KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hades ransomware has been linked to the Evil Corp cybercrime gang who uses it to evade sanctions imposed by the Treasury Department’s Office of Foreign Assets Control (OFAC).
Evil Corp (aka the Dridex gang or INDRIK SPIDER) has been active since at least 2007 and it is known for distributing the Dridex malware.
They later shifted to the ransomware “business,” first using Locky ransomware and then their own ransomware strain known as BitPaymer, deployed in attacks until 2019.
The U.S. Treasury Department sanctioned Evil Corp gang members in December 2019 after being charged for using Dridex to cause over $100 million in financial damages.
Because of this, their victims face a tricky situation if they want to pay Evil Corp’s ransom as they would also violate the sanctions.
OFAC also warned in October 2020 that orgs assisting ransomware victims in making ransom payments to sanctioned threat actors also face risks as their actions could violate regulations.
Starting with June 2020, Evil Corp refreshed its tactics to circumvent the sanctions, deploying its new WastedLocker ransomware in attacks targeting enterprise orgs.
Wearable device maker Garmin is one of the high-profile targets Evil Corp hit with its WastedLocker ransomware. The company had to shut down some of its connected services and call centers following the attack.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
CrowdStrike now linked the cybercrime gang to Hades ransomware based on “significant code overlap.” This new, previously unattributed malware tooling is helping Evil Corp bypass sanctions to monetize their attacks.
Hades ransomware is a 64-bit compiled variant of WastedLocker upgraded with supplementary code obfuscation and a few minor feature changes.
