KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Cybersecurity firm Qualys is likely the latest victim to have suffered a data breach after a zero-day vulnerability in their Accellion FTA server was exploited to steal hosted files.
In December, a wave of attacks targeted the Accellion FTA file-sharing application using a zero-day vulnerability that allowed attackers to steal files stored on the server.
Since then, the Clop ransomware has been extorting these victims by posting the stolen data on their ransomware data leak site.
As Accellion FTA devices are standalone servers designed to be outside the security perimeter of a network and accessible to the public, there have been no reported attacks on these devices leading to internal systems compromise.
Before today, the known victims extorted by Clop include Transport for NSW, Singtel, Bombadier, geo-data specialist Fugro, law firm Jones Day, science and technology company Danaher, and technical services company ABS Group.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
Yesterday, the Clop ransomware gang posted screenshots of files allegedly belonging to the cybersecurity firm Qualys. The leaked data includes purchase orders, invoices, tax documents, and scan reports.
As reported by Valery Marchive of LegMagIT and confirmed by BleepingComputer, Qualys had an Accellion FTA device located on their network.
The Accellion FTA device was located at fts-na.qualys.com, and the IP address used by the server is assigned to Qualys. Qualys has since decommissioned the FTA device, with Shodan showing it was last active on February 18th, 2021.
It is unknown if Clop sent ransom notes to Qualys regarding the attack, but other victims have received them in the past, according to a report by Mandiant.
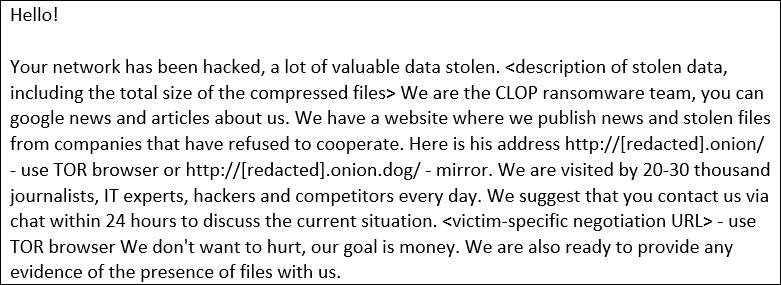
It is still unclear if the Clop ransomware gang performed the attacks on Accellion FTA devices or is partnering with another group to share the files and extort victims publicly.
Clop has in the past sent emails to journalists, including BleepingComputer, about new Accellion FTA victims posted to their site.
BleepingComputer has contacted Qualys before publication and are awaiting an official statement.
In a statement issued tonight, Qualys has confirmed that their Accellion FTA server was breached in December 2020 and affected a limited amount of customers.
As the server was deployed in their DMZ, which is segregated from their internal network, Qualys’ product environment was not compromised.
“New information has come out today related to a previously identified zero-day exploit in a third-party solution, Accellion FTA, that Qualys deployed to transfer information as part of our customer support system.”
“Qualys has confirmed that there is no impact on the Qualys production environments, codebase or customer data hosted on the Qualys Cloud Platform. All Qualys platforms continue to be fully functional and at no time was there any operational impact.”
“Qualys had deployed the Accellion FTA server in a segregated DMZ environment, completely separate from systems that host and support Qualys products to transfer information as part of our customer support system,” Qualys disclosed in a security incident notice today.
Also Read: The 3 Main Benefits Of PDPA For Your Business
Qualys states that they have shut down the affected Accellion FTA servers and switched to alternative applications for support-related file transfers.
At this time, Qualys is still investigating the breach and has hired Mandiant to assist them.