KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The DeadBolt ransomware is now targeting ASUSTOR NAS devices by encrypting files and demanding a $1,150 ransom in bitcoins.
This wave of attacks was first reported on Reddit and the BleepingComputer forums, and soon after, on the ASUSTOR forums.
Similar to the DeadBolt ransomware attacks that targeted QNAP NAS devices last month, the threat actors claim to be using a zero-day vulnerability to encrypt ASUSTOR NAS devices.
When encrypting files on an ASUSTOR device, the ransomware will rename the files to include the .deadbolt file extension. The ASUSTOR login screen will also be replaced with a ransom note demanding 0.03 bitcoins, worth approximately $1,150, as shown below.
Also Read: 10 Simple and Useful Tips On Agreement Drafting Services
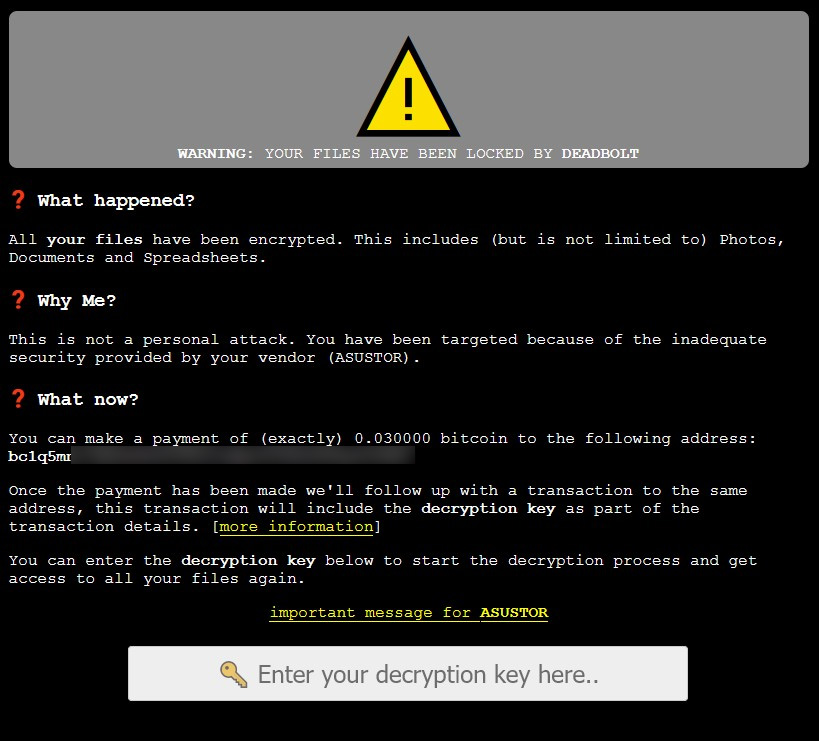
While ASUSTOR has not explained how the NAS devices are being encrypted, some ASUSTOR owners believe that it is a vulnerability in the PLEX media server or EZ Connect that allows access to their devices.
ASUSTOR states that they are investigating the attacks and have provided the following statement:
In response to Deadbolt ransomware attacks affecting ASUSTOR devices, the myasustor.com DDNS service will be disabled as the issue is investigated. ASUSTOR will release more information with new developments as we investigate and review the causes to ensure this does not happen again. We remain committed to helping affected customers in every way possible. For your protection, we recommend the following measures:
Change default ports, including the default NAS web access ports of 8000 and 8001, as well as remote web access ports of 80 and 443.
Most importantly, do not expose your ASUSTOR device to the Internet to avoid being encrypted by DeadBolt.
If DeadBolt has already infected your device, unplug the Ethernet cable and force-shut down your NAS device by holding the power button for three seconds.
Also Read: Top 5 Impact of Data Loss on Business
Do not attempt to reboot the NAS, as this will erase all files. Instead, use this contact form to request instructions from ASUSTOR technicians on how to recover your files.
It is unclear if all ASUSTOR devices are vulnerable to DeadBolt attacks, but reports indicate that the AS6602T, AS-6210T-4K, AS5304T, AS6102T, and AS5304T models are unaffected.
Unfortunately, there is no way to recover files encrypted by the DeadBolt ransomware for free, and many affected QNAP users were forced to pay the ransom to recover files.
ASUSTOR is planning to release a recovery firmware today so that users can once again use their NAS devices. However, this firmware update will not help recover any encrypted files.
“We estimate to release a recovery firmware from our support engineers today for users whose NAS is hacked so they can use their NAS again. However, encrypted files can not be recovered unless users have backups,” ASUSTOR wrote to their Facebook page.
Unfortunately, this recovery process will likely remove the ransom note pages and malware executable required to decrypt files if a ransom is paid, which historically caused a lot of issues for QNAP owners.
It is strongly suggested that users backup the index.cgi and ALL YOUR FILES HAVE BEEN LOCKED BY DEADBOLT.html files before running the recovery software.
