KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Emotet is now taking part in the United States 2020 Presidential election with a new spam campaign pretending to be from the Democratic National Convention’s Team Blue initiative.
When the Emotet gang sends out spam, their main goal is to convince recipients to open the attached malicious document. This is usually done through email themes that pretend to be shipping documents, invoices, payment receipts, and voicemails.
During the holidays or major political events, Emotet is known to send more intricately-themed emails to convince users to open attachments. These emails include invites to holiday parties or even a Greta Thunberg demonstration.
Once the attachments are opened, and macros enabled, the Emotet malware will be installed on a computer. It will then steals your emails and use your computer to send out further spam.
Ultimately, Emotet will install other malware such as TrickBot or QakBot that may lead to a ransomware attack on your network.
Just days after the first Presidential debate, the threat actors behind Emotet are spewing out a new spam campaign that pretends to be from the DNC.
This new campaign pretends to be from the Democratic Party’s ‘Team Blue Take Action’ initiative asking for volunteers to help Democrats get elected in the 2020 elections.
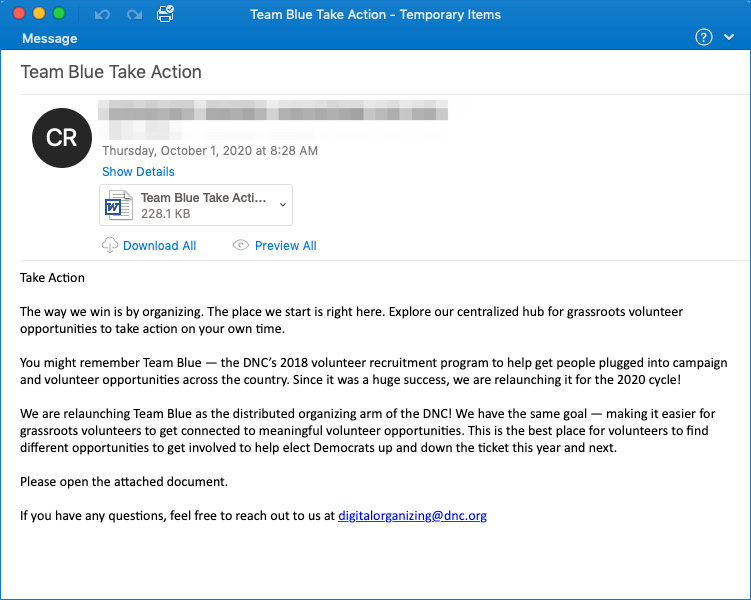
The full text of the ‘Take Blue Take Action’ spam email is:
Take Action
The way we win is by organizing. The place we start is right here. Explore our centralized hub for grassroots volunteer opportunities to take action on your own time.
You might remember Team Blue - the DNC's 2018 volunteer recruitment program to help get people plugged into campaign and volunteer opportunities across the country. Since it was a huge success, we are relaunching it for the 2020 cycle!
We are relaunching Team Blue as the distributed organizing arm of the DNC! We have the same goal - making it easier for grassroots volunteers to get connected to meaningful volunteer opportunities. This is the best place for volunteers to find different opportunties to get involved to help elect Democrats up and down the ticket this year and next.
Please open the attached document.According to ProofPoint, who found this new Emotet campaign, the spam emails are using the email subjects such as ‘Team Blue Take Action’, ‘Valanters 2020’, ‘List of works’, and ‘Volunteer.’
The malicious documents are also named to coincide with the volunteer theme and include filenames such as ‘Team Blue Take Action.doc’, ‘List of works.doc’, ‘Valanters 2020.doc’, and ‘Volunteer.doc.’
When opened, the attached documents will pretend to be created from an iOS device and prompt you to ‘Enable Content’ to view it properly.
Also Read: Intrusion Into Privacy All About Law And Legal Definition
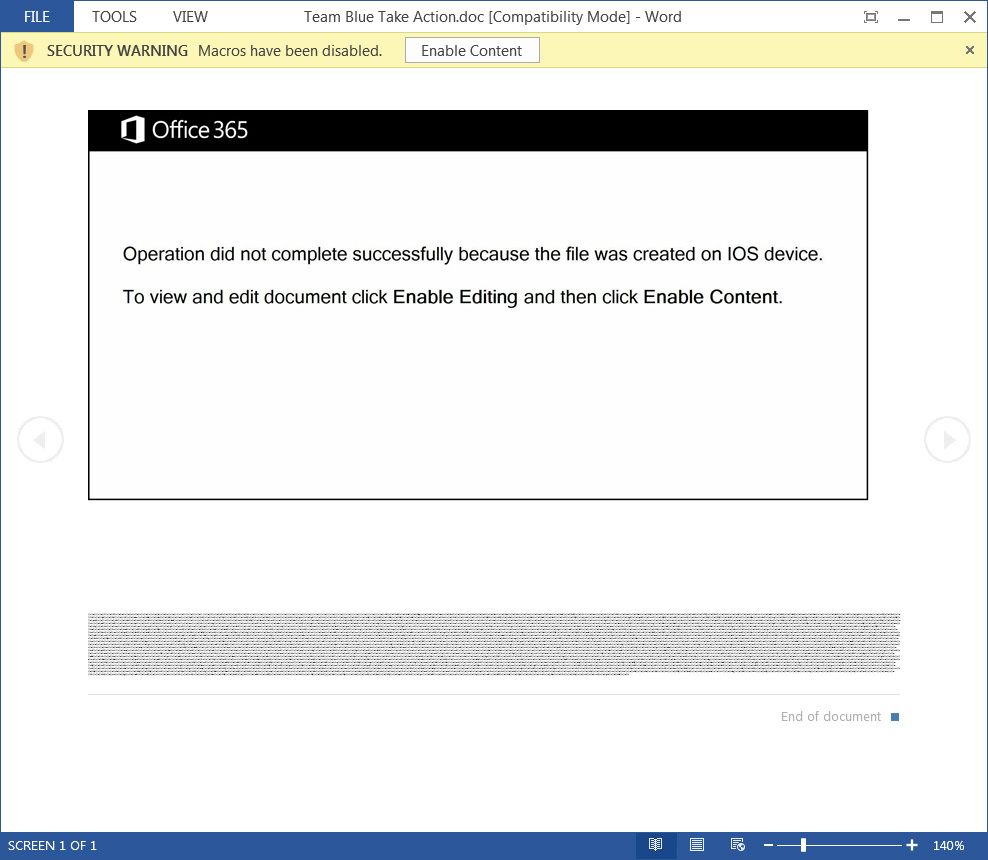
Once you enable content, though, malicious macros will be launched that download and install the Emotet trojan onto your computer.
When successful, the Trojan will quietly run in the background while using your computer to send out further spam and downloading other malware onto your computer.
As a general rule, never open attachments from anyone without confirming over the phone that they did indeed send you the file. You should also always be cautious of enabling content or macros on any attachment you receive.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business