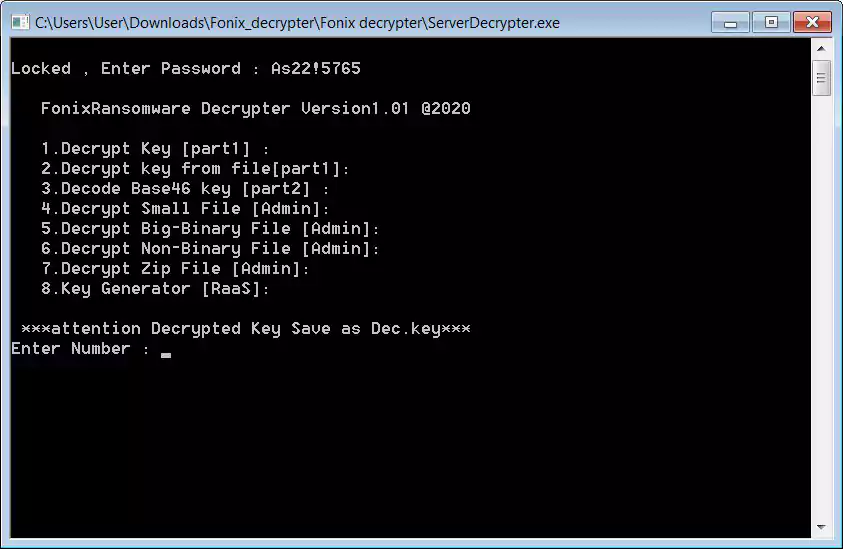
Even considering that it can only decrypt one file simultaneously, from our tests of the decryptor, it has very confusing instructions and is prone to crashing.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
The good news is that Michael Gillespie has told BleepingComputer that the master keys work but only on some Fonix ransomware versions.
However, Emisosft’s decryptor will decrypt all versions of the ransomware, which include the .Fonix, .FONIX, .repter, .XINOF encrypted file extensions.
There is no ETA as to when the decryptor will be released, but if you are a victim of this ransomware, a solution will be available soon.