KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Newly discovered critical vulnerabilities in the Exim mail transfer agent (MTA) software allow unauthenticated remote attackers to execute arbitrary code and gain root privilege on mail servers with default or common configurations.
The security flaws (10 remotely exploitable and 11 locally) found and reported by the Qualys Research Team are collectively known a 21Nails.
All versions released before Exim 4.94.2 are vulnerable to attacks attempting to exploit the 21Nails vulnerabilities.
“Some of the vulnerabilities can be chained together to obtain a full remote unauthenticated code execution and gain root privileges on the Exim Server,” as Qualys senior Manager Bharat Jogi noted.
“One of the vulnerabilities discovered by the Qualys Research Team (CVE-2020-28017) affects all versions of Exim going back all the way to 2004 (going back to the beginning of its Git history 17 years ago).”
A list of all 21Nails vulnerabilities discovered by Qualys is available in the table embedded below.
| CVE | Description | Type |
|---|---|---|
| CVE-2020-28007 | Link attack in Exim’s log directory | Local |
| CVE-2020-28008 | Assorted attacks in Exim’s spool directory | Local |
| CVE-2020-28014 | Arbitrary file creation and clobbering | Local |
| CVE-2021-27216 | Arbitrary file deletion | Local |
| CVE-2020-28011 | Heap buffer overflow in queue_run() | Local |
| CVE-2020-28010 | Heap out-of-bounds write in main() | Local |
| CVE-2020-28013 | Heap buffer overflow in parse_fix_phrase() | Local |
| CVE-2020-28016 | Heap out-of-bounds write in parse_fix_phrase() | Local |
| CVE-2020-28015 | New-line injection into spool header file (local) | Local |
| CVE-2020-28012 | Missing close-on-exec flag for privileged pipe | Local |
| CVE-2020-28009 | Integer overflow in get_stdinput() | Local |
| CVE-2020-28017 | Integer overflow in receive_add_recipient() | Remote |
| CVE-2020-28020 | Integer overflow in receive_msg() | Remote |
| CVE-2020-28023 | Out-of-bounds read in smtp_setup_msg() | Remote |
| CVE-2020-28021 | New-line injection into spool header file (remote) | Remote |
| CVE-2020-28022 | Heap out-of-bounds read and write in extract_option() | Remote |
| CVE-2020-28026 | Line truncation and injection in spool_read_header() | Remote |
| CVE-2020-28019 | Failure to reset function pointer after BDAT error | Remote |
| CVE-2020-28024 | Heap buffer underflow in smtp_ungetc() | Remote |
| CVE-2020-28018 | Use-after-free in tls-openssl.c | Remote |
| CVE-2020-28025 | Heap out-of-bounds read in pdkim_finish_bodyhash() | Remote |
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
MTA servers such as Exim are an easy target to attacks given that, in most cases, they are reachable over the Internet and provide attackers with a simple entry point into a target’s network.
“Once exploited, they could modify sensitive email settings on the mail servers, allow adversaries to create new accounts on the target mail servers,” Qualys explained.
Microsoft warned in June 2019 about an active Linux worm targeting the CVE-2019-10149 Exim RCE bug, saying that Azure servers could be hacked by abusing the flaw although existing mitigations could block the malware’s worm functionality.
One month later, attackers started exploiting vulnerable Exim servers to install the Watchbog Linux trojan to add them to a Monero cryptomining botnet.
Last but not least, the National Security Agency (NSA) said in May 2020 that the Sandworm Russian military hackers have been exploiting the critical CVE-2019-10149 (The Return of the WIZard) Exim flaw since at least August 2019.
Exim is the default MTA on Debian Linux distros and currently the world’s most popular MTA, according to a mail server survey from May 1st, 2021.
According to the survey, it is installed on more than 59% out of a total of 1,084,800 mail servers reachable on the Internet, representing just over 344,026 Exim servers.
However, a BinaryEdge search found over 3,564,945 Exim mail servers running vulnerable versions exposed to attack over the Internet.
