KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







CD Projekt Red has released a hotfix for Cyberpunk 2077 to fix a remote code execution vulnerability that could be exploited by third-party data file modifications and save games files.
On February 2nd, 20201, CD Projekt warned that Cyberpunk 2077 users should avoid using files, such as mods that modify data files or custom save game files, due to a vulnerability in how the game uses DLL files.
Last week, CyberpunkSaveEditor creator PixelRick disclosed that a buffer overflow vulnerability chained with a non-ASLR DLL (xinput1_3.dll) allows specially crafted save games or modifications to perform code execution on a PC.
ASLR, or address space layout randomization, is a security feature that randomizes the memory regions (address space) utilized by a process. By doing this, vulnerability exploits must be tailor-made for a particular process as it is currently loaded into memory.
Also Read: Website Ownership Laws: Your Rights And What These Protect
If exploited, this vulnerability could have allowed attackers to execute commands on the computer, including download and installing malware.
To resolve the vulnerabilities, CD Projekt has released Cyberpunk 2077 Hotfix 1.12, which states it “Fixed a buffer overrun issue” and “Removed/replaced non-ASLR DLLs.”
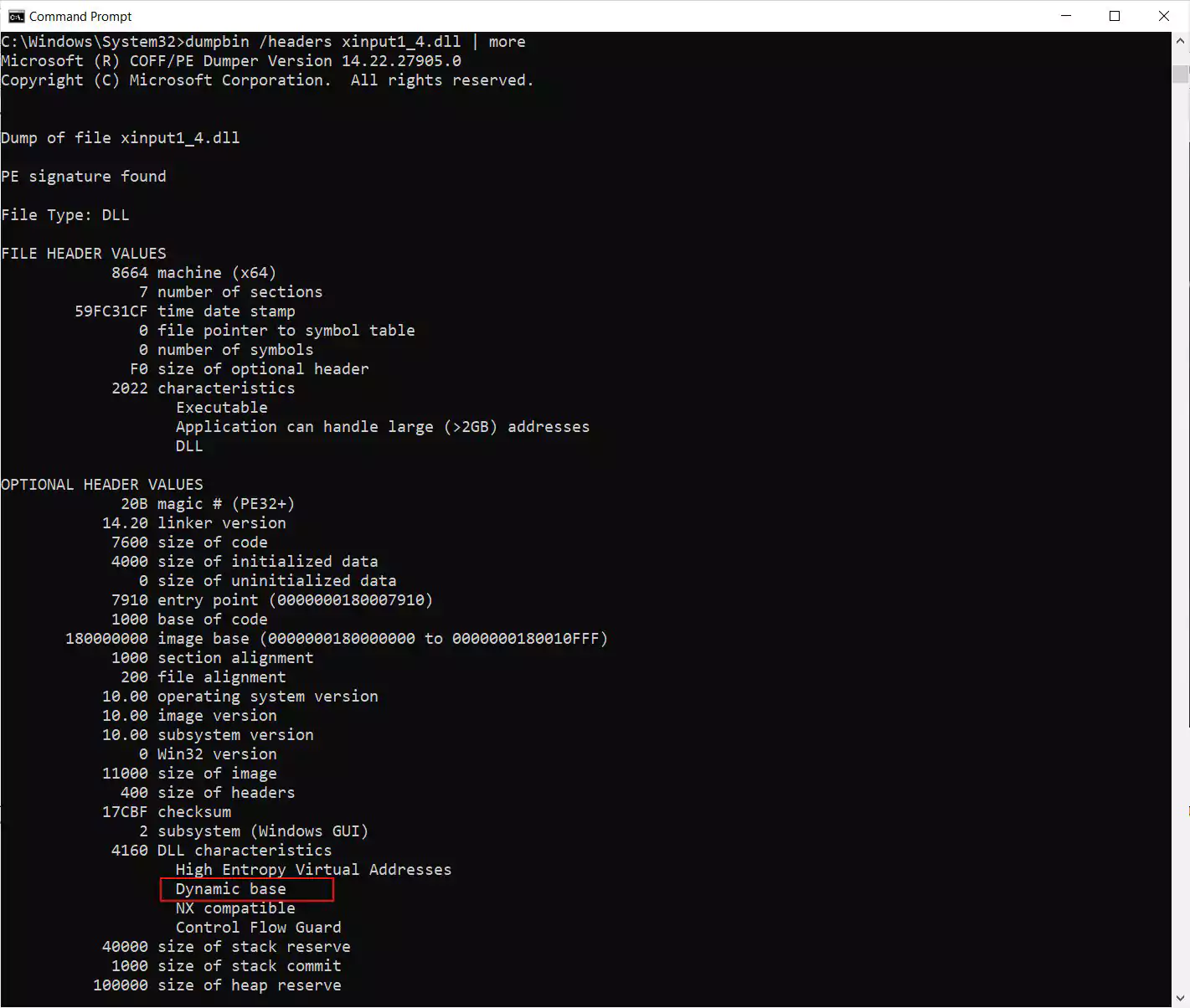
With this hotfix installed, the vulnerable xinput1_3.dll DLL file has been removed, and the Cyberpunk2077.exe executable now loads the ASLR-enabled C:\Windows\System32\xinput1_4.dll file bundled with Windows 10.
The ASLR feature is shown to be enabled in the xinput1_4.dll file by the ‘dynamic base’ characteristic displayed using the ‘dumpbin.exe /headers’ command, as shown below.
If you are currently launching Cyberpunk 2077 outside of Steam or using a mod manager, it is strongly advised to update the game first within Steam before playing it.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
The patch is tiny and only takes a few seconds to install.