These files contain the information necessary to pay the ransom and receive a decryption key, which owners can then use with Emsisoft’s decryptor for DeadBolt.
If a ransom is paid, the threat actors will create a bitcoin transaction to the same bitcoin address a ransom was paid that contains the decryption key for the victim. The decryption key is located under the OP_RETURN output, as shown below.
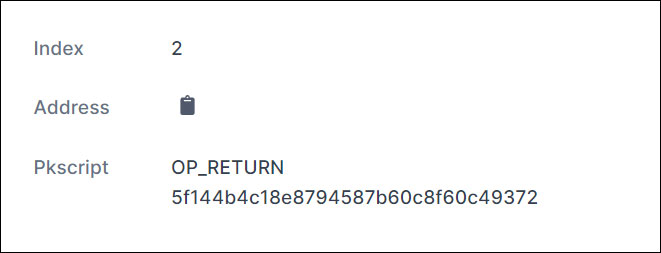
For those who need help with the decryption process or want to see common issues that affected QNAP devices last month, you can review our DeadBolt ransomware support topic.
Similar to the attacks on QNAP devices, DeadBolt is attempting to sell information to ASUSTOR about the alleged zero-day vulnerability used to breach NAS devices and the master decryption for all victims.
The DeadBolt ransom note includes a link titled “important message for ASUSTOR,” that when clicked, will display a message from the DeadBolt gang specifically for ASUSTOR.
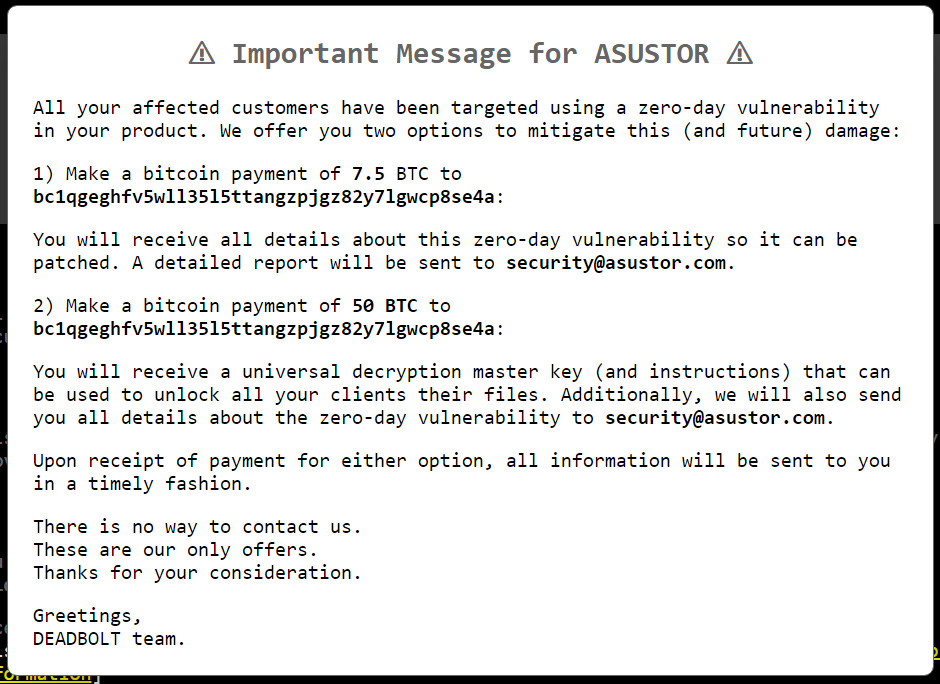
On this screen, the DeadBolt threat actors are selling the details of the alleged zero-day vulnerability if ASUSTOR pays them 7.5 Bitcoins, worth $290,000.
The DeadBolt gang is also trying to sell ASUSTOR the master decryption key for all victims and the zero-day details for 50 bitcoins, worth $1.9 million.
“Make a bitcoin payment of 50 BTC to bc1qgeghfv5wll35l5ttangzpjgz82y7lgwcp8se4a,” the threat actors wrote in a message to QNAP.
“You will receive a universal decryption master key (and instructions) that can be used to unlock all your clients their files. Additionally, we will also send you all details about the zero-day vulnerability to [email protected].”
The ransomware operation states that there is no way to contact them other than making the bitcoin payment. However, once payment is made, they say they will send the information to the [email protected] email address.
It is doubtful that ASUSTOR will pay the extortion demand, so if the DeadBolt Ransomware encrypted your NAS device, the only way to recover files is to restore from backups or pay the ransom.
Based on last month’s analysis of the ransomware by BleepingComputer, DeadBolt is a Linux malware that uses a template for the ransom note that can be substituted for any vendor, as shown below:
This is not a personal attack. You have been targeted because of the inadequate security provided by your vendor ({VENDOR_NAME}).
Therefore, we will likely see attacks against other NAS manufacturers in the future.