KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A high severity bug found in Facebook’s official chat plugin for WordPress websites with over 80,000 active installations could allow attackers to intercept messages sent by visitors to the vulnerable sites’ owner.
The Facebook Chat Plugin allows WordPress website owners to embed a chat pop-up to communicate with visitors in real-time through Facebook’s messaging platform for Facebook Pages.
The plugin also comes with support for chat transcripts and makes it easy to set up auto-replies and FAQs outside working hours to provide visitors with helpful information while the site owner can’t reply.
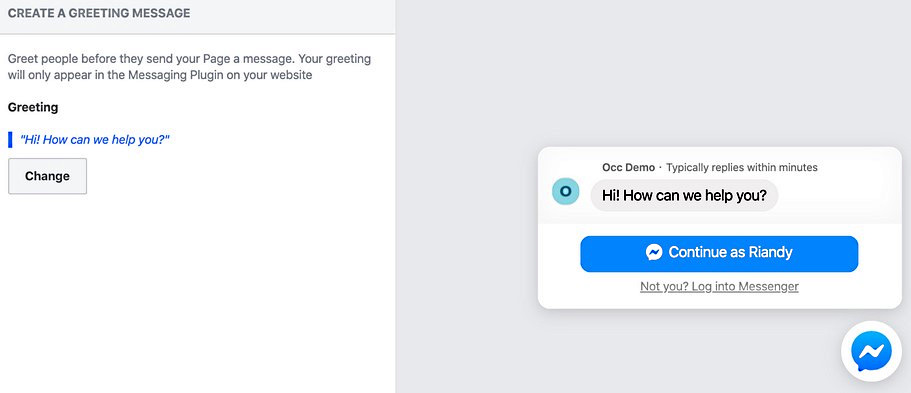
In a report published today by Wordfence’s Threat Intelligence team, threat analyst Chloe Chamberland says that the high severity authenticated options change vulnerability with a 7.4 CVSS base score rating was discovered on June 26, 2020.
Facebook’s security team addressed the flaw with the release of version 1.6 on July 28, roughly a month after they responded to Wordfence’s initial report.
On websites running a vulnerable version of the Official Facebook Chat Plugin, low-level authenticated attackers can “connect their own Facebook Messenger account [..] and engage in chats with site visitors[..].”
To connect the chat pop-up with the owner’s Facebook page, the plugin uses the wp_ajax_update_options AJAX action which, in unpatched versions, did not check if page connection requests came from authenticated website admins.
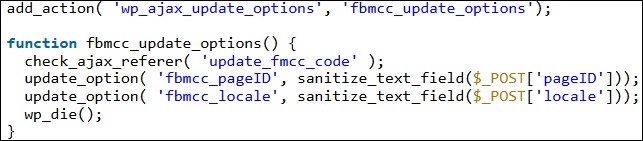
“This made it possible for any authenticated user, including subscriber level accounts, to send a request to update the options and hook-up their own Facebook Messenger account,” Chamberland explains.
“As a result, attackers could link their own Facebook Page Messenger account, by updating the page ID, to any given site running the plugin as long as they were able to register on the site and access the /wp-admin dashboard.”
After successfully linking their own Facebook page to the targeted site’s chat, attackers receive any messages sent through the site’s Messenger Chat, with the site owner no longer receiving any incoming messages.
“Exploit attempts targeting this vulnerability could easily be used as part of a social engineering attack by posing as a site owner requesting personally identifiable information, credentials, or other information,” Chamberland adds.
Attackers could also use their access to compromised sites’ chats to ruin the sites’ reputation through toxic interaction with their visitors or to cause loss of revenue by “driving traffic to the competitors business.”
Also read: Completed DPIA Example: 7 Simple Helpful Steps To Create
Even though Facebook Chat Plugin version 1.6, the release that addresses this vulnerability was published on July 28, the plugin was downloaded only 25,657 times since then based on historic download data provided by WordPress’ portal, this being the total number of both updates and new installs.
This means that at least 54,000 WordPress sites with active Messenger Chat pop-ups are still left exposed to attacks designed to exploit this flaw as part of future hacking campaigns.
Facebook Chat Plugin users are strongly recommended to update their plugin to version 1.6 as soon as possible to block attacks designed to hijack their sites’ chat as part of social engineering schemes.
Yesterday, Wordfence also reported reflected Cross-Site Scripting (XSS) and PHP Object Injection vulnerabilities found in the Newsletter WordPress plugin that can let hackers inject backdoors, create rogue admins, and potentially take over affected sites.
Wordfence also found a critical bug in Google’s official WordPress plugin with 300,000 installations that could allow attackers to gain owner access to targeted sites’ Google Search Console and facilitate black hat SEO campaigns.
Also read: Top 25 Data Protection Statistics That You Must Be Informed