KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







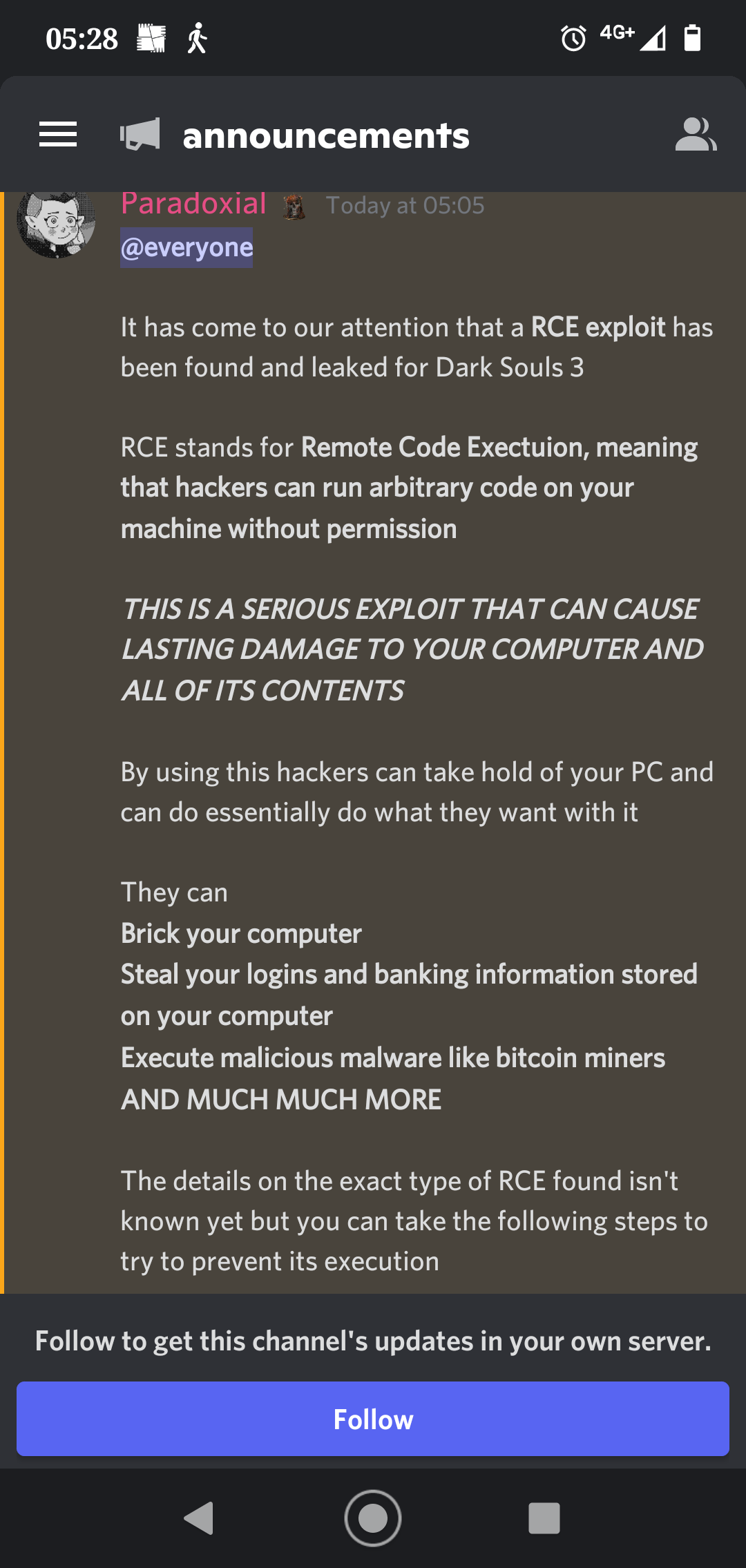
Bandai Namco has deactivated the online PvP mode for the Dark Souls role-playing game, taking its servers offline to investigate reports about a severe security issue that may pose a risk to players.
According to community reports on Reddit, the vulnerability is a remote code execution (RCE) that could allow attackers to take control of the system, giving them access to sensitive information, letting them plant malware, or use resources for cryptocurrency mining.
The same reports claim that the exploit is actively circulated and it may also work against Elden Ring, an upcoming title of Bandai Namco.
Also Read: The 5 Phases of Penetration Testing You Should Know
The issue became widely known on Saturday in a post on Discord clarifying that the game developer received details about the RCE vulnerability in a responsible disclosure report straight from the person who discovered it.
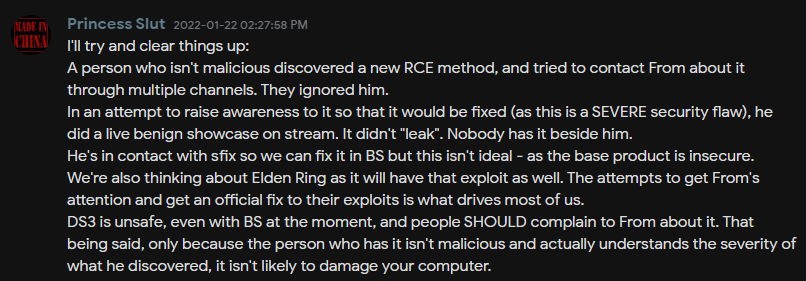
Bandai Namco allegedly ignored the report but given the severity of the flaw, the reporter decided to demonstrate it on popular streamers to raise awareness and show how critical it is.
Indeed, there has been at least one stream on Twitch showcasing the exploit, even if involuntarily, ending with a crash following the execution of Microsoft PowerShell and a text-to-speech script.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
After the reports of active exploitation spread, Dark Souls announced on Twitter that the PvP servers for all titles of the series would be taken offline to allow the team to investigate the allegations.
This only affects the PC platform, and the PvP experience on Xbox and PS consoles remains unaffected.
Blue Sentinel, a widely used anti-cheat tool for the Dark Souls game, is reportedly working on a patch to prevent exploiting the flaw. However, the possibility of mitigation through this tool isn’t guaranteed.
Bleeping Computer has reached out to Bandai Namco asking for more details on the RCE exploit and the time estimates for remediation, but we haven’t received a response yet.