KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Federal Bureau of Investigation (FBI) email servers were hacked to distribute spam email impersonating FBI warnings that the recipients’ network was breached and data was stolen.
The emails pretended to warn about a “sophisticated chain attack” from an advanced threat actor known, who they identify as Vinny Troia. Troia is the head of security research of the dark web intelligence companies NightLion and Shadowbyte
The spam-tracking nonprofit SpamHaus noticed that tens of thousands of these messages were delivered in two waves early this morning. They believe this is just a small part of the campaign.
Researchers at the Spamhaus Project, an international nonprofit that tracks spam and associated cyber threats (phishing, botnets, malware), observed two waves of this campaign, one at 5 AM (UTC) and a second one two hours later.
The messages came from a legitimate email address – [email protected] – which is from FBI’s Law Enforcement Enterprise Portal (LEEP), and carried the subject “Urgent: Threat actor in systems.”
All emails came from FBI’s IP address 153.31.119.142 (mx-east-ic.fbi.gov), Spamhaus told us.
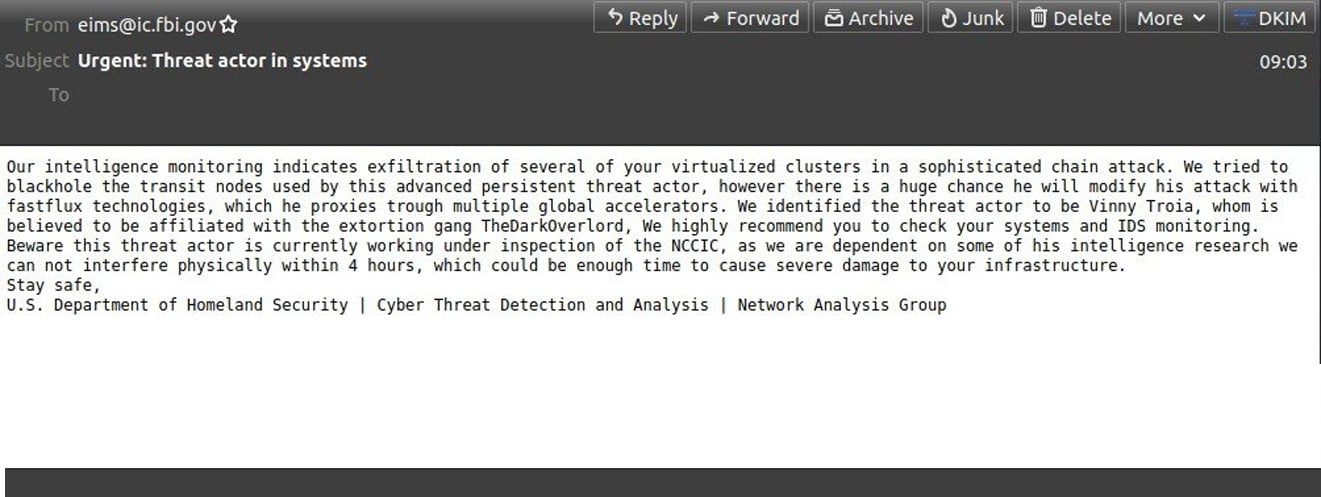
The message warns that a threat actors has been detected in the recipients’ network and has stolen data from devices.
Our intelligence monitoring indicates exfiltration of several of your virtualized clusters in a sophisticated chain attack. We tried to blackhole the transit nodes used by this advanced persistent threat actor, however there is a huge chance he will modify his attack with fastflux technologies, which he proxies trough multiple global accelerators. We identified the threat actor to be Vinny Troia, whom is believed to be affiliated with the extortion gang TheDarkOverlord, We highly recommend you to check your systems and IDS monitoring. Beware this threat actor is currently working under inspection of the NCCIC, as we are dependent on some of his intelligence research we can not interfere physically within 4 hours, which could be enough time to cause severe damage to your infrastructure.
Stay safe,
U.S. Department of Homeland Security | Cyber Threat Detection and Analysis | Network Analysis GroupSpamhaus Project told BleepingComputer that the fake emails reached at least 100,000 mailboxes. The number is a very conservative estimate, though, as the researchers believe “the campaign was potentially much, much larger.”
