KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







One of the largest Vietnamese crypto trading platforms, ONUS, recently suffered a cyber attack on its payment system running a vulnerable Log4j version.
Soon enough, threat actors approached ONUS to extort a $5 million sum and threatened to publish customer data should ONUS refuse to comply.
After the company’s refusal to pay the ransom, threat actors put up data of nearly 2 million ONUS customers for sale on forums.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
On December 9th, the PoC exploit for the notorious Log4Shell vulnerability (CVE-2021-44228) leaked on GitHub. And, that got the attention of opportunistic attackers who began mass-scanning the internet for vulnerable servers.
Between December 11th and 13th, threat actors successfully exploited the Log4Shell vulnerability on a Cyclos server of ONUS and planted backdoors for sustained access.
Cyclos provides a range of point-of-sale (POS) and payment software solutions, and like most vendors, was using a vulnerable log4j version in their software.
Although Cyclos did issue an advisory on the 13th and reportedly informed ONUS to patch their systems, it was too late.
Despite ONUS having patched their Cyclos instance, the exposure window allowed sufficient time for threat actors to exfiltrate sensitive databases.
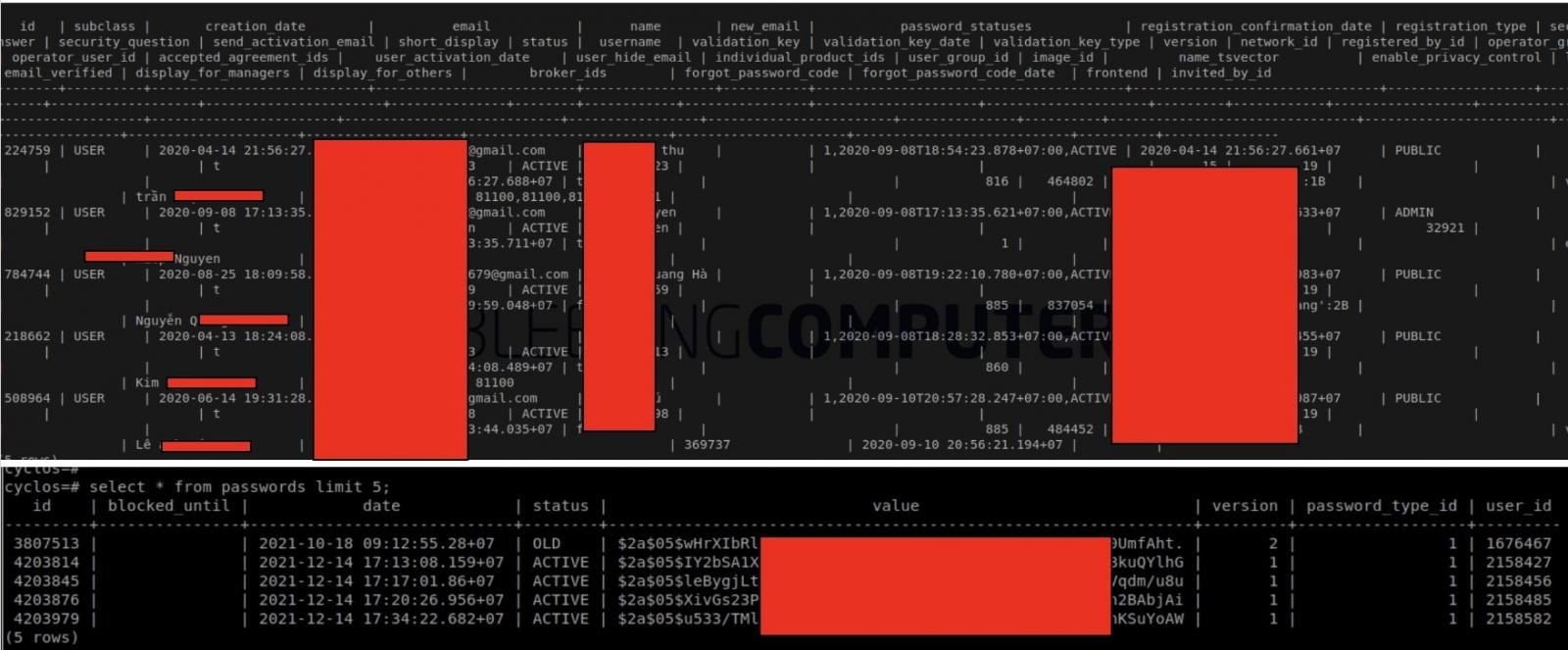
These databases contained nearly 2 million customer records including E-KYC (Know Your Customer) data, personal information, and hashed passwords.
E-KYC workflows used by banks and FinTech companies typically involve procuring some form of identification documents and proofs from the customers, along with a ‘video selfie’ for automated verification.
Interestingly, the Log4Shell vulnerability existed on a sandbox server used “for programming purposes only” but allowed attackers further access into sensitive data storage locations (Amazon S3 buckets) with production data, due to a system misconfiguration.
ONUS was then reportedly slapped with a $5 million extortion demand that they declined to meet. Instead, the company chose to disclose the attack to their customers via a private Facebook group.
“As a company that puts safety first, we are committed to providing our customers with transparency and integrity in business operations,” stated ONUS CEO Chien Tran.
“That is why, after careful consideration, the right thing we need to do now is to inform the entire ONUS community about this incident.”
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
The hack itself is a little more than just a Log4j problem alone. Log4j exploit may have been the entry point for attackers, but improper access control on ONUS’ Amazon S3 buckets allowed attackers undue access.
“The hacker took advantage of a vulnerability in a set of libraries on the ONUS system to get into the sandbox server (for programming purposes only),” explains ONUS.
