KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







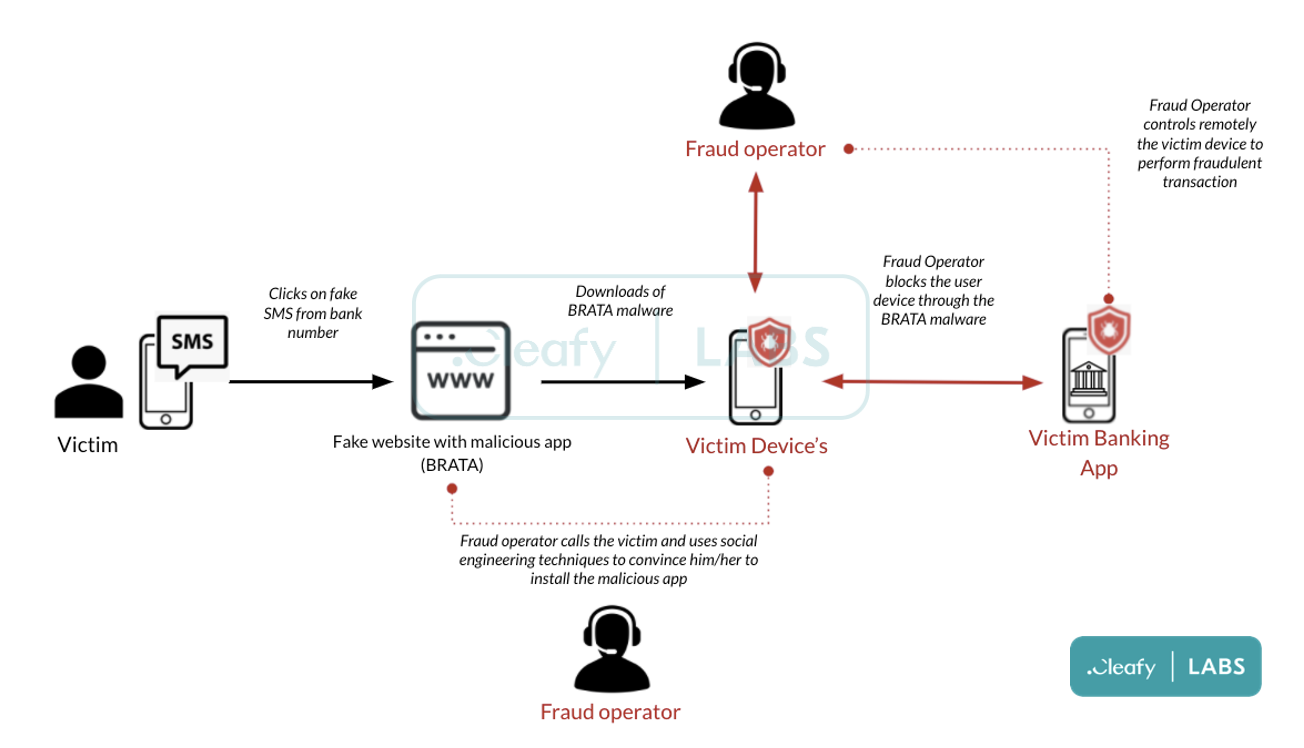
The BRATA Android remote access trojan (RAT) has been spotted in Italy, with threat actors calling victims of SMS attacks to steal their online banking credentials.
The variant currently in circulation is new, and according to a report by researchers at Cleafy, it can pass undetected by the vast majority of AV scanners.
BRATA was previously seen in Brazil, delivered via apps on the Google Play Store, but it appears that its authors are now selling it to foreign operators, which is not unusual in this field.
Also Read: 13 Special Skills To Become a Front End Developer Singapore
The Italian campaign was first spotted in June 2021, delivering multiple Android apps through SMS phishing, otherwise known as smishing.
Most of the malicious apps were called “Sicurezza Dispositivo” (Device Security) and were promoted as anti-spam tools.
That first wave failed in AV detection, having a 50% stealthiness rate in Virus Total. These high detection rates led to a second wave using a new variant with extremely low detection rates in mid-October.
In the second wave, the actors also expanded their targeting scope, raising the targeted financial institutes from one to three.
