KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





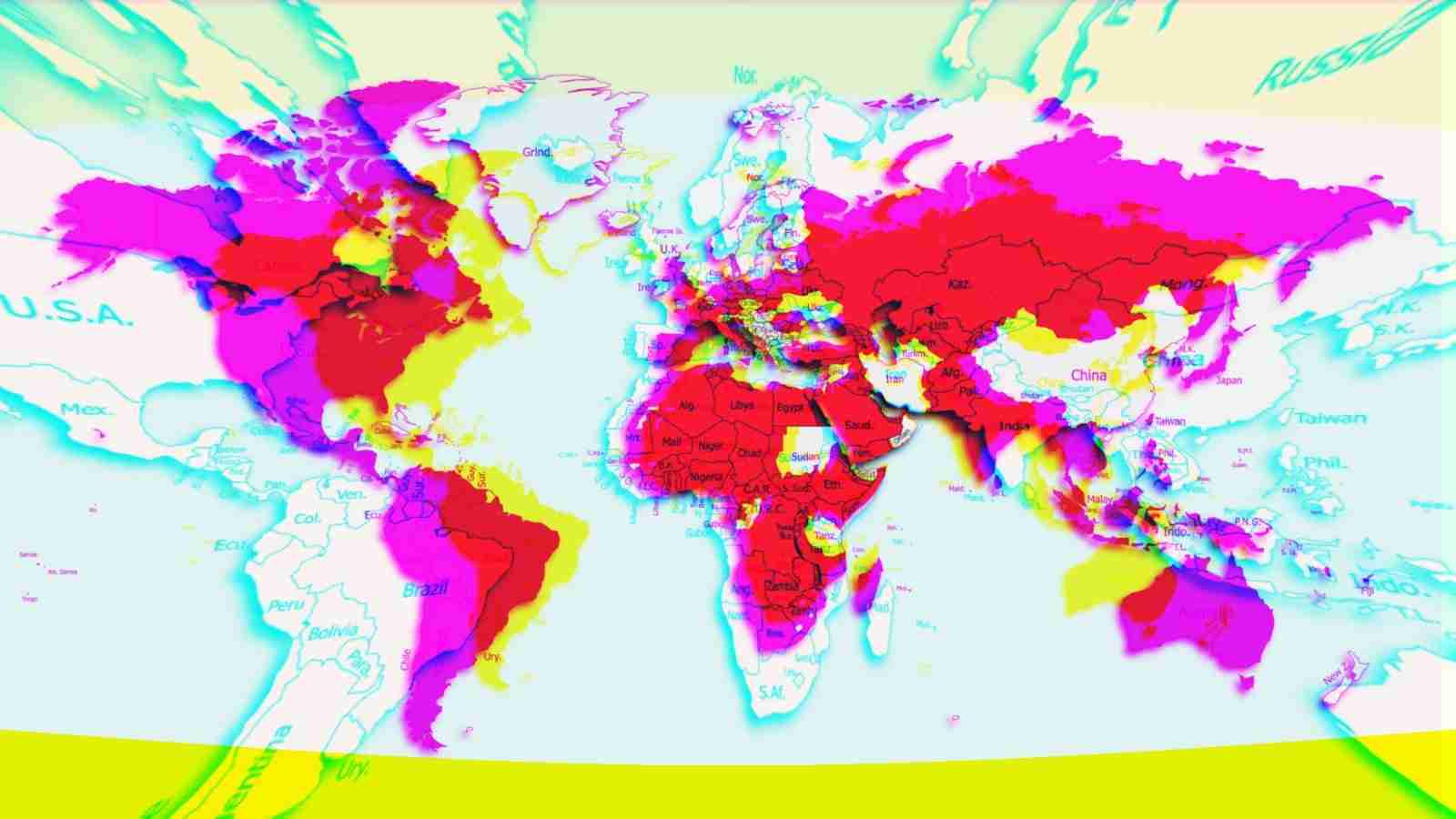
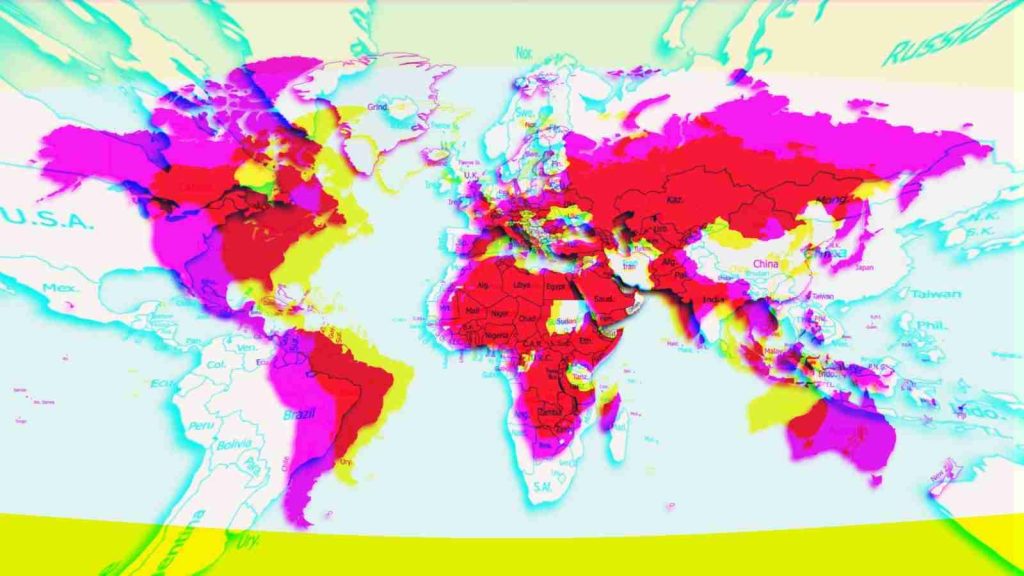
A new Android threat that researchers call FlyTrap has been hijacking Facebook accounts of users in more than 140 countries by stealing session cookies.
