KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Conti ransomware gang is hacking into Microsoft Exchange servers and breaching corporate networks using recently disclosed ProxyShell vulnerability exploits.
ProxyShell is the name of an exploit utilizing three chained Microsoft Exchange vulnerabilities (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) that allow unauthenticated, remote code execution on unpatched vulnerable servers.
These three vulnerabilities were discovered by Devcore’s Orange Tsai, who used them as part of the Pwn2Own 2021 hacking contest.
While Microsoft fully patched these vulnerabilities in May 2021, technical details regarding exploiting the vulnerabilities were recently released, allowing threat actors to start using them in attacks.
So far, we have seen threat actors using the ProxyShell vulnerabilities to drop webshells, backdoors, and to deploy the LockFile ransomware.
Also Read: 12 Benefits of Data Protection for Business Success
Last week, Sophos was involved in an incident response case where the Conti ransomware gang encrypted a customer.
After analyzing the attack, Sophos discovered that the threat actors initially compromised the network using the recently disclosed Microsoft Exchange ProxyShell vulnerabilities.
Like most recent Microsoft Exchange attacks, the threat actors first drop web shells used to execute commands, download software, and further compromise the server.
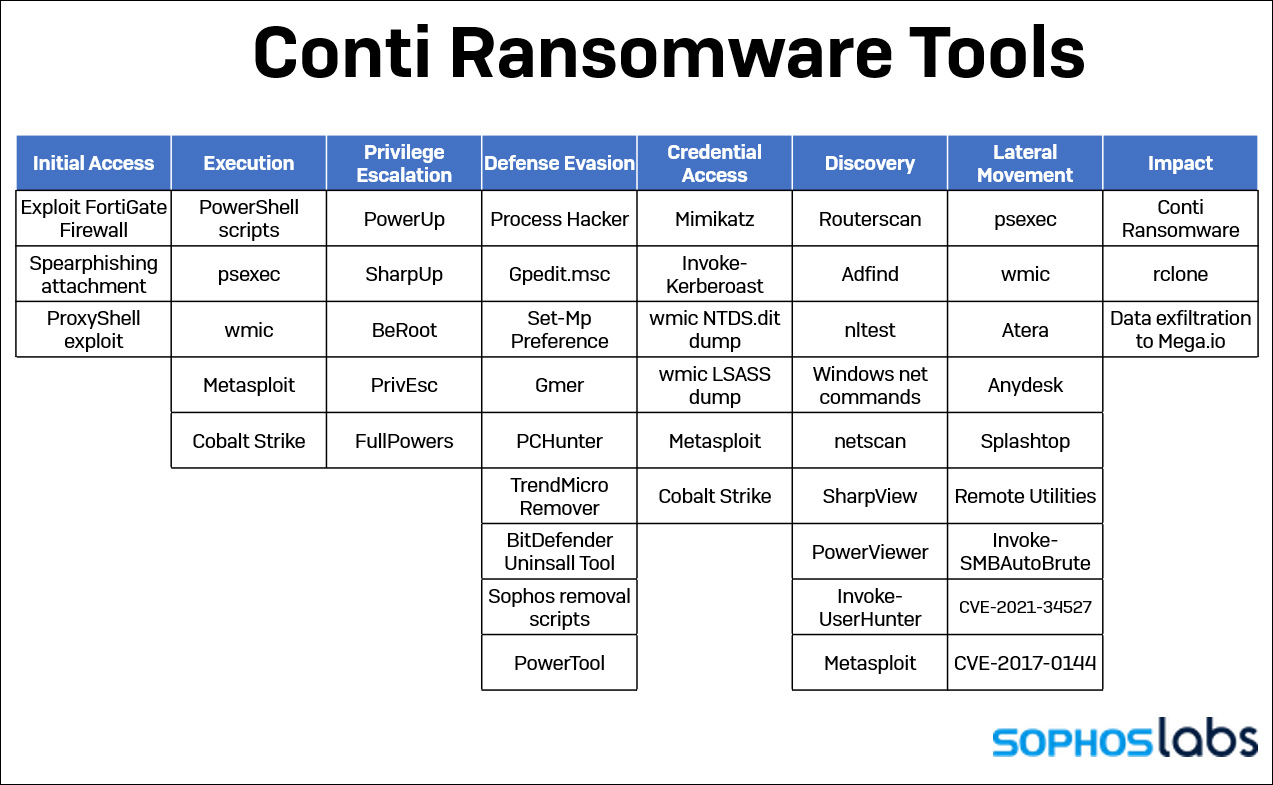
Once the threat actors gain complete control of the server, Sophos observed them quickly falling into their standard tactics as outlined in the recently leaked Conti training material.