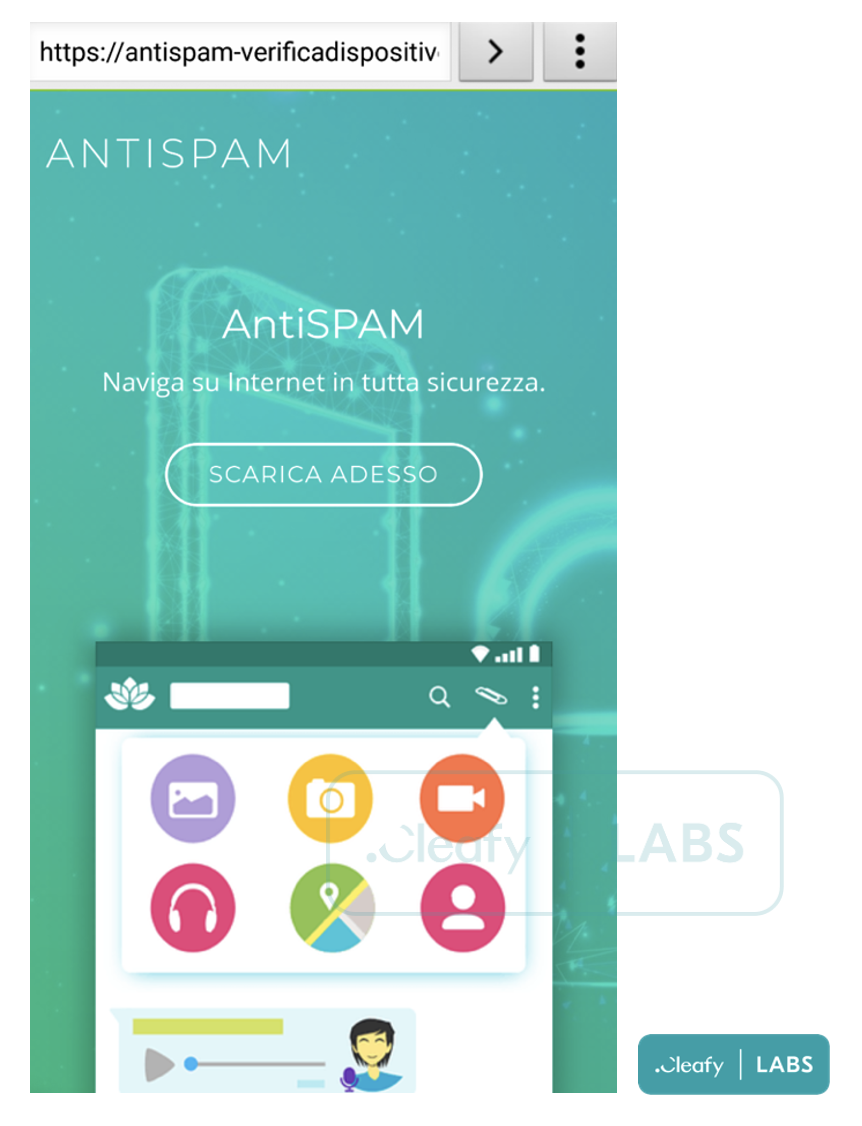
The attack begins with an unsolicited SMS text linking a malicious website. This text claims to be a message from the bank urging the recipient to download an anti-spam app.
The link leads to a page from where the victim downloads the BRATA malware themselves or takes them to a phishing page to enter their banking credentials.
During that step, the threat actors call the victim on the phone and pretend to be an employee of the bank, offering help with installing the app.