“Hades ransomware shares the majority of its functionality with WastedLocker; the ISFB-inspired static configuration, multi-staged persistence/installation process, file/directory enumeration, and encryption functionality are largely unchanged,” CrowdStrike said.
“Hades did receive minor modifications, and the removed features included those that were uniquely characteristic of INDRIK SPIDER’s previous ransomware families — WastedLocker and BitPaymer.”
When encrypting a victim’s systems, Hades creates a ransom note named ‘HOW-TO-DECRYPT-[extension].txt’ resembling ransom notes dropped by REvil ransomware.
The ransom notes contain a URL that directs the victims to a Tor site with info about the attack and a Tox messenger address they can use to contact Evil Corp’s operators.
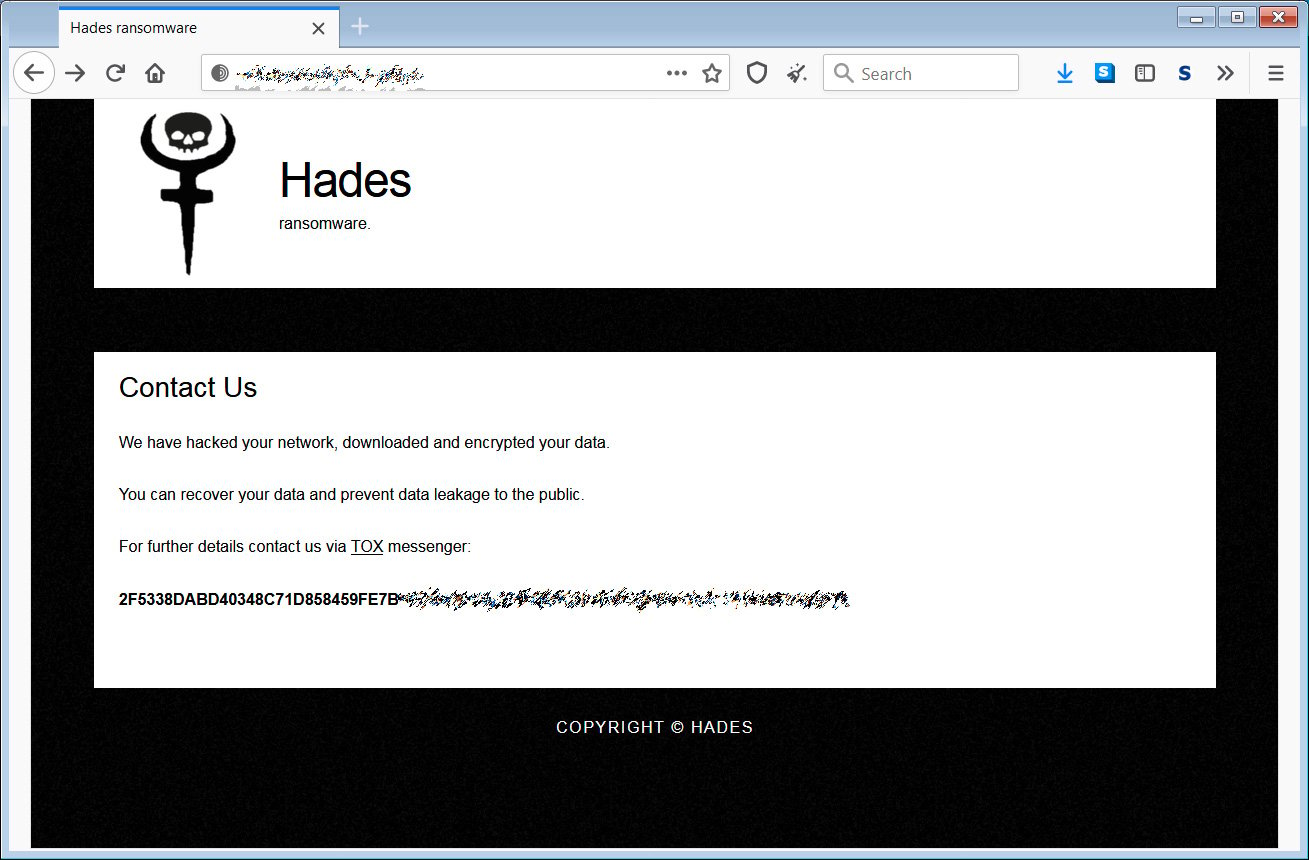
“INDRIK SPIDER’s move to this ransomware variant also came with another shift in tactics: the departure from using email communication and the possibility of exfiltrating data from victims to elicit payments,” CrowdStrike added.
BleepingComputer reported that Hades ransomware was used to encrypt trucking giant Forward Air’s systems in December 2020.
While there aren’t many Hades ransomware attacks being reported by affected organizations, Evil Corp victims have been using the ID-Ransomware service to check if their systems were hit by Hades ransomware since the group started using the new strain.
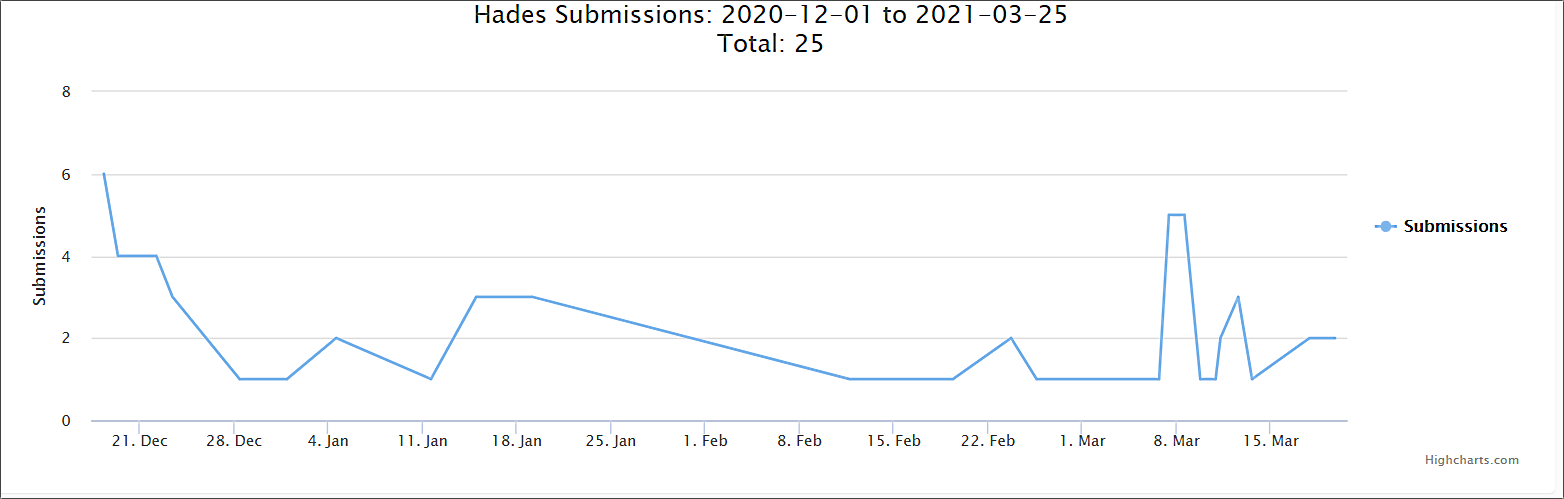
“The continued development of WastedLocker ransomware is the latest attempt by the notorious adversary to distance themselves from known tooling to aid them in bypassing the sanctions imposed upon them,” CrowsStrike concluded.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
“The sanctions and indictments have undoubtedly significantly impacted the group and have made it difficult for INDRIK SPIDER to successfully monetize their criminal endeavors.”