In a tweet today, the nonprofit said that the recipients were scraped from the American Registry for Internet Numbers (ARIN) database.
While this looks like a prank, there is no doubt that the emails originate from FBI’s servers as the headers of the message show that it’s origin is verified by the DomainKeys Identified Mail (DKIM) mechanism.
Received: from mx-east-ic.fbi.gov ([153.31.119.142]:33505 helo=mx-east.fbi.gov)
envelope-from
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=fbi.gov; s=cjis; t=1636779463; x=1668315463;
h=date:from:to:message-id:subject:mime-version;
bh=UlyBPHe3aElw3Vfnk/pqYLsBAoJGDFR1NyZFcSfpl5g=;
b=N3YzXzJEbQCTJGh8qqjkYu/A5DTE7yoloPgO0r84N+Bm2ae6f+SxzsEq
nbjnF2hC0WtiVIMMUVGzxWSiZjq1flEygQGI/JVjjk/tgVVPO5BcX4Os4
vIeg2pT+r/TLTgq4XZDIfGXa0wLKRAi8+e/Qtcc0qYNuTINJDuVxkGNUD
62DNKYw5uq/YHyxw+nl4XQwUNmQCcT5SIhebDEODaZq2oVHJeO5shrN42
urRJ40Pt9EGcRuzNoimtUtDYfiz3Ddf6vkFF8YTBZr5pWDJ6v22oy4mNK
F8HINSI9+7LPX/5Td1y7uErbGvgAya5MId02w9r/p3GsHJgSFalgIn+uY
Q==;
X-IronPort-AV: E=McAfee;i="6200,9189,10166"; a="4964109"
X-IronPort-AV: E=Sophos;i="5.87,231,1631577600";
d="scan'208";a="4964109"
Received: from dap00025.str0.eims.cjis ([10.67.35.50])
by wvadc-dmz-pmo003-fbi.enet.cjis with ESMTP/TLS/ECDHE-RSA-AES256-GCM-SHA384; 13 Nov 2021 04:57:41
+0000
Received: from dap00040.str0.eims.cjis (dap00040.str0.eims.cjis [10.66.2.72])
by dap00025.str0.eims.cjis (8.14.4/8.13.8) with ESMTP id 1AD4vf5M029322
for ; Fri, 12 Nov 2021 23:57:41 -0500
Date: Fri, 12 Nov 2021 23:57:41 -0500 (EST)
From: [email protected]
v=DMARC1; p=reject; rua=mailto:[email protected],mailto:[email protected]; ruf=mailto:[email protected]; pct=100Also Read: Free Privacy Policy Compliance Review
The headers also show the following FBI internal servers that processed the emails:
The FBI confirmed that the content of the emails is fake and that they were working on solving the issue as their helpdesk is flooded with calls from worried administrators.
In a statement to BleepingComputer, the FBI said that they could not share more information due to being an ongoing situation.
“The FBI and CISA are aware of the incident this morning involving fake emails from an @ic.fbi.gov email account. This is an ongoing situation and we are not able to provide any additional information at this time. We continue to encourage the public to be cautious of unknown senders and urge you to report suspicious activity to www.ic3.gov or www.cisa.gov.” – FBI.
Whoever is behind this campaign was likely motivated to discredit Vinny Troia, the founder of dark web intelligence company Shadowbyte, who is named in the message as the threat actor responsible of the fake supply-chain attack.
Members of the RaidForums hacking community have a long standing feud with Troia, and commonly deface websites and perform minor hacks where they blame it on the security researcher.
Tweeting about this spam campaign, Vinny Troia hinted at someone known as “pompomourin,” as the likely author of the attack. Troia says the individual has been associated in the past with incidents aimed at damaging the security researcher’s reputation.
Speaking to BleepingComputer, Troia said that “my best guess is ‘pompomourin’ and his band of minions [are behind this incident].”
“The last time they [pompompurin] hacked the national center for missing children’s we site blog and put up a post about me being a pedophile” – Vinny Troia
This assumption is further supported by the fact that ‘pompompurin’ contacted Troia a few hours before the spam email campaigns started to simply say “enjoy,” as a warning that something involving the researcher was about to happen.
Troia said that ‘pompompurin’ messages him every time they start an attack to discredit the researcher.
Update 11/13/21: Added statement from the FBI.