





Threat actors impersonated Truist, the sixth-largest US bank holding company, in a spear-phishing campaign attempting to infect recipients with what looks like remote access trojan (RAT) malware.
They also tailored the phishing campaign “to spoof the financial institution through registered domains, email subjects, and an application, all appearing to be related to the institution,” the FBI said in a TLP:WHITE private industry notification.
The PIN was released in coordination with DHS-CISA and is designed to provide security professionals and network admins with the indicators of compromise needed to detect and block such attacks.
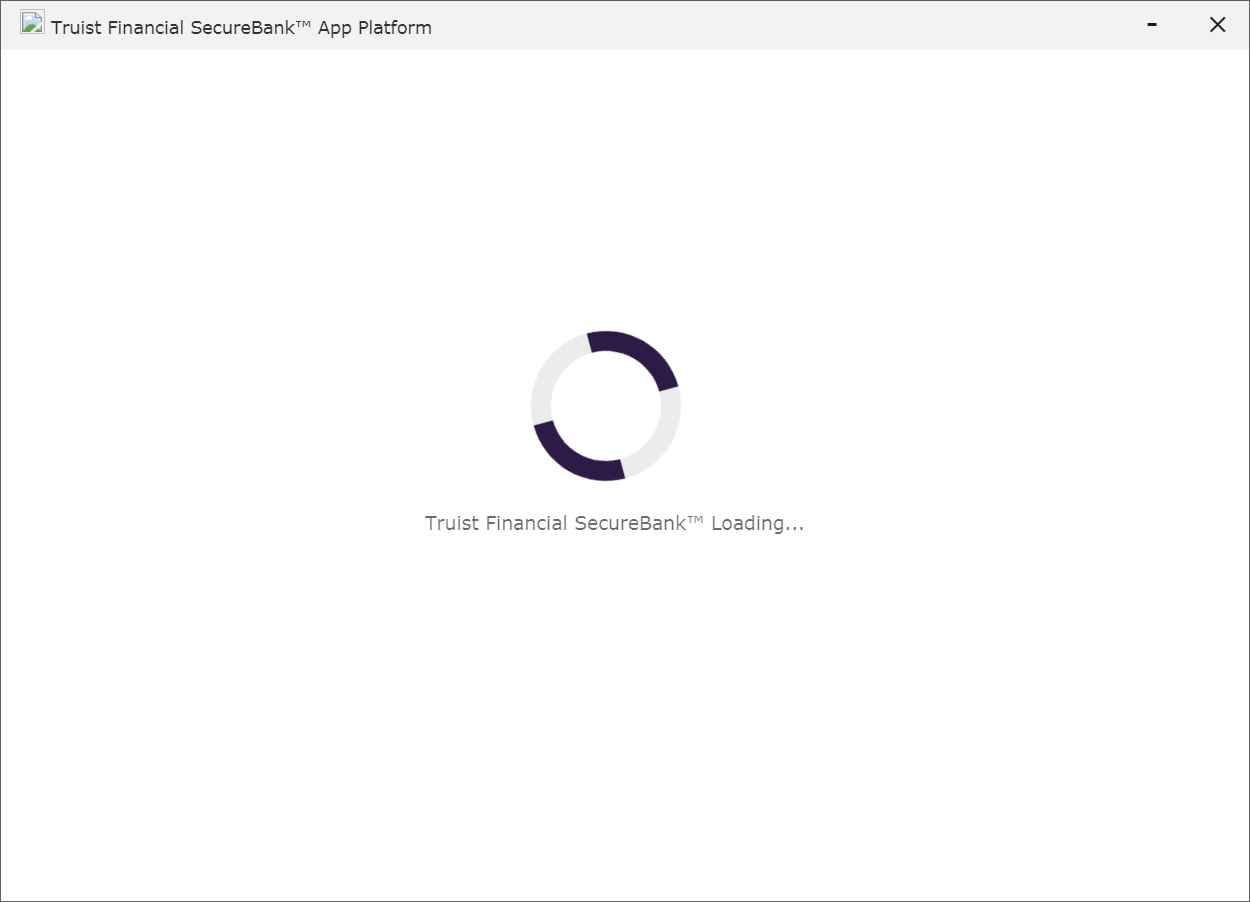
In one of the attacks targeting a renewable energy company in February 2021, the phishing emails instructed the target to download a malicious Windows app mimicking the legitimate Truist Financial SecureBank App and supposedly needed to complete the process behind a $62 million loan.
“The fraudulent loan amount was in line with the victim’s business model,” the FBI added. “The phishing e-mail also contained a link to download the application and a username and password for access.”
“The phishing e-mail appeared to originate from a United Kingdom-based financial institution, stating the US financial institution’s loan to the victim was confirmed and could be accessed through an application which appeared to represent the US financial institution.”
