KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A joint operation between French and Ukrainian law enforcement has reportedly led to the arrests of several members of the Egregor ransomware operation in Ukraine.
As reported first by France Inter, on Tuesday, law enforcement made the arrests after French authorities could trace ransom payments to individuals located in Ukraine.
The arrested individuals are thought to be Egregor affiliates whose job was to hack into corporate networks and deploy the ransomware. France Inter also reports some individuals provided logistical and financial support.
Over this past year, Egregor has attacked numerous French organizations, including Ubisoft, Ouest France, and, more recently Gefko.
The operation was reported launched through an investigation opened last fall by the Tribunal de grande instance de Paris after receiving complaints about the ransomware gang.
It is not known at this time how many people were arrested.
BleepingComputer.com has contacted French law enforcement but has not heard back at this time.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
Egregor operates as a ransomware-as-a-service (RaaS) where affiliates partner with the ransomware developers to conduct attacks and split the ransom payments.
In partnerships like this, the ransomware developers are responsible for developing the malware and running the payment site. At the same time, the affiliates are responsible for hacking into victims’ networks and deploying the ransomware.
As part of this arrangement, developers earn between 20-30% of a ransom payment, while affiliates make the other 70-80%.
Egregor launched in the middle of September, just as one of the largest groups known as Maze began shutting down its operation.
At the time, threat actors told BleepingComputer that Maze affiliates moved to the Egregor RaaS, allowing the new ransomware operation to launch with experienced and skilled hackers.
In November, the ransomware gang partnered with the Qbot malware to gain access to victims’ networks, increasing the volume of attacks even further.
Due to Egregor growing so quickly in a relatively short period, victims had to wait in a queue to negotiate a ransomware payment.
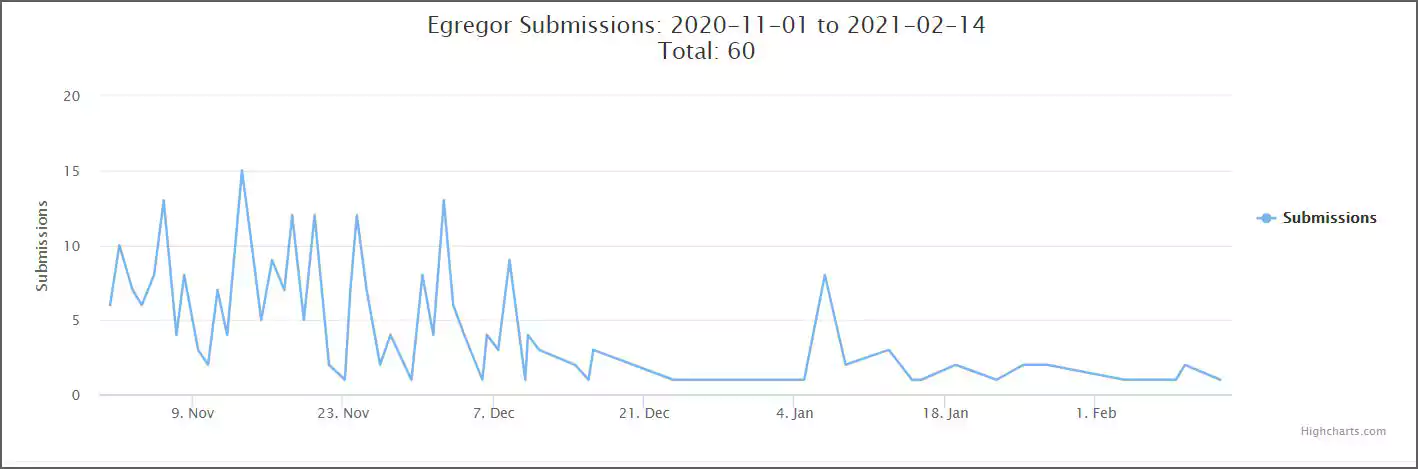
In early December, Egregor suddenly started slowing down with far fewer attacks conducted by the operation. You can see this dramatic decrease beginning on December 9th, 2020, in the graph below of Egregor submissions to ID Ransomware.
Last month, Bill Siegel, CEO of ransom negotiation firm Coveware, told BleepingComputer that they too had seen a decline in Egregor attacks and told us affiliates might have moved to another RaaS.
In January, Egregor’s data leak site went offline for approximately two weeks, and when it came online again, there were issues with the site. This unusual activity led other threat actors to become suspicious that Egregor was hacked or breached by aw enforcement.
Whether the decline of Egregor activity is law enforcement related or simply the ebbs and flows of ransomware operations is not currently known.
In a new report released last week by cybersecurity firm Kivu, researchers state that Egregor has amassed over 200 victims since it launched, and is comprised of 10-12 core members and 20-25 semi-exclusively vetted members.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
Some of the well-known companies that have been attacked by Egregor include Barnes and Noble, Kmart, Cencosud, Randstad, Vancouver’s TransLink metro system, and Crytek.
Thx to pancak3 for the tip!