KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Facebook has disrupted the operations of seven different spyware-making companies, blocking their Internet infrastructure, sending cease and desist letters, and banning them from its platform.
“As a result of our months-long investigation, we took action against seven different surveillance-for-hire entities to disrupt their ability to use their digital infrastructure to abuse social media platforms and enable surveillance of people across the internet,” said Director of Threat Disruption David Agranovich and Head of Cyber Espionage Investigations Mike Dvilyanski.
“These surveillance providers are based in China, Israel, India, and North Macedonia. They targeted people in over 100 countries around the world on behalf of their clients.”
Following this investigation, Facebook found that these seven companies’ services were used against and harmed vulnerable individuals such as activists, journalists, and minorities.
Also Read: PDPA For Companies: Compliance Guide For Singapore Business
However, the surveillance companies claimed their spyware and hacking tools were only used to target and help catch criminals and terrorists.
Facebook alerted people targeted with their surveillance tools (roughly 50,000 Facebook users) and shared its findings with other platforms, security researchers, and policymakers to take appropriate measures.
As Citizen Labs also revealed today, some of the people targeted with such surveillance tools had their devices infected with more than one spyware strain and, in some cases, by several attackers.
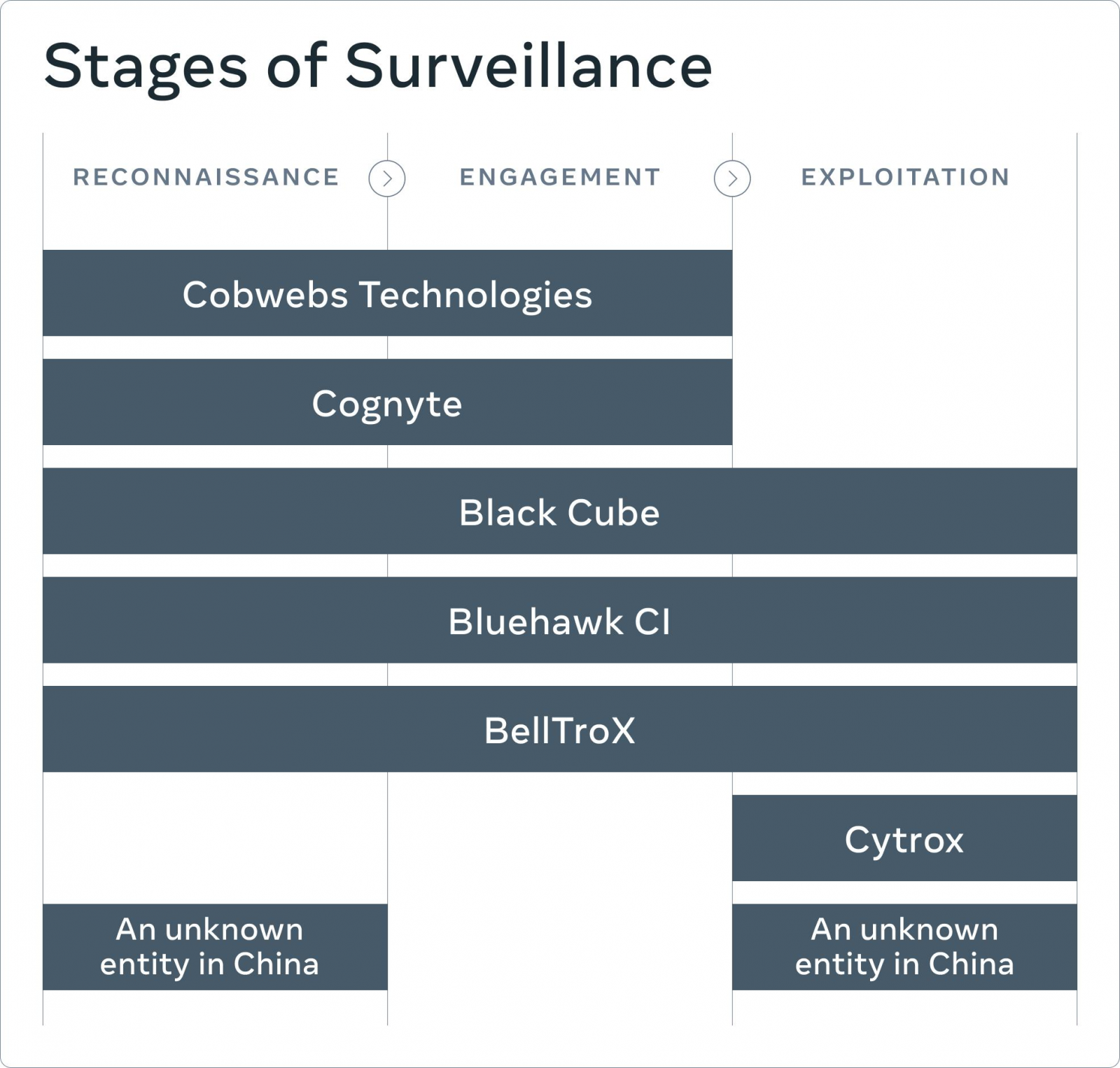
According to the full threat report also published today by Facebook, the seven surveillance-for-hire entities whose activity was disrupted as a result of Facebook’s investigation and the particular stages of surveillance they’re specialized in are:
“Although public debate has mainly focused on the exploitation phase, it’s critical to disrupt the entire lifecycle of the attack because the earlier stages enable the later ones,” they added.
“If we can collectively tackle this threat earlier in the surveillance chain, it would help stop the harm before it gets to its final, most serious stage of compromising people’s devices and accounts.”
Also Read: 10 Government Data Leaks In Singapore: Prevent Cybersecurity
Facebook’s investigation and disruptive actions against spyware-makers follow a string of recent reactions to the threat such entities represent to vulnerable groups.
For instance, similar action was taken by Apple last month when it filed a lawsuit against spyware-maker NSO Group for targeting and spying on Apple users with surveillance tech.
As later revealed, Apple warned US Department of State employees unknown attackers hacked their iPhones to deploy NSO-developed Pegasus spyware.
In July, Citizen Lab confirmed a report published by Amnesty International and Forbidden Stories which revealed that NSO spyware was found on iPhones hacked using zero-day zero-click iMessage exploits.
The same month, Microsoft and Citizen Lab linked spyware company Candiru to Windows spyware dubbed DevilsTongue and deployed on targets’ devices using Windows zero-day vulnerabilities.
Facebook also sued NSO Group two years ago for developing and selling a WhatsApp zero-day exploit that government-backed attackers used to compromise devices belonging to high-profile targets, including government officials, diplomats, and journalists.
The Commerce Department’s Bureau of Industry and Security (BIS) also sanctioned NSO Group and Candiru in last month for supplying software used to spy on government officials, journalists, and activists.