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
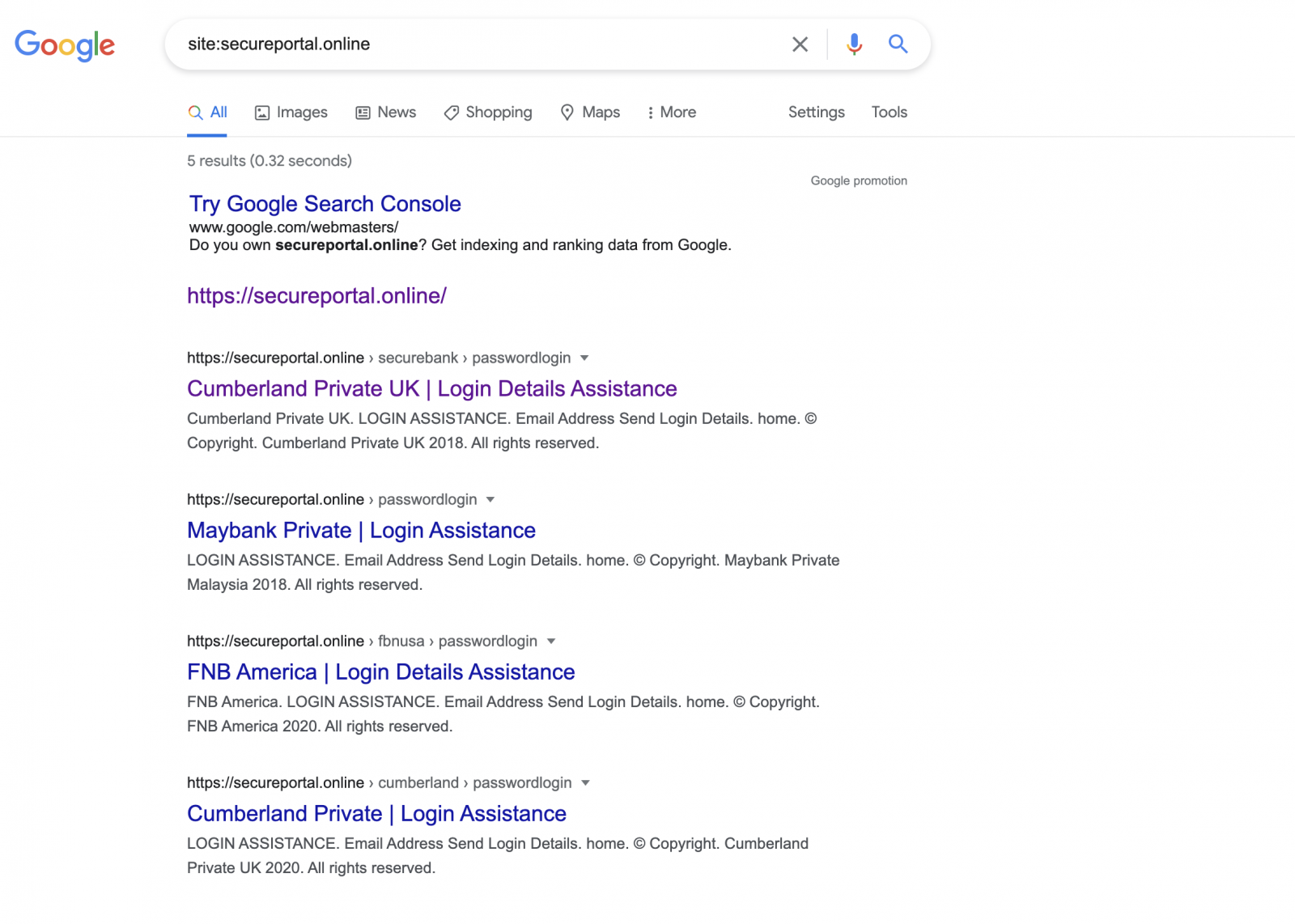
The threat actors hosted the fake Windows application on a fraudulent domain registered by the threat actors before the attack and impersonating Truist.
Other US and UK financial institutions (e.g., MayBank, FNB America, and Cumberland Private) seem to have also been impersonated in this spear-phishing campaign.
To increase their attacks’ success rate, the attackers used malware currently undetected by anti-malware engines on VirusTotal.
The malware deployed after recipients download and install the malicious executable in the spear-phishing emails connects to the secureportal(.)online domain.
As further detailed on the VirusTotal page for the malware sample shared by the FBI, the attackers can use the malware to log keystrokes and take screenshots of the victims’ screens.
According to VirusTotal, the malware’s list of capabilities includes:
Last month, world-leading employment agency Michael Page was impersonated in a similar phishing campaign attempting to infect recipients with Ursnif data-stealing malware capable of harvesting credentials and sensitive data from infected computers.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
Using info harvested from infected systems, the attackers can then steal their victims’ login credentials and various other sensitive data to further compromise their accounts or networks.
Fake applications used as decoys while performing malicious activity in the background is a known tactic employed in the past by cybercriminals and state-backed threat actors such as the Lazarus Group [1, 2].