FlyTrap campaigns rely on simple social engineering tactics to trick victims into using their Facebook credentials to log into malicious apps that collected data associated with the social media session.
Researchers at mobile security company Zimperium detected the new piece of malware and found that the stolen information was accessible to anyone who discovered FlyTrap’s command and control (C2) server.
Also Read: The Top 4W’s of Ethical Hacking
FlyTrap campaigns have been running since at least March. The threat actor used malicious applications with high-quality design, distributed through Google Play and third-party Android stores.
The lure consisted of offers for free coupon codes (for Netflix, Google AdWords) and voting for the favorite soccer team or player, in tune with the delayed UEFA Euro 2020 competition.
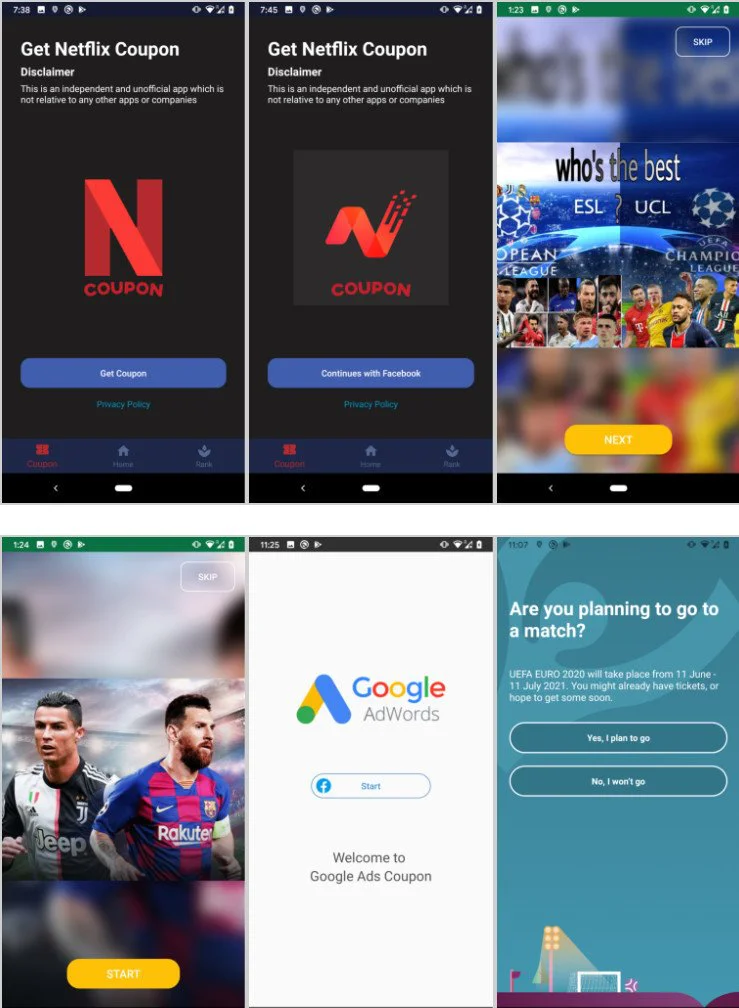
Getting the promised reward required logging into the app using Facebook credentials, authentication occurring on the legitimate social media domain.
Since the malicious apps use the real Facebook single sign-on (SSO) service, they can’t collect users’ credentials. Instead, FlyTrap relies on JavaScript injection to harvest other sensitive data.
“Using this technique, the application opens the legit URL inside a WebView configured with the ability to inject JavaScript code and extracts all the necessary information such as cookies, user account details, location, and IP address by injecting malicious JS code”
All the information collected this way goes to FlyTrap’s C2 server. More than 10,000 Android users in 144 countries fell victim to this social engineering.