Also Read: Top 4 Advantages Of Opting For WordPress Developer Singapore
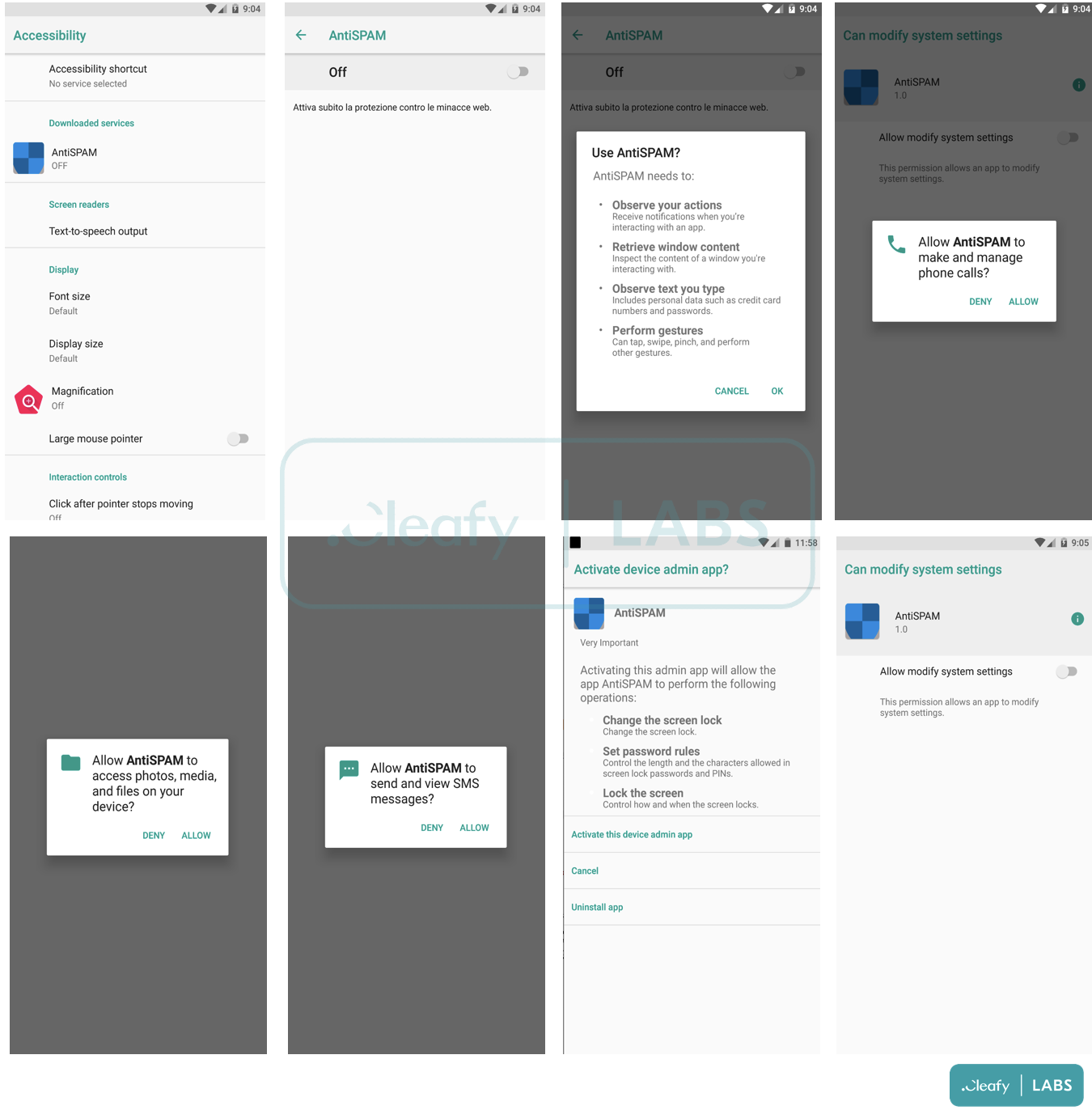
The app requires multiple permissions to enable the actor to take full control of the compromised device, including the Accessibility services, view and send SMS, make phone calls, and perform screen recording.
The full list of BRATA’s capabilities includes:
The actors abuse these permissions to access the victim’s bank account, retrieve the 2FA code, and eventually perform fraudulent transactions.
The mule accounts used as intermediary points in this campaign are based in Italy, Lithuania, and the Netherlands.
As this is a mobile campaign, desktop users are excluded from infections to narrow the targeting scope to prospective victims.
If you try to open the link contained in the SMS on a PC or laptop, the website won’t be viewable. That’s a simple checking method to confirm the validity of incoming messages.
Secondly, no bank ever suggests installing any app other than the official e-banking app, which is found on the Play Store/App Store and linked to from the bank’s official website.
Finally, whenever you install an app, pay attention to the type of permission requested and consider its relevance to the app’s functionality. Do not install the app if an app is requesting too many permissions unrelated to its functionality.