





A botnet known as DarkIRC is actively targeting thousands of exposed Oracle WebLogic servers in attacks designed to exploit the CVE-2020-14882 remote code execution (RCE) vulnerability fixed by Oracle two months ago.
Almost 3,000 Oracle WebLogic servers are reachable over the Internet based on Shodan stats and allow unauthenticated attackers to execute remote code on targeted servers according to a Juniper Threat Labs report.
While attackers are currently targeting potentially vulnerable WebLogic servers using at least five different payloads, the most interesting is the DarkIRC malware “currently being sold on hack forums for $75.”
The threat actor selling the DarkIRC botnet on Hack Forums goes by the name of Freak_OG and started advertising it beginning with August 2020.
Juniper Threat Labs didn’t say that this threat actor is behind the ongoing DarkICE attacks even though the filename of one of the recently detected payloads is similar to a FUD (Fully Undetected) Crypter filename also advertised by Freak_OG earlier this month.
“We are not certain if the bot operator who attacked our honeypot is the same person who is advertising this malware in Hack Forums or one of his/her customers,” the report reads.
Also Read: PDPA Breach Penalty Singapore: How Can Businesses Prevent
DarkIRC is delivered on unpatched servers using a PowerShell script executed via an HTTP GET request in the form of a malicious binary that comes with both anti-analysis and anti-sandbox capabilities.
Before unpacking the final malware, it will first check if it’s running in a VMware, VirtualBox, VBox, QEMU, or Xen virtual machine and stop the infection process if it detects a sandbox environment.
Once unpacked, the DarkIRC bot will install itself in %APPDATA%\Chrome\Chrome.exe and will gain persistence on the compromised device by creating an autorun entry.
DarkIRC comes with a multitude of capabilities including but not limited to keylogging, downloading files and executing commands on the infected server, credential stealing, spreading to other devices via MSSQL and RDP (brute force), SMB, or USB, as well as launching several versions of DDoS attacks.
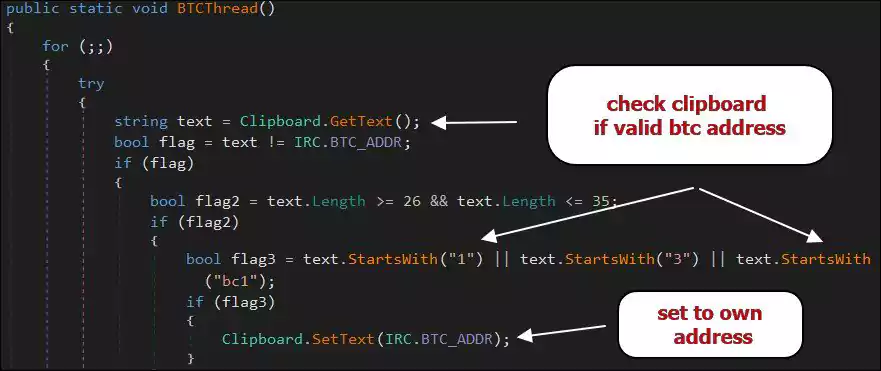
Attackers can also use the bot as a Bitcoin clipper that allows them to change bitcoin wallet addresses copied to the clipboard to one controlled by its operators in real-time.
One week after Oracle patched the vulnerability, threat actors started hunting for exposed Oracle WebLogic instances and checking if they are vulnerable to exploitation.
Last month, attackers also targeted Oracle WebLogic servers vulnerable to CVE-2020-14882 exploits to deploy Cobalt Strike beacons that allow for persistent remote access to compromised servers for harvesting information and deploying second stage malware payloads.
“Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans,” the Cisco Talos Incident Response (CTIR) team revealed in a September report.
Also Read: Data Protection Authority GDPR: Everything You Need To Know
These ongoing attacks are not surprising given how trivial it is to exploit CVE-2020-14882, its critical severity rating, and the fact that that exploit code is publicly available.
“It is remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password,” Oracle explained in a security advisory issued on November 2nd after releasing an out-of-band security update to address a bypass.
Oracle also provides WebLogic Server hardening instructions and CISA urged admins to apply the security update to block incoming attacks.