KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Analysis of the recently-emerged Entropy ransomware reveals code-level similarities with the general purpose Dridex malware that started as a banking trojan.
Two Entropy ransomware attacks against different organizations allowed researchers to connect the dots and establish a connection between the two pieces of malware.
In a report today, Sophos principal researcher Andrew Brandt says that deeper inspection of the Entropy malware was prompted by a detection signature that had been created for catching Dridex.
Also Read: AI Auditing Framework: Draft Guidance for Organizations
Both victim organizations had unprotected machines, but the systems running endpoint protection stopped the attack, triggered by detecting the packer code for protecting Entropy, although the signature was for identifying the packer code for Dridex.
SophosLabs analysts found that some of the other subroutines that Entropy relies on to hide its behavior were similar to those for the same functionality in Dridex.
“The instructions that dictate how Entropy performs the first ”layer“ of unpacking are similar enough to Dridex that the analyst who looked at the packer code, and in particular the portion that refers to an API called LdrLoadDLL – and that subroutine’s behavior, described it as ”very much like a Dridex v4loader,“ and compared it to a similar loader used by a Dridex sample from 2018”
There’s suspicion in the infosec community that Entropy ransomware is a rebrand of Grief (a.k.a. Pay or Grief) ransomware, which is a continuation of the DoppelPaymer operation.
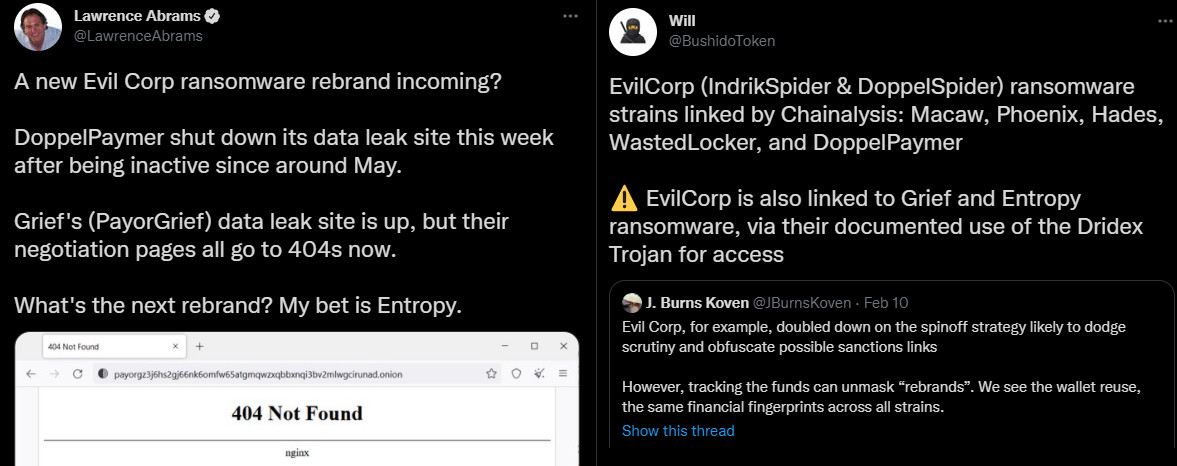
These suspicions grow stronger with today’s report from Sophos, which notes that the same packer code was detected on Sophos-protected systems targeted with DoppelPaymer ransomware.
DoppelPaymer is attributed to the EvilCorp gang (a.k.a. Indrik Spider), which is behind the distribution of the Dridex banking trojan turned malware downloader via phishing emails.
Members of EvilCorp and companies associated with the group have been sanctioned in 2019 by the U.S. Treasury Department, causing ransomware negotiation firms to stop mediating ransom payments to avoid fines and legal actions.
EvilCorp decided to rename their ransomware operations, so sanctions could no longer be applied. Some of the ransomware names used are WastedLocker, Hades, and Phoenix.
The Entropy ransomware operation started since at least November 2021, stealing data from breached networks. In the style of other ransomware operations, the Entropy group set up a leak site to publish the names of non-paying victims. As of this writing, the site lists nine organizations in the public and private sector.
Also Read: How to Make Data Protection Addendum Template in Simple Way
In the first attack that Sophos analyzed, the threat actor exploited ProxyShell vulnerabilities in Exchange Server for remote access into a media organization in North America and deployed Cobalt Strike beacons.
The attackers spent four months moving laterally and stealing data before encrypting computers using Entropy ransomware.