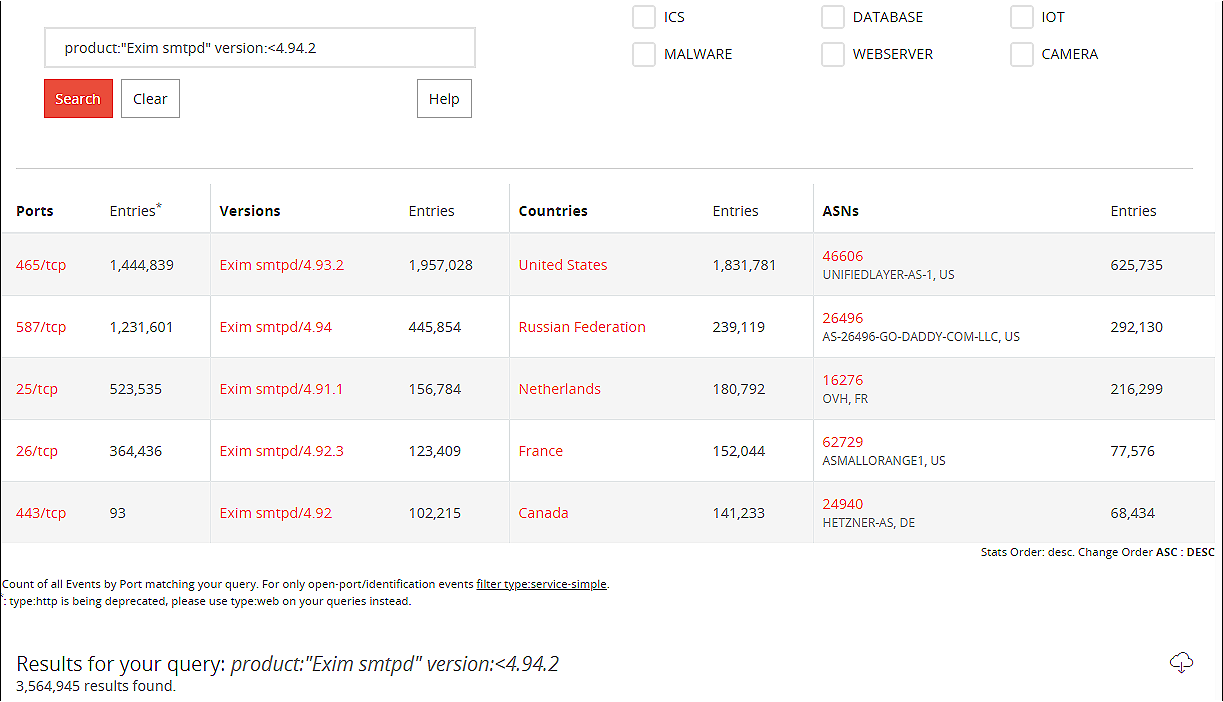
If not patched as soon as possible, all these servers could fall victim to incoming remote command execution attacks if not urgently patched against the 21Nails vulnerabilities.
Therefore, all Exim users should immediately upgrade to the latest available Exim version to block any incoming attack targeting their vulnerable servers.
If you have to upgrade from an Exim version older than 4.94, you will also need to rework your server configuration due to issues with *tainted data*, according to Exim developer Heiko Schlittermann. “This is a security measure which we introduced with 4.94,” he said.
“Alternatively you can use the exim-4.94.2+taintwarn branch. This branch tracks exim-4.94.2+fixes and adds a new main config option (the option is deprecated already today and will be ignored in a future release of Exim): ‘allow_insecure_tainted_data’.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
“This option allows you to turn the taint errors into warnings. (Debian is set to include this “taintwarn” patch in its Exim 4.94.2 release).”
More technical details on each of the 21Nail vulnerabilities is available in Qualys’ security advisory.
Update: Added info on ‘tainted data’ upgrade issues.