KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The infrastructure of today’s most dangerous botnet built by cybercriminals using the Emotet malware was taken down following an international coordinated action coordinated by Europol and Eurojust.
The joint effort between law enforcement agencies and authorities from Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine allowed investigators to take control of the botnet’s servers and disrupt the malware’s operation.
Following a global investigative effort, judicial authorities and law enforcement took down the botnet’s whole infrastructure from the inside after gaining control of its servers earlier this week.
“The infrastructure that was used by EMOTET involved several hundreds of servers located across the world, all of these having different functionalities in order to manage the computers of the infected victims, to spread to new ones, to serve other criminal groups, and to ultimately make the network more resilient against takedown attempts,” Europol explained.
“The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure. This is a unique and new approach to effectively disrupt the activities of the facilitators of cybercrime.”
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
You can check if your e-mail address has been compromised by Emotet and used to deliver malicious emails using this Dutch National Police portal.
This portal will help you search through a database of e-mail addresses, usernames, and passwords stolen by Emotet and found earlier this week by the Dutch National Police during the criminal investigation that led to the botnet’s disruption.
The Ukrainian police’s Cyberpolice Department also arrested two individuals suspected to have been involved in the botnet’s infrastructure maintenance and are facing 12 years in prison if found guilty.
Other members of a cybercrime group that used the infrastructure of the Emotet botnet were also identified during the investigation with measures being taken to detain them.
A video of the arrests made by the Ukrainian police is embedded below.
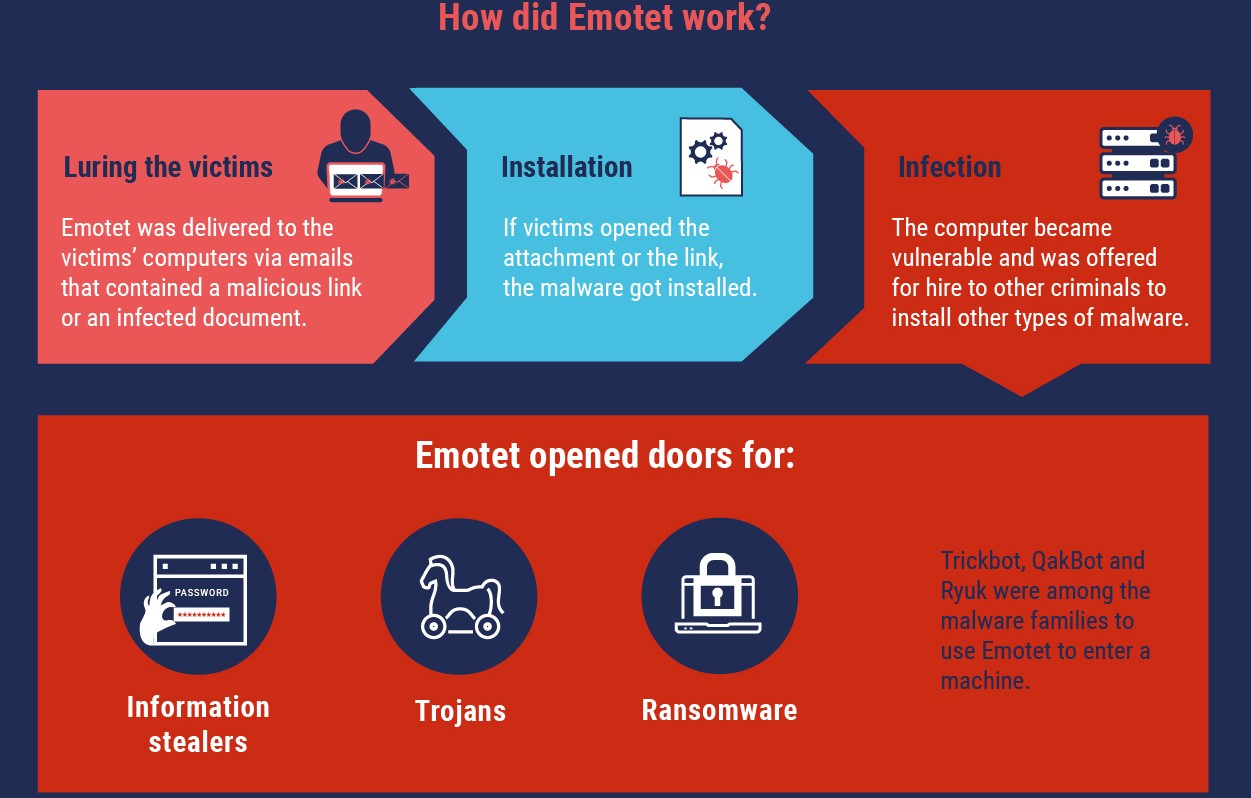
The Emotet malware was first spotted as a banking Trojan in 2014 and it has evolved into a botnet used by the TA542 threat group (aka Mummy Spider) to deploy second-stage malware payloads.
Emotet drops QakBot and Trickbot (which in turn deploy both Ryuk and Conti ransomware) trojan payloads on victims’ compromised computers.
“The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale,” Europol added.
“Once this unauthorised access was established, these were sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware.”
Following a break of more than a month, the Emotet botnet was revived on December 21sts [1, 2], with Microsoft spotting a campaign delivering “a wide range of lures in massive volumes of emails, the use of fake replies or forwarded emails, password-protected archive attachments.”
Before this short break, Emotet has targeted US state and local governments in potentially targeted campaigns according to an October DHS-CISA advisory.
The highly active Trickbot botnet was also partially and temporarily disrupted following a joint operation in October 2020.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
Update: Added info on arrests made by the Ukrainian police.