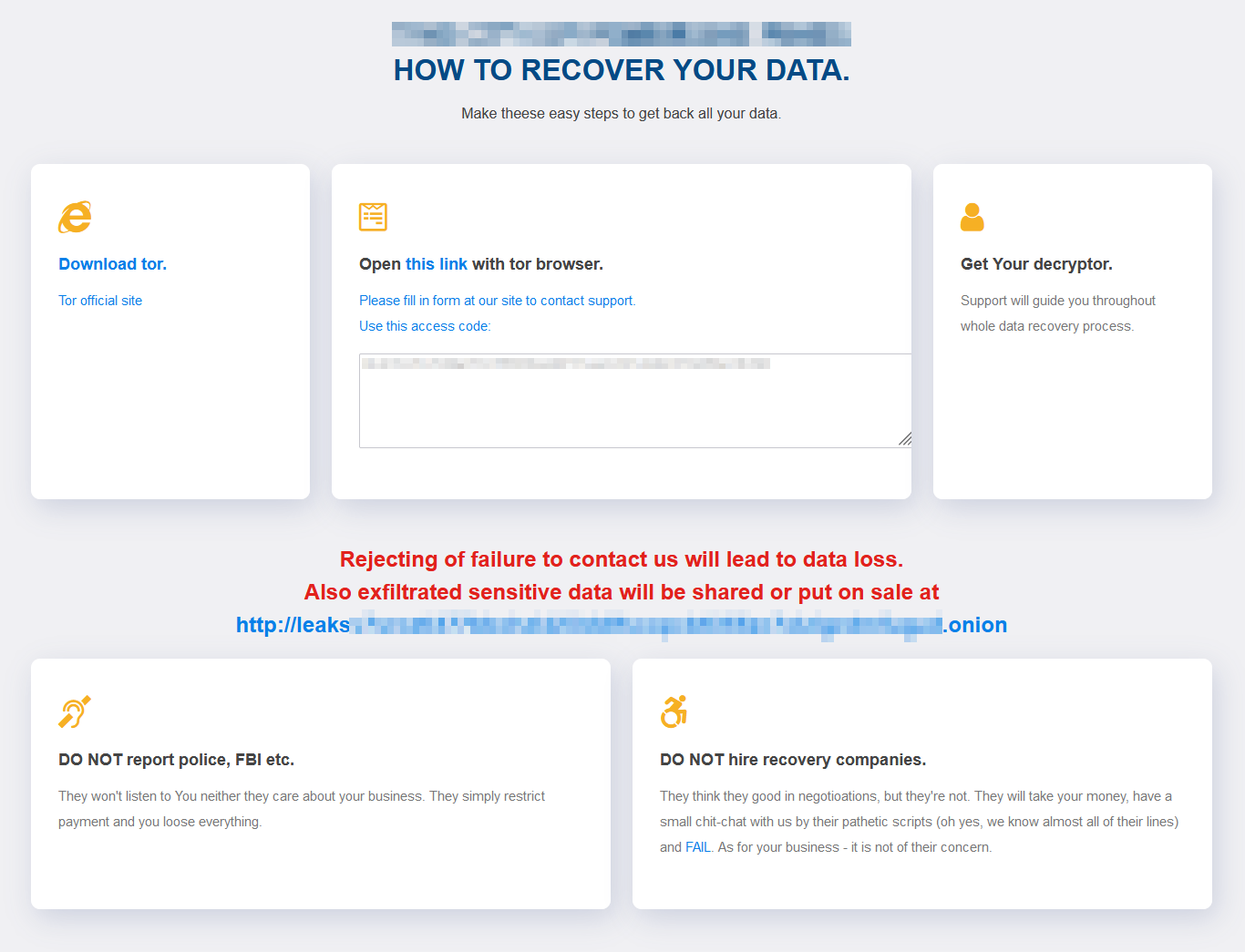
The second attack deployed the Dridex malware on a computer belonging to a regional government organization. Dridex was then used to funnel in other malware that allows pivoting to other systems.
“Significantly, in this second attack, only 75 hours passed between the initial detection of a suspicious login attempt on a single machine and the attackers commencing data exfiltration” – Sophos
Sophos notes that both attacks were possible because the targets had vulnerable Windows machines “that lacked current patches and updates.”
Keeping machines up-to-date and implementing multi-factor authentication (MFA) makes initial access a more difficult task for attackers, the researcher note.