“However, due to a configuration problem, this server contains information that gave bad guys access to our data storage system (Amazon S3) and stole some essential data. This leads to the risk of leaking the personal information of a large number of users.”
The customer information retrieved by threat actors includes:
Cybersecurity firm CyStack, which provided services to ONUS, has conducted a thorough investigation and released their findings on the attack mechanics and the backdoor planted by the attackers.
By December 25th, after failing to secure the extortion amount from ONUS, threat actors put up the customer data for sale on a data breach marketplace, as seen by BleepingComputer:
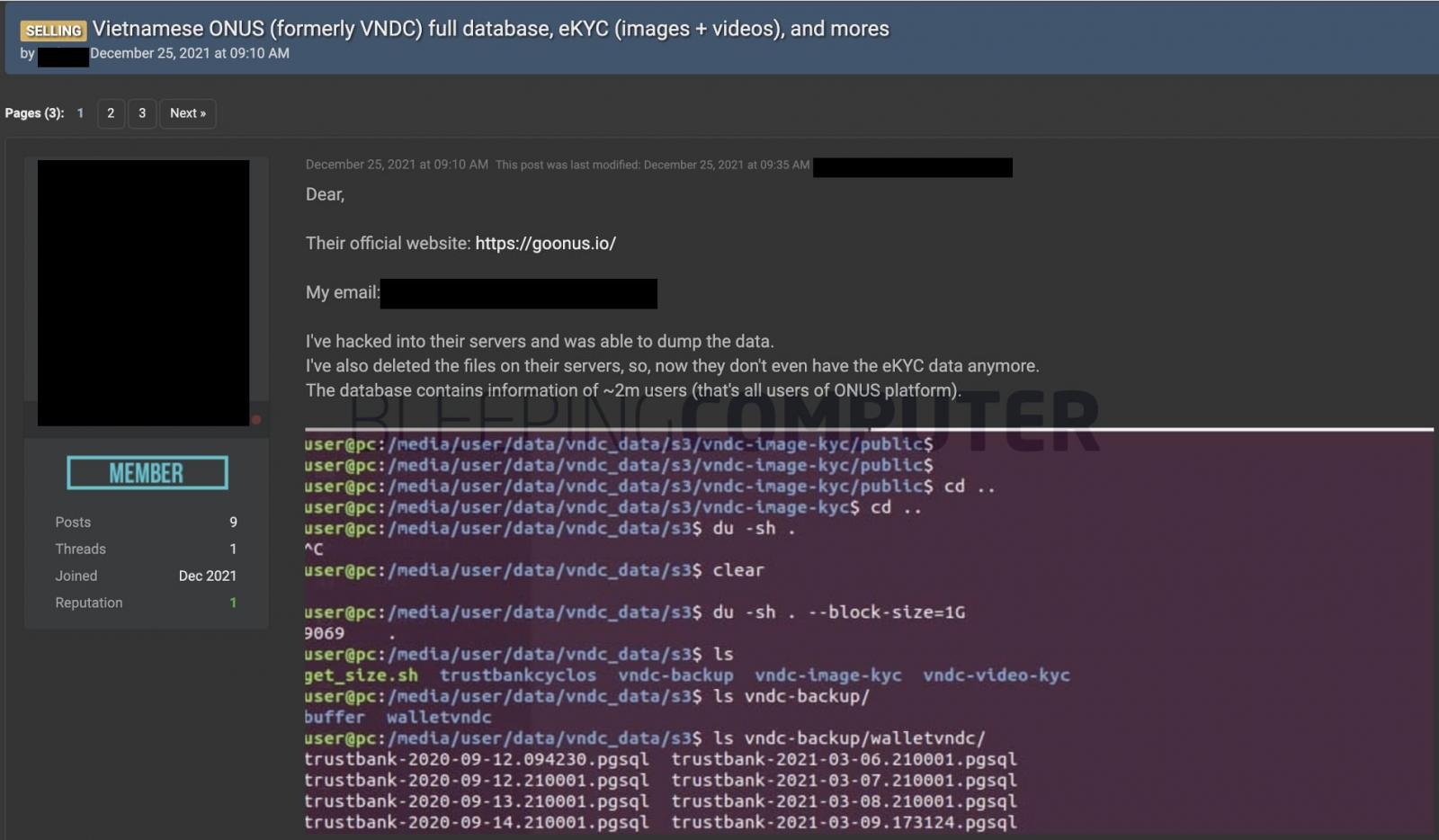
Threat actors claim to have copies of 395 ONUS database tables with customers’ personal information and hashed passwords in their possession.
Samples of such data published in the forum post were seen by BleepingComputer.
The samples also included unredacted images of customers’ ID cards, passports, and customer-submitted video selfie clips procured during the KYC process.
“We sincerely apologize and hope for your understanding,” states ONUS.
“This is also an opportunity for us to review ourselves, upgrade and further perfect the system to assure the safety of our users, especially during the transition from VNDC to ONUS.”
CyStack’s recommendations to ONUS included patching the Log4Shell vulnerability in Cyclos–as instructed by the vendor, deactivating leaked AWS credentials, properly configuring AWS access permissions, blocking public access to all sensitive S3 buckets, and imposing additional restrictions.
By now log4j vulnerabilities have been exploited by all kinds of threat actors from state-backed hackers to ransomware gangs and a few others to inject crypto miners on vulnerable systems.
The Conti ransomware gang has also been seen eying vulnerable VMWare vCenter servers for exploitation.
Log4j users should immediately upgrade to the latest version 2.17.1 (for Java 8) released yesterday. Backported versions 2.12.4 (Java 7) and 2.3.2 (Java 6) containing the fix are expected to be released shortly.