KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A financially motivated cybercrime gang has breached and backdoored the network of a US financial organization with a new malware known dubbed Sardonic by Bitdefender researchers who first spotted it.
FIN8, the threat actor behind this incident, has been active since at least January 2016 and is known for targeting retail, restaurant, hospitality, healthcare, and entertainment industries with the end goal of stealing payment card data from POS systems.
This threat actor’s malicious arsenal includes a large assortment of tools and tactics, ranging from POS malware (e.g., BadHatch, PoSlurp/PunchTrack, PowerSniff/PunchBuggy/ShellTea) to Windows zero-day exploits and spear-phishing.
Since FireEye first spotted them, FIN8 has orchestrated multiple large-scale but sporadic campaigns that impacted hundreds of organizations.
Also Read: 5 Workplace Tips: Protecting Information On Mobile Devices
Sardonic is a new C++-based backdoor the FIN8 threat actors deployed on targets’ systems likely via social engineering or spear-phishing, two of the group’s favorite attack methods.
While the malware is still under development, its functionality includes:
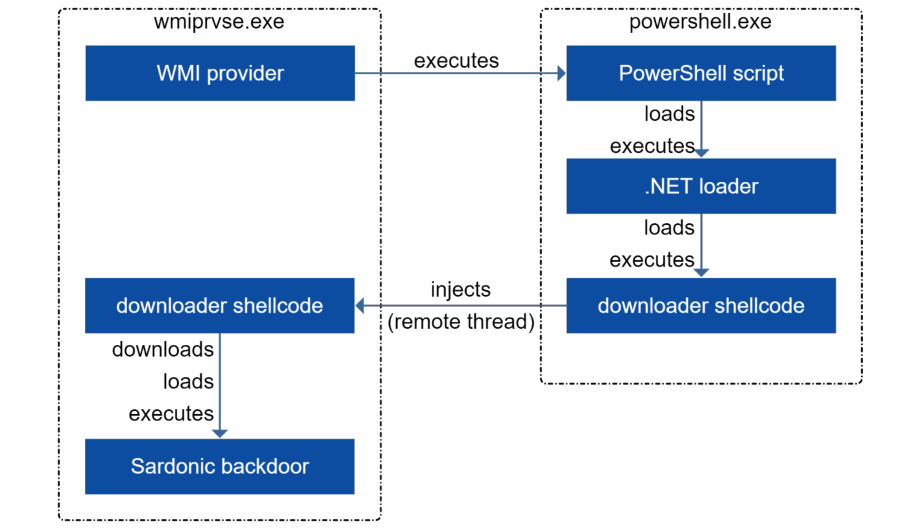
During their attack against the US bank, the backdoor was deployed and executed onto victims’ systems as part of a three-stage process using a PowerShell script, a .NET loader, and downloader shellcode.
As Bitdefender’s researchers observed, the PowerShell script is copied manually onto compromised systems, while the loaders are delivered onto compromised devices via an automated process.
FIN8 operators also tried multiple times to install the Sardonic backdoor on Windows domain controllers to escalate privilege and move laterally through the organization’s network.
Bitdefender urges organizations at risk of being targeted by FIN8 (primarily financial, retail, hospitality entities) to be on alert and check their networks for known FIN8 indicators of compromise.
“FIN8 continues to strengthen its capabilities and malware delivery infrastructure. The highly skilled financial threat actor is known to take long breaks to refine tools and tactics to avoid detection before it strikes viable targets,” Bitdefender’s Cyber Threat Intelligence Lab researchers concluded.
Also Read: The Role Of A DPO During Work From Home
“Bitdefender recommends that companies in target verticals (retail, hospitality, finance) check for potential compromise by applying [the IoCs] to their EDR, XDR and other security defenses.”
Additional details on Sardonic’s inner workings and indicators of compromise (IOCs), including infrastructure info and malware hashes, can be found at the end of Bitdefender’s whitepaper.