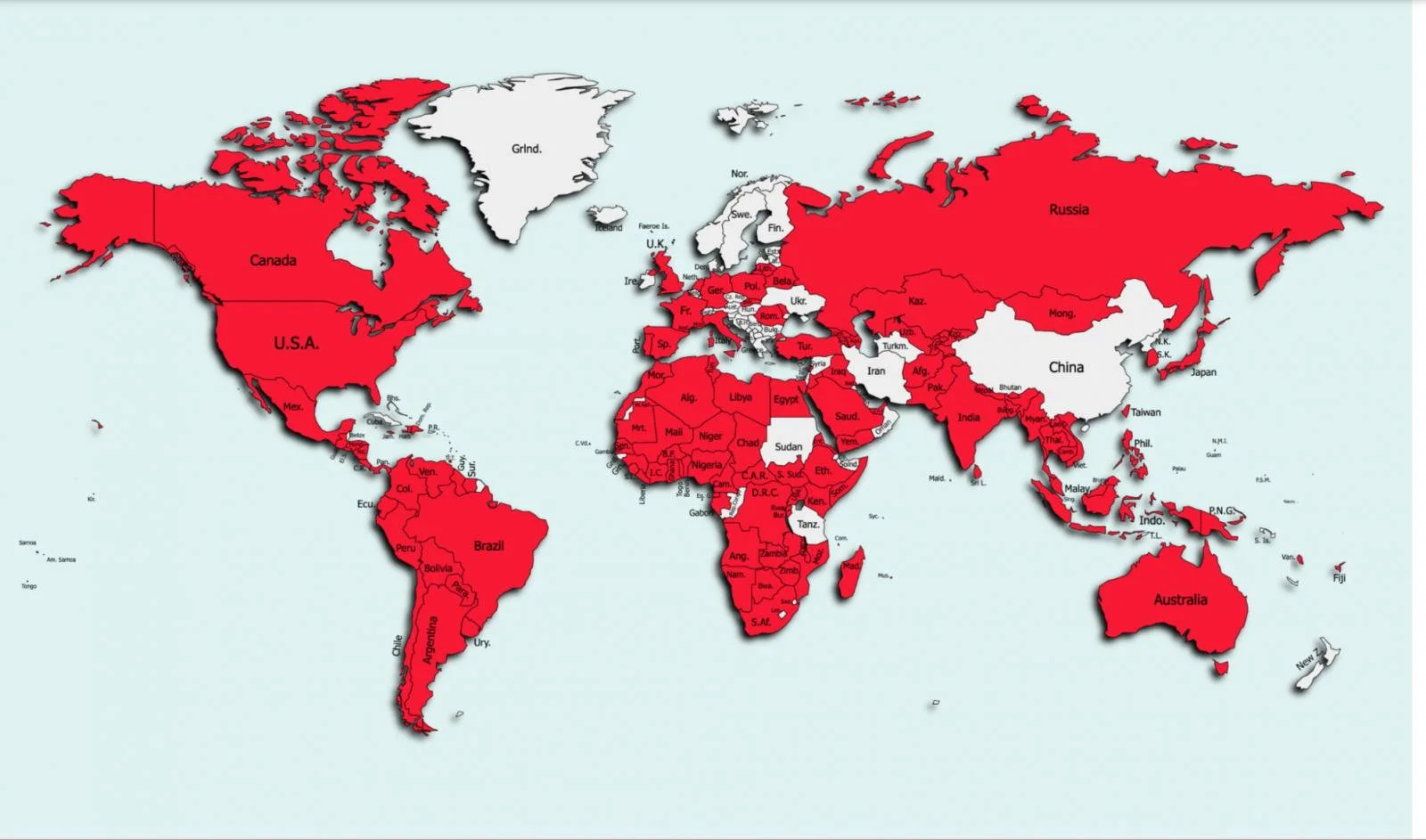
The numbers come straight from the command and control server, which the researchers were able to access because the database with the stolen Facebook session cookies was exposed to anyone on the internet.
Zimperium’s Aazim Yaswant says in a blog post today that FlyTrap’s C2 server had multiple security vulnerabilities that facilitated access to the stored information.
The researcher notes that accounts on social media platforms are a common target for threat actors, who can use them for fraudulent purposes like artificially boosting the popularity of pages, sites, products, misinformation, or a political message.
He highlights the fact that phishing pages that steal credentials are not the only way to log into the account of an online service. Logging onto the legitimate domain can also come with risks.
“Just like any user manipulation, the high-quality graphics and official-looking login screens are common tactics to have users take action that could reveal sensitive information. In this case, while the user is logging into their official account, the FlyTrap Trojan is hijacking the session information for malicious intent” – Aazim Yaswant, Android malware researcher, Zimperium
Despite not using a new technique, FlyTrap managed to hijack a significant number of Facebook accounts. With a few modifications, it could turn into a more dangerous threat for mobile devices, the researcher says.
Also Read: Protecting Data Online in the New Normal