This routine includes getting lists of domain admins and computers, dumping LSASS to gain access to administrator credentials, and spreading laterally throughout the network to other servers.
As the threat actors compromised various servers, they would install multiple tools to provide remote access to the devices, such as AnyDesk and Cobalt Strike beacons.
After gaining a foothold on the network, the threat actors stole unencrypted data and uploaded it to the MEGA file sharing server. After five days, they began encrypting devices on the network from a server with no antivirus protection using the observed command:
start C:\x64.exe -m -net -size 10 -nomutex -p \\[computer Active Directory name]\C$What made this particular case stand out was the speed and precision the group conducted the attack, where it only took 48 hours from the initial breach to stealing 1 TB of data.
“Within 48 hours of gaining that initial access, the attackers had exfiltrated about 1 Terabyte of data. After five days had passed, they deployed the Conti ransomware to every machine on the network, specifically targeting individual network shares on each computer,” explained Sophos in their report.
“Over the course of the intrusion, the Conti affiliates installed no fewer than seven back doors on the network: two web shells, Cobalt Strike, and four commercial remote access tools (AnyDesk, Atera, Splashtop and Remote Utilities).”
“The web shells, installed early on, were used mainly for initial access; Cobalt Strike and Any Desk were the primary tools they used for the remainder of the attack”
Also Read: Privacy policy template important tips for your business
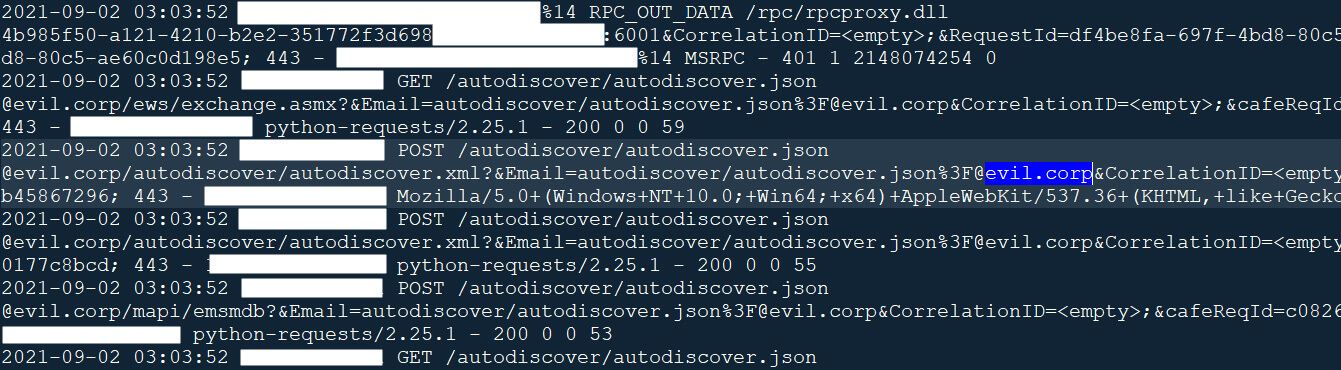
When conducting attacks using ProxyShell, the threat actors target the autodiscover service by making requests like the following:
https://Exchange-server/autodiscover/[email protected]/mapi/nspi/?&Email=autodiscover/autodiscover.json%[email protected]To check if your Exchange Server has been targeted, you can examine IIS logs for requests to “/autodiscover/autodiscover.json” with strange or unknown emails.
In the Conti case observed by the Sophos, the threat actors utilized an email from @evil.corp, which should easily make the exploit attempts stand out.
Without a doubt, the ProxyShell vulnerabilities are being used by a wide range of threat actors at this time, and all Microsoft Exchange server admins need to apply the most recent cumulative updates to stay protected.
Unfortunately, this will mean mail downtime as the updates are installed. However, this is far better than the downtime and expenses that a successful ransom attack will incur.