KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The U.S. Federal Bureau of Investigation (FBI) is warning the general public of the risks behind recently registered FBI-related domains that spoof some of the federal law enforcement agency’s official websites.
The warning comes in the form of a public service announcement issued through the FBI’s Internet Crime Complaint Center (IC3) earlier today.
“The Federal Bureau of Investigation (FBI) is issuing this announcement to help the public recognize and avoid spoofed FBI-related Internet domains,” the IC3 PSA reads.
“The FBI observed unattributed cyber actors registering numerous domains spoofing legitimate FBI websites, indicating the potential for future operational activity.”
Nation state-backed or financially motivated threat actors are frequently using such lookalike domains in attacks designed to harvest the targets’ credentials and financial information, to spread malware, as well as to propagate false information.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
Spoofed domains used in this type of attack are commonly created using misspelled versions of legitimate domains or switched top-level domains — in this case, .com or .net instead of the .gov one used by the FBI’s official U.S. government website.
The lookalike domains the FBI warns about can also be used to create spoofed emails that would allow attackers to persuade their victims to click and open malicious links and websites.
Additionally, “members of the public could unknowingly visit spoofed domains while seeking information regarding the FBI’s mission, services, or news coverage,” the FBI adds.
“The FBI urges all members of the American public to critically evaluate the websites they visit, and the messages sent to their personal and business email accounts, to seek out reliable and verified FBI information.”
The FBI also provides a list of recommendations to help the public spot these lookalike domains if they will get used in future malicious campaigns:
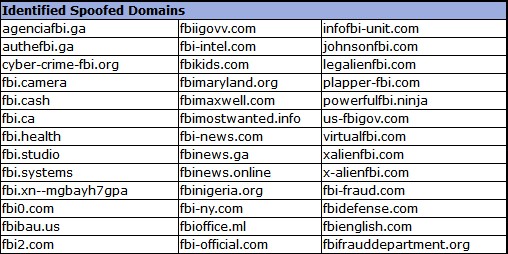
The FBI’s PSA also comes with an appendix of some examples of identified spoofed FBI-related Internet domains with dozens of such domains detected recently and possibly being prepared for future attacks.
Although there are no signs at the moment that the lookalike domains have already been used in attacks, they could be used by both nation state-backed hacking groups or cyber-criminals as part of espionage or financially motivated campaigns targeting businesses and individuals.
fbi-news.com, fbi-intel.com, fbimaryland.org, fbi-fraud.com, fbi-ny.com, fbi-gov.network, fbiusagov.com, fbiusgov.com, fbiusa.net, fbi-usa.us, and fbihelp.org are just a few of the most interesting and potentially most dangerous ones if used in future malicious campaigns.
Last month, the FBI also warned of the potential use of spoofed US Census Bureau domains in future malicious campaigns for phishing and credential theft.
While previously it was quite easy to register a fraudulent .gov domain, starting with March 2020 the U.S. government made it a lot harder for unauthorized organizations or individuals to circumvent the official .gov registration process.
Entities who want to register a .gov domain now are required to use notarized signatures as part of the registration process for .gov domains to block attempts to use fake information on the authorization letter required by the U.S. General Services Administration (GSA) that oversees the DotGov Program.
Earlier this year, the Cybersecurity and Infrastructure Security Agency (CISA) also shared plans to take over the management of the .gov TLD from the GSA given that “the .gov top-level domain (TLD) is critical infrastructure for thousands of federal, state and local government organizations across the country.”
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
A bipartisan bill known as the “DOTGOV Act of 2019” was also introduced in Senate last year, seeking, among other things, to provide CISA with the authority to manage the .gov TLD after assuming